The Zionist Death Grip On The United States Government Greg Reese | Infowars.com April 30th…
Organized Gang Stalking, Electronic Harassment, and Psychotronic Tortures (Part 3 From “Mind Control Slave”)
Mind Control & Cults
Articles & Interviews
Part VI: Mind Control: History and Applications
April 5, 2025Part VII: Electronic Mind Control and Electronic Weapons
March 13, 2025Part VIII: Cult Connections
March 12, 2025Appendix 7: Human Experimentation in America
January 23, 2025Books and pdfs by Dr. Robert Duncan, ex-CIA neuroscientist
October 7, 2024“PsyWar: Enforcing the New World Order:” Dr. Robert Malone Lecture
September 17, 2024Appendix 42. Psychological Operations Blueprint (by Omnisense)
February 19, 2024Appendix 63: NASA’s Project Blue Beam by Serge Monast- 1994
December 2, 2023The Intra-Body Nano-Network Compilation (Sept. 5, 2023 video)
October 27, 2023Cognitive Warfare June-November, 2020 Francois du Cluzel
March 16, 2023Appendix 148: Kabbalah, Satanic Jewish Black Magic, & Freemasonry
December 9, 2022Appendix 152. Torturedinamerica.org. Excellent website!
November 30, 2022Appendix 220. (Nazi) Vril Maidens (2 articles)
January 19, 2022Appendix 224. Professor Ian F. Akyildiz videos on Biodigital Convergence
December 20, 2021Appendix 227: Masonic-Jewish Murder Ritual on Video
October 12, 2021Appendix 234: Maurice Strong and Tavistock (video)
August 19, 2021Quora Q & A On Gangstalking
March 14, 2021Elisa E. (“Our Life Beyond MKULTRA”): 5 Interviews
February 15, 2021The MANY Methods of Mind Manipulation . . . a Worldwide Operation
October 22, 2020Digital Twins, Digital Immortality, and Targeted Individuals
September 19, 2020MKULTRA and Operation Paperclip youtube
January 4, 2019MKULTRA Survivors Speak (youtube and article)
November 18, 2018Anthony C. Sutton: Psychotronic Weapons and Behavior Modification
November 16, 2018Truth In Quotes and Images: Freedom Fighters Help Yourselves
January 5, 2018Psychopolitics: Jewish-Communist Brainwashing Techniques (Kenneth Goff)
December 19, 2017Military Amok: Army Deploys Psy-Ops on U.S. Senators
October 2, 2017USAF Squadrons & Satellite Weapons
June 19, 2017How To Stop Electronic Torture!
December 5, 2016“NSA Mind Control and Psyops” by Will Filer
December 5, 2016Las Vegas “shooting”… Just Another Staged, False-Flag Event?
October 31, 2016Total Individual Control Technology (by Omnisense)
February 17, 2016THE SILENT MASSACRE: ELECTRONIC STALKING AND MIND CONTROL
December 2, 2015The Invisible War: 21st Century Targeting (youtube)
November 14, 2015‘The NSA – Citadel Of Evil’ by Steve Smith
October 27, 2015Dr. Stan Monteith, Author
February 25, 2014Dr. Eric Karlstrom on Sandy Hook / Mind Control
February 25, 2014Dr. Eric Karlstrom
February 25, 2014Social Engineering 101: Silent Weapons for Quiet Wars (Against Humanity)
February 25, 2014Organized Gang Stalking Quotes
February 23, 2014I. Organized Gang Stalking; An Aggressive Campaign That Will Astound You by DT Stockton
Organized Gang Stalking, Electronic Harassment, Psychotronic Tortures by DT Stockton
What you are about to read will seem paranoid and crazy. What is crazy is that all this information is true and there is a trail of evidence that proves these facts. As you read, you will learn of acts of terrorism and acts of treason being perpetrated against the American people and people around the world by the Intelligence Agencies of many countries. These acts include, but are not limited, to “gang-stalking”–systematic attempts to drive a target crazy (i.e. “gas lighting”) and/or attempts to drive a target to murder and/or suicide. It is a campaign that will astound you.
In my investigations, I have discovered that the intelligence agencies not only from the United States, but also from the following countries are involved: Canada, England, Great Britain, France, Germany, Australia, India, Pakistan, Israel, Poland, Czechoslovakia, Jamaica, the Philippines and possibly, Japan, Ireland, Africa, Italy, Monaco, Venezuela, Mexico, Guatemala, El Salvador, China; however, keep in mind that there is a strong possibility that others are also involved. This is being conducted worldwide under the Echelon Project.
These agencies are forcing people–homeless and runaway children, homeless adults and mentally and physically-challenged persons, released from institutions under the Reagan-Bush presidencies–through these illegal acts, to become government-controlled informants, and implanting a device called a “burst bug” in their ear. These controlled informants are the people conducting unscrupulous activities, which include gang-stalking, assault, murder, identity theft, break-ins, robberies and the sabotage of automobiles, electronics, especially computers, etc. They are pushing people to commit homicide and suicide. They are also being used to falsely accuse targets of crimes such as child molestation, rape and white collar crimes, framing them for these crimes and then lying in jury trials, etc. This has been the case with Martha Stewart, Michael Jackson and Dan Rather, to name just a few. Many of these controlled informants are also convicted murderers, pedophiles, rapists, etc. The intelligence agencies hide their criminal records and many of them continue to commit the same offenses upon society, where the intelligence agencies turn a blind eye.
These crimes are also being conducted so that the Pentagon and the intelligence agencies can convince Congress, by manipulation, to pass legislation, such as the National Identification Card, the Patriot Act II and other bills which contain subsections which are not known to the general public and even the Congress. It is the Pentagon and the intelligence agencies including the military that are conducting these criminal acts and acts of terrorism so that they can pass the necessary legislation to eventually abolish the Constitution and all of our civil liberties and achieve the Military Industrial Complex, and, as former president George Herbert Walker Bush stated, the New World Order, which is a one-world government.
Through my investigations and by being a target myself of these informants, I have found that government-controlled informants in the African-American and Hispanic communities are 3 to 4 in 5. In the Middle Eastern and other foreign communities such as Indian, Pakistani, Asian, Africans, Jamaicans, Zimbabwean, etc., it seems much higher. I have found that 4 out of 5 are government-controlled informants and many times 5 out of 5. And in the overall U.S. population, including the white communities, these government-controlled informants are 1 in 5.
Many of these foreign individuals are often wanted criminals in their native country and other countries. They often have criminal records and outstanding warrants. And some have been military trained either in foreign countries or the U.S.
The burst-bug device is a tracking device and a listening device, which gives the controlled informant the amazing ability to hear at a super human level. Individuals with the burst-bug implant can hear the quietest whisper from across a room; it gives a deaf person the ability to hear. It permits the Pentagon and all other intelligence agencies to hear conversations in real time, which are digitally recorded. Through the burst-bug, the intelligence agencies are conducting voice analysis and voice recognition. The intelligence agencies are giving instructions, in real-time, on how to handle a target situation, or things to say to a targeted person. The government-controlled informants, who are gang-stalking the target will often repeat parts of what is said on a target’s phone conversation from illegal phone taps. This lets the target know that they are being both watched and monitored. This method makes a target feel paranoid or think they are crazy. The use of this device in this manner is also used in courtroom circumstances, guiding the informant on what to say in trials when they are on a witness stand.
I have discovered this burst bug in children as young as two years old and seniors as old as 86 years. The intelligence agencies are training these people to be terrorists and to be loyal only to them. With this manipulation comes a great deal of brainwashing and pure fear.
For those that want to dispute this, I have several family members and friends of twenty plus years who are forced to be government-controlled informants. I have been attempting to go public with this information for several years, so to get the terrorism against me, my family, friends and the many other targeted people to cease. And to restore freedom as we believe it to be. However, one of many problems that I have had has been that the intelligence agencies have damaged eight computers in an attempt to prevent this from occurring. I have hidden all evidence of this so to preserve it
All of these activities are conducted by the Intelligence Agencies under “The War on Drugs”, “The War on Crime” and “The War on Terror.” This is ironic considering that the intelligence agencies are the criminals and terrorists. The intelligence agencies have been illegally investigating Americans and businesses since 1980, through illegal wire taps, the bugging of homes/offices/ automobiles, the placing of tracking devices on vehicles, and whenever possible, on a target’s person, in items such as a watch or clothing, etc. They are also using GPS in cell phones to track their targets. They have been investigating financial records, often using their controlled informants to do these illegal activities. The premise under which they are conducting illegal activities is that we are all guilty of something. So with that as their starting point, they are launching investigations, violating all federal and state laws, all constitutional rights and all civil liberties. Their behavior and actions are as if we are their property, and they will do with us as they so choose.
The War on Drugs is the cover that the Pentagon uses, through the CIA, to take over all aspects of the illegal drug business, from growing and manufacturing, to importing/exporting, to sales. At least 99% of all illegal drug growers/manufacturers and dealers are government-controlled informants with the burst-bug.
The burst-bug operates at various frequencies, hence the word “burst.” The frequency range for this device can go as high as 22GHz, and because it is government standard, can go above 22GHz, possibly 24GHZ and higher. This device is most often detectable with detection equipment called OSCOR, which stands for Enhanced Omni-Spectral Correlator, with the 21GHz down converter. However, because of their constant surveillance of me with illegal phone taps, listening device bugs and the sabotage of my computers, they have full knowledge that I am going public with this information; therefore the frequency is expected to be kept at an above 22GHz level for the present.
For those being gang-stalked, the burst-bug implant in informants is how they are able to have precise timing accosting targets unexpectedly. They have this down to a science. Keep in mind they have hundreds of billions of taxpayers’ dollars at their disposal. And their budgets have been increasing under these bogus wars for the past 30 years. This will assist you in your ability to prove what is occurring. Gather the evidence against these individuals and intelligence agencies, and it will give you the power to both fight back and to sue under many federal laws including but not limited to The Patriot Act. Keep in mind that both these informants and the intelligence agencies are defined as terrorists under the Patriot Act and other federal laws. This is where The Patriot Act is a double–edge sword. Moreover, they are guilty of treason under our Constitution.
Another fact, according to an individual who did work for the CIA under the War on Drugs and several informants who have put their lives on the line to tell me information, is that there is No Paper Trail!
They are using these acts of terrorism and acts of treason to achieve the Total Military Industrial Complex. President Eisenhower warned us about this in his last speech before leaving office.
Because of their constant terrorism against me dating to 1986, as well as their terrorism against my family, friends and anyone connected to me, I have had to turn the tables and investigate them. And because the intelligence agencies are fully aware of my knowledge, they have launched a campaign to destroy my credibility, which simply will not work. What you are reading is a miniscule drop in the bucket.
And now I need your help in exposing these murdering terrorists and to seek justice under our laws. Investigate for yourselves. You will understand that this is the truth. And when you come to realize the terrorism, the treason, the murder, it will shock you, scare you and anger you. So, whatever it takes, gather the resources you need to fight and expose this betrayal to the American people and the illegal use of our tax dollars against us in such a horrendous manner.
For those of you that live with rose-colored glasses, and have a difficult time accepting truth and reality—grow up! It is time to face adulthood, to face the realities of life and deal with life as it is. And only together can we fight this evil. All laws are in our favor.
Furthermore, if what is stated here is not true then explain why at minimum 90% of all businesses and corporations across this country, and I presume across the world, are owned and controlled by government-controlled informants, giving the Pentagon, FBI, CIA, the NSA and the Military just several years to achieve the Total Military Industrial Complex. The following businesses are just a small example. You will find that all are owned by government-controlled informants and that most, if not all, of the employees are also government-controlled informants, and all are controlled by the intelligence agencies. The intelligence agencies tell them who to hire and who to fire, how much to pay and how many hours to employ them. Every facet is dictated. These controlled informants have been and are still perpetrators in gang-stalking and all other forms of terrorism and acts of treason against this country and its citizens. They get jobs after the intelligence agencies deem that they have earned it and they must continue to earn it. These acts of terrorism are also perpetrated against them by other controlled informants, which is a psychological warfare tactic used to control them. It keeps them living in fear.
The burst-bug links all and the digital recordings will prove everything. Evidence shows us the truth.
The following information is not bashing foreigners. In my investigations I have found that most, if not all foreigners who have entered this country since 1980, to gain an education and/or work and reside in this country are government-controlled informants. Keep in mind these people do not understand our way of life and our foundation under the Constitution. They simply have no respect for us Americans and our country. They are betraying us right under our noses and are truly enjoying it. As these people gang stalk me, I see the glee in their eyes and the smirk on their faces. It is my belief that they really enjoy the fact that they are taking our money and committing terrorism and acts of treason against us. When doing business with these controlled informants, we are empowering them with our money. They have been taking our jobs and businesses and betraying the American people with acts of terrorism and acts of treason.
Under the Patriot Act government-controlled informants are terrorists, who have no rights to own or possess property, businesses nor do they have a right to the custody of their children.
Jobs which are being exported to places like India, etc. are their reward for the domestic spying, domestic terrorism (i.e. gang-stalking), which they are conducting while in the United States and other countries.
Operation TIPS has been illegally in place under these methods for several decades.
Many companies and corporations have been taken over illegally by the intelligence agencies right under the noses of the masses and politicians.
All United States Postal, UPS, Fed Ex, DHL, and many courier service companies and employees, that I have met and observed, are government-controlled informants. All postal employees are guaranteed job security for life, so for the intelligence agencies to take over the postal service, they had to place a few of their controlled informants in position so that they could gang-stalk the others who were not under their control. With these tactics they drove some to the breaking point and they snapped, hence “going postal.” The intelligence agencies and their controlled informants committed plain and simple, acts of terrorism.
All doormen, maintenance workers, superintendents, management companies, which I have investigated and observed in the past several years are government-controlled informants involved in these unscrupulous and illegal activities. I have also found this to be true with airline and airport employees. Jet Blue is a prime example of what I state here. It is my strong belief that the Founder and ex-CEO David Neeleman is a government-controlled informant.
Several other companies and corporations are Con Edison and Time Warner Cable from executives to repair personnel; Amtrak, MTA, PATH, bus drivers, etc. from administrative personnel to train crews to track repair; Parks Departments throughout this country, from executive personnel to maintenance personnel. And Trash Removal Companies, such as Waste Management are another. This continues to occur throughout this country. Parking lot and garage companies and corporations have also fallen prey to these actions. Many security guards and security companies, home security companies are also controlled under the intelligence agencies.
Charity organizations such as The Salvation Army, Goodwill, Volunteers of America and Gods Love We Deliver, from administration personnel to thrift store employees, are another small example.
Political organizations such as the American Civil Liberties Union are being sabotaged from within. It is my belief that Anthony Romero is a government-controlled informant.
All libraries from public, private and universities etc. have been taken over with controlled informants in positions such as security, administration and other aspects of duties. This is how they have been illegally censoring books from their collections. This is how they have been monitoring targeted persons’ reading interests and other behavior such as computer usage and history. All computers have spy ware linked to the intelligence agencies. They also have the ability to take over and control these computers by closing programs and other such activity. I have witnessed this first hand.
All professional fields have been infiltrated and often taken over by the intelligence agencies using their controlled informants, such as, hospital workers, physicians, therapists, psychiatrists, ministers, prosecutors, public defenders, judges, police, firefighters, attorneys, paramedics and several politicians and lobbyists, etc.
Police departments have many infiltrators in them. Many are foreigners, as well as Americans, who are betraying the confidence and trust of their fellow officers. They are intentionally attempting to setup and often frame their fellow officers for crimes so that the feds can force them to become a government-controlled informant. This is the secret and treasonous building of the military-police-state.
Students at universities, colleges and trade schools are being targeted. Some are being recruited to be government informants under the guise of doing the right thing for the country to end crimes such as rape, murder and drug use. After spending the past several decades stiffening the penalties, for drug use/possession and other crimes, the intelligence agencies have utilized these penalties through their government-controlled informants to setup and often frame individuals for such crimes. Since college is where young adults start to experiment, the intelligence agencies are forcing them to become government-controlled informants by lying, scaring and terrorizing them. After 27 years of recruiting among college students, these adults are now career professionals.
There are systematic methods used to put businesses out of business and sabotaging businesses from within. One such method is that a government-controlled informant will purchase a building and over inflate the rent so that the existing business cannot afford the large rent increase which drives the business under. Then they lower the rent to something more reasonable for the controlled informant that rents that same space. Another method used is to send a controlled informant building inspector to say that the building needs work and/or is unsafe and the need to put up scaffolding, and/or road construction is needed, which hurts/drives down business. They often take over manufacturing companies and raise the minimum purchase order requirement which is not within the ability of a small business to afford. Slander is another tactic. They will spread lies and rumors about a business or it owner(s). Often they will have controlled informants infiltrate a business, in positions such as cook, bartender, etc. and sabotage the business from within with tactics like bad service, etc.
Eminent Domain is another form of domestic terrorism utilized by the intelligence agencies. Investigate all parties involved including the developers and you will see that it is all linked to the Pentagon and the intelligence agencies. I further challenge anyone to prove this information to be untrue.
For those that are losing or about to lose their home from a foreclosure, this is the work of the Pentagon and the intelligence agencies. The intelligence agencies have illegally taken over all banks, and their government-controlled informants control and/or own many of the mortgage companies. The agenda is for all of us to live in housing which is controlled under the Military Industrial Complex. This is one of many steps they are taking to achieve the Military Industrial Complex, which is to own and control everything.
HAARP, EMP, Pulse and Direct Energy weapons, contrary to the propaganda and lies that the intelligence agencies and the military disclose to the public, are extremely lethal. These weapons are used to take down airplanes and terrorize a targeted person over a period of time. These weapons come in the form of vibrations, which can be used to target a specific organ in the body causing scar tissue to form leading to the death of that organ. These weapons can cause heart attacks and strokes. In my experience, there are approximately 100 plus vibrations that attack the heart. There are vibrations that cause panic attacks and sleep deprivation. There are vibrations which cause a targeted person to go mad and/or crazy, as well as many other capabilities. For various reasons not everyone can feel the vibrations from these weapons, as some people are more sensitive to smells than others and some people are more sensitive to sounds than others. However, a seismograph can record these vibrations, and will prove that they are real and unnatural in nature. And what can be proven is that HAARP, EMP, Pulse and Direct Energy weapons are in use, harmful and lethal. All controlled informants are aware of these weapons which, makes them complicit in these acts of terrorism and murder. Congress is also aware of these weapons and has failed to ban them. Refer to HR2977.
These weapons are being used at retirement communities, hospitals, schools, and many other places, killing people. All that would show up in an autopsy is that the person died from natural causes, only because the degree of scar tissue caused by the weapons is overlooked and often never questioned.
Anyone disputing what is stated here must be presumed to be a government-controlled informant. This is how the intelligence agencies spread disinformation. Keep in mind that the intelligence agencies have been able to keep this from the masses for the past 27 years by dismissing and discrediting others who have tried to come forward as “conspiracy theorists” and brainwashing the masses with the idea that anyone saying conspiracy is crazy. I am not a conspiracy theorist, nor criminal, nor terrorist. I only base my information on facts which I have gained through years of gathering evidence through my investigations and experiences. Evidence permits us to see the truth.
Another method used in domestic spying, since 1980, and utilized in individualized gang-stalking/terrorism is the use of helicopters. The NSA are using helicopters equipped with technology that most people will not believe exists. They are also using heat sensors, which the federal courts have deemed illegal to use in the privacy of our homes, to illegally spy on us. For those individuals that are being gang-stalked, in conjunction with their many other methods, this equipment is being used in conducting noise campaigns. They are using the heat sensors to know what part of your home you are in and notifying the controlled informant(s) which, may live above you or next to you know, as to where to make the noise. And they are also monitoring the illegal phone taps and bugging devices. These helicopters are also illegally tapping into our computers, often interfering with transmissions, attacking it with viruses and Trojans and slowing down the computer with all types of other attacks. They are also relays for the HAARP, EMP, Pulse and Direct Energy weapons. At night the NSA helicopters hover at 26,000 to 39,000 feet. On bad weather they are just above the clouds at 39,000 feet. To the naked eye they look like stars and some people have stated that they look like planets. However, with a telescope you can see that they are only between 26,000 and 39,000 feet and that they are not stars or planets. Not only are NSA helicopters being used in stalking and terrorizing targets, the FBI and local police use their helicopters to take an active role in these activities, for I have witnessed this first hand.
During the morning and all during the course of the day the military fly their spy planes over this entire country, including farm and rural towns and communities, breaking down our firewalls and breaking into our computers, including company and corporate computers, which have wireless capabilities. They are also installing spy ware through these wireless means. Microsoft’s Windows XP has three (3) back doors, which Microsoft will not discuss nor will they state as to why they are there. However, I believe I know why they are there; it is for this very purpose, so that the intelligence agencies can illegally spy on us and interfere and repress us Americans. I believe when the government went after Microsoft for unfair business practices, this was part of their settlement agreement with the Bush Administration.
It is my belief that because of the close monitoring of me and the intelligence agencies being fully aware that I am now going public with this information, they recently came forward about themselves and their illegal abuses of the Patriot Act with the illegal investigations into many Americans. However, they only told the smallest truth, the rest were lies. The number of persons investigated is in the millions not thousands and they have been doing this for many years prior to the Patriot Act. Not only is the FBI conducting such abuses, the intelligence agencies are far reaching, including the CIA, the NSA and the Pentagon. The IRS is also involved. When it comes to the requests for information from the libraries on a “person of interest,” they have been doing this verbally through the burst-bug, with no paper trail. It is my belief that the requests for information through paper protocol have been recently done to cover their tracks.
Politicians are also being targeted by illegal investigations and gang-stalking tactics. Senator Craig is a prime example. Also, many secretaries and receptionists of politicians are controlled informants who are spying on them, often blocking people and information such as deleting emails, voicemails and intercepting letters from getting to the politicians.
The Pentagon and the intelligence agencies have been illegally manipulating and interfering with elections in this country by using their controlled informants. All informants are controlled on every level including: if they vote and who they vote for, which is why many do not vote, unless they are told to do so. They have infiltrated all Presidential Candidates Campaigns and have been sabotaging them from the inside. I watched first hand the presidential election in Ohio being sabotaged by these government-controlled informants, at the voter registration offices, campaign offices and at the election polls. And I did collect names. These activities were also done against Grey Davis of California. I was first told in 2001 about what was going to happen to Grey Davis in 2003. Many of the persons who were involved in the proposition of the recall of Grey Davis were government-controlled informants led by the intelligence agencies. And what this has led me to believe is that these events are well orchestrated and planned years in advance regardless of what the majority of the people want. In the case of the Florida presidential election the Feds used their government-controlled informants who happen to be police officers to prevent many black voters from voting. I challenge anyone to investigate those police officers involved and you will find that they have the burst-bug implant.
Three last facts: One, all payphones, throughout this country, have been tapped since 1980. Two, the Pentagon is operating various conspiracy websites, one being www.911TruthOut.org, using their controlled informants. Three, on Sundays, they run the Truth Movement at St. Marks Episcopal Church, using their controlled informants. Now ask yourselves, why?
The terrorism is well orchestrated. The campaign against all Americans and this country from within will astound those who investigate further. It is simply insane how the intelligence agencies will stop at nothing to achieve their goal, which is “Total Control.”
Part of a series of articles published by Citizens Against Human Rights Abuse
Overt Harassment: Preconditioning for Electronic Harassment
Overt Harassment
Overt Harassment — which obviously is meant to be observed — may be intended to “precondition” individuals for eventual long-term electronic harassment. Persons terrified by unexplained overt harassment are not likely to cope with the sudden onset of electronic harassment in any more reasoned fashion. This phased pattern of harassment is apparent in all of the cases now being investigated. The fact that the overt harassment continues in these cases even after the electronic targeting commences suggest that the objective is to maintain long-term extremes of stress.
Many of the overt harassment tactics discussed below are surfacing in cases which (so far) have not involved discernible forms of electronic harassment. These are cases involving so-called “whistleblowers” who, because of their inside knowledge of certain potentially newsworthy events, pose particular threats of embarrassment to the Government or to government-affiliated employers. We have noticed that electronic harassment is beginning to surface as a form of retaliation against persons who try to assist electronic “harassees.” Retaliation suggests loss of control. Under these circumstances, we are not entirely confident that “whistleblowers” will continue to be exempted from this type of harassment in the long term.
The individuals now in touch with the Project describe their circumstances as involving most, if not all, of the following overt forms of harassment:
* Sudden, bizarrely-rude treatment, isolation and acts of harassment and vandalism by formerly friendly neighbors.
* Harassing telephone calls, which continue even after the targeted individual obtains new, unlisted telephone numbers.
* Mail interception, theft and tampering.
* Noise campaigns.
While unrelenting harassing telephone calls might be considered in this context, other tactics are employed. Blaring horns, whistles, sirens, garbage disposal (run concurrently in apartment settings, for excessively prolonged periods of time), and amplified transmissions of recorded “general racket” have been used on a recurrent basis under circumstances intended to persuade the individual that he or she is under surveillance.
In all of these cases, the individuals’ neighbors apparently pretend to be oblivious and/or indifferent to these sudden, continuous explosions of noise.
Door slamming is also a popular pastime, particularly in apartment buildings. One individual reported that, during a peak period of harassment, the neighbor across the hall began entering and leaving his apartment every 10 minutes, slamming his door loudly on each occasion. This was a daily occurrence, encompassing periods of several hours, over a period of several months. It is apparently served to trigger a door-slamming “chain reaction” on the part of neighbors both on that floor and on the floors immediately above and below. When our contact politely asked her immediate neighbor to close her door more quietly, he slammed the door in her face. Prior to commencement of this harassment, the neighbor had apparently been quite friendly and courteous.
In another case, the primary door-slammer is an employee of Radix Systems, Inc., Rockville, MD, a DOD contractor engaged in the “super-secret” research and development of some type of electronic equipment.
Several individuals reported recurrent, loud, strange noises in their ventilation systems during the preliminary stages of their harassment. One individual complained of being recurrently awakened in the middle of the night by the sound of wires being fed into his (independent) ventilation system. On checking further, he found that a tubular construction had been built into his vent system which appears to lead to the apartment upstairs. His upstairs neighbor is employed by the Department of Justice.
A number of individuals report that occupants of upstairs and downstairs apartments appear to follow them from room to room, tapping on the floor or engaging in other activities which appear intended to advertise an ongoing surveillance.
The Justice Department employee mentioned above went as far as to offer an unsolicited apology to her downstairs neighbor for an all- night “pacing about” in her bedroom (in the event he had happened to notice it). She claimed to be an insomniac. The pacing-about continued during her recent 36-hour absence from the area. When her contact politely alerted her to the fact that her apartment had apparently been entered during her absence, she told him, in effect, to mind his own business and then immediately complained to the building manager that he was stalking her.
She conveniently forgot to inform the building manager that she had assiduously “courted” this individual for several months, without success; and that she had been stealing his newspapers on a regular basis. (On one occasion, she handed him a week’s accumulation of those papers, claiming that they had been left outside the door of another apartment. Her reason for collecting and saving the newspapers which had not been delivered to her directly is unknown.)
* Recurrent confrontations by unusually hostile strangers; and comments by strangers which appear intended to evoke “paranoid” reactions.
In this context, we note that several individuals have reported confrontations with “homeless” people who, on closer examination, were found to be fastidiously clean, though garbed in offbeat fashion (wigs included). The same “eccentric” confronted two of the individuals in contact with us, at separate distant locations. He is reported as having feigned mental illness on both occasions, and as having apparently enjoyed creating a public scene.
* Entries into the individual’s residence, during late-night hours while he/she is sleeping, and/or during the day when the individual is elsewhere.
In virtually all such cases, the burglars leave evidence of their visits, such as relocating objects, or by committing petty and not- so=petty acts of vandalism. In two cases, the burglar’s “calling card” was to slaughter caged pets, leaving the mangled carcasses inside their locked cages.
In one case, the burglar stole several pieces of correspondence and left a packet of crack cocaine behind as a “calling card.” Our contact in this case — an individual who has no criminal record and no history of experimentation with drugs — is also being harassed (stalked) by a police officer of her community. One of his recent acts was to “frame” her with a drug possession charge. After pulling her off the road (a frequent pastime) and subjecting her to an illegal search (done, twice, so far), he conveniently managed to find a glassine packet of cocaine eight feet away, in front of his squad car. He retrieved the packet with his fingers and then charged her with Possession. Our contact found the packet of crack cocaine in her apartment shortly after this investigator reminded the attorney handling her case that the police officer had smudged his only piece of evidence with his own fingerprints. It would appear that someone is interested in correcting that police officer’s oversight.
In another case, the individual reports that a tremendous amount of money has been stolen from a hiding place in her apartment, within hours after she had withdrawn the money from her bank. There were no obvious signs of entry into her apartment. The police conducted a cursory inquiry which failed to produce evidence of a crime worthy of investigation. (This case is an anomaly. Money is usually not stolen. Documents appear to be the preferred objects of theft, when theft occurs.)
In another case, the burglars replaced installed light bulbs with “exploding” bulbs, many of which were ‘Made in Hungary.’ The light bulbs are now in our possession.
* Rapidly deteriorating health, generally of a digestive nature.
In two cases of the cases reported, massive rectal bleeding accompanied the sudden onset of sever gastrointestinal disturbances. One of these individuals abruptly terminated the deteriorative process simply by changing the locks on her door.
* Sleep disruption/deprivation
This is achieved by means of overt and electronic harassment. Sleep deprivation, as a tactic, invariably surfaces when the targeted individual begins exhibiting a strong emotional and irrational response to the other forms of harassment.
* Vandalism of privately-owned vehicles
Vehicles invite peculiarly ferocious attacks in these harassment campaigns — slashed tires, smashed windows, oil drainage, oil contamination, destruction of electronic components and batteries (frequently involving wildly fluctuating, grounded fuel gages, often within range of weapons research facilities and/or other microwave emitters); and suddenly failed brakes and clutches (possible involving anti-traction polymers, which are also in DOD’s “non-lethal” weapons arsenal). Recurrent auto thefts have also been reported.
Two individuals reported finding their oil contaminated immediately after having the oil changed by reputable mechanics. In one of these cases, the oil viscosified (thickened) while the individual was driving through a remote rural area. Her car ground to a halt. Getting the “gunk” cleaned out of her engine proved to be an expensive ordeal. (Viscosification agents are also lauded by the U.S. Global Strategy Council as serving “non-lethal” strategic purposes — a topic discussed in Part I of this publication. Had this woman been assaulted while awaiting help in the said isolated area, the “non-lethal” attributes of viscosfication agents might have required redefinition.)
Most of those who have experienced these attacks on a recurring basis have abandoned driving all together — an objective apparently sought by their tormentors as a means of increasing their isolation.
* Staged accidents.
The majority of those in touch with us have reported these types of experiences. One individual, for example, was tailgated at a high rate of speed by two vehicles, while concurrently being threatened with a gun by one of the vehicles’ occupants. Two others narrowly avoided what happened to be deliberately attempted collisions by drivers who quickly sped away from the scene. One avoided three attempts in four days at being run off the road. One survived by being run off the road in two incidents within a one-week period, which resulted in “totaling” of her two vehicles. Another narrowly avoided being crushed into an expressway retaining wall, on four occasions, by an off-duty metro bus, as well as, within the same time frame, being “fried” by two suddenly-malfunctioned household appliances which subsequently repaired themselves. It should be noted that, in some of these cases, “accidental” deaths do occur. One individual in contact with us reported that his mother drove off a cliff to her death, during a period when he was researching evidence that a still-respected, high level State Department official had passed A-bomb secrets to the Soviet Government during World War II. The accident occurred shortly after her car had undergone routine maintenance. She was returning from a dental appointment when the accident occurred. Witnesses state that it appeared that she had suddenly stepped on the accelerator before running off the road. The accident served to terminate this person’s research project.
We also look into the recent death of a woman in Lexington, MO, who was killed when the brakes on her tractor failed. We are informed that she had been collecting affidavits from persons who believe they are the targets of government harassment and experimentation when her “accident” occurred. We are also informed that these affidavits have disappeared.
Suicides might also qualify as “staged accidents,” particularly where “plausibly deniable” government involvement has been surfaced. We are currently looking into the recent suicide of a man in Trappe, PA, who, as early as 1981, had asked the FBI and CIA to intervene in his case. We have copies of that early correspondence. The man, a former U.S. Army radar technician, had a highly technical and — given date of his correspondence — “precocious” grasp of the experimental objectives apparently being sought in his case. It is apparent from his correspondence that he had wanted to believe that the Soviets were conducting these experiments. The FBI and CIA, of course, did not intervene. We are informed that members of his family have also been targets of this experimentation.
* Isolation of the individual from members of his/her family — virtually assured when highly focused forms of electronic harassment commence.
The exception to this is when elderly parents and young children in the family become targets for apparent purposes of intimidation. This situation has been reported in eight of our cases, to date.
One individual (driven to extremes of stress by ongoing electronic harassment focusing on her children) killed one child in an effort to protect her from further pain. (2) It appears that lasers were being used in this individual’s case. The targeting intensified after she called the Soviet Embassy to report the harassment, which she believed to be U.S. Government-sponsored. It became even more deadly when, in a further show of defiance, she then called the representative of the Iraqi Government to portray the U.S. Government’s war in the Middle East as “hypocritical.” She is now hospitalized in a Midwestern facility, where, apparently, the experimentation is now continuing.
(That psychiatric facility is in a State where a disproportionate number of complaints of electronic harassment are beginning to surface. It is also within range of a U.S. Air Force base which houses a “super secret” research facility. We are currently looking into information that spouses and children of persons employed on that USAF base may be the targets of involuntary experimentation involving direct-energy weapons technologies.)
Another individual, during a telephone conversation, was told by an employee of a local power company that, if she valued the lives of her children, she would drop her public opposition to the company’s installation of high power lines. Since receiving that threat, the individual’s 11-year-old daughter has been reduced to extremes of pain, resulting in her recurrent hospitalization for treatment of illnesses which cannot be diagnosed. It is also apparent to this individual that her three-year-old son is on the receiving end of externally-induced auditory input. (DOE figures prominently in this case.)
* Progressive financial impoverishment, brought on by termination of the individual’s employment, and compounded by expenses associated with the harassment.
The majority of those now in contact with the Project — educated, white-collar professionals — have lost their jobs. Termination of employment in many of these cases involved prefatory harassment by the employer and co-workers, which coincided with the other overt forms of harassment discussed above.
The overt harassment tactics are being described as recurrent, non- sequential and overlapping. As noted above, the overt harassment continues even after the electronic harassment commences.
[B]HR 2977 IH
107th CONGRESS
1st Session [/B]
H. R. 2977
To preserve the cooperative, peaceful uses of space for the benefit of all humankind by permanently prohibiting the basing of weapons in space by the United States, and to require the President to take action to adopt and implement a world treaty banning space-based weapons.
IN THE HOUSE OF REPRESENTATIVES
October 2, 2001
Mr. KUCINICH introduced the following bill; which was referred to the Committee on Science, and in addition to the Committees on Armed Services, and International Relations, for a period to be subsequently determined by the Speaker, in each case for consideration of such provisions as fall within the jurisdiction of the committee concerned
________________________________________
A BILL
To preserve the cooperative, peaceful uses of space for the benefit of all humankind by permanently prohibiting the basing of weapons in space by the United States, and to require the President to take action to adopt and implement a world treaty banning space-based weapons.
Be it enacted by the Senate and House of Representatives of the United States of America in Congress assembled,
SECTION 1. SHORT TITLE.
This Act may be cited as the `Space Preservation Act of 2001′.
SEC. 2. REAFFIRMATION OF POLICY ON THE PRESERVATION OF PEACE IN SPACE.
Congress reaffirms the policy expressed in section 102(a) of the National Aeronautics and Space Act of 1958 (42 U.S.C. 2451(a)), stating that it `is the policy of the United States that activities in space should be devoted to peaceful purposes for the benefit of all mankind.’.
SEC. 3. PERMANENT BAN ON BASING OF WEAPONS IN SPACE.
The President shall–
(1) implement a permanent ban on space-based weapons of the United States and remove from space any existing space-based weapons of the United States; and
(2) immediately order the permanent termination of research and development, testing, manufacturing, production, and deployment of all space-based weapons of the United States and their components.
SEC. 4. WORLD AGREEMENT BANNING SPACE-BASED WEAPONS.
The President shall direct the United States representatives to the United Nations and other international organizations to immediately work toward negotiating, adopting, and implementing a world agreement banning space-based weapons.
SEC. 5. REPORT.
The President shall submit to Congress not later than 90 days after the date of the enactment of this Act, and every 90 days thereafter, a report on–
(1) the implementation of the permanent ban on space-based weapons required by section 3; and
(2) progress toward negotiating, adopting, and implementing the agreement described in section 4.
SEC. 6. NON SPACE-BASED WEAPONS ACTIVITIES.
Nothing in this Act may be construed as prohibiting the use of funds for–
(1) space exploration;
(2) space research and development;
(3) testing, manufacturing, or production that is not related to space-based weapons or systems; or
(4) civil, commercial, or defense activities (including communications, navigation, surveillance, reconnaissance, early warning, or remote sensing) that are not related to space-based weapons or systems.
SEC. 7. DEFINITIONS.
In this Act:
(1) The term `space’ means all space extending upward from an altitude greater than 60 kilometers above the surface of the earth and any celestial body in such space.
(2)(A) The terms `weapon’ and `weapons system’ mean a device capable of any of the following:
(i) Damaging or destroying an object (whether in outer space, in the atmosphere, or on earth) by–
(I) firing one or more projectiles to collide with that object;
(II) detonating one or more explosive devices in close proximity to that object;
(III) directing a source of energy (including molecular or atomic energy, subatomic particle beams, electromagnetic radiation, plasma, or extremely low frequency (ELF) or ultra low frequency (ULF) energy radiation) against that object; or
(IV) any other unacknowledged or as yet undeveloped means.
(ii) Inflicting death or injury on, or damaging or destroying, a person (or the biological life, bodily health, mental health, or physical and economic well-being of a person)–
(I) through the use of any of the means described in clause (i) or subparagraph (B);
(II) through the use of land-based, sea-based, or space-based systems using radiation, electromagnetic, psychotronic, sonic, laser, or other energies directed at individual persons or targeted populations for the purpose of information war, mood management, or mind control of such persons or populations; or
(III) by expelling chemical or biological agents in the vicinity of a person.
(B) Such terms include exotic weapons systems such as–
(i) electronic, psychotronic, or information weapons;
(ii) chemtrails;
(iii) high altitude ultra low frequency weapons systems;
(iv) plasma, electromagnetic, sonic, or ultrasonic weapons;
(v) laser weapons systems;
(vi) strategic, theater, tactical, or extraterrestrial weapons; and
(vii) chemical, biological, environmental, climate, or tectonic weapons.
(C) The term `exotic weapons systems’ includes weapons designed to damage space or natural ecosystems (such as the ionosphere and upper atmosphere) or climate, weather, and tectonic systems with the purpose of inducing damage or destruction upon a target population or region on earth or in space.
II. Electronic Harassment. What is Electronic Harassment?
From: Electronic Harassment
If someone uses any electronic device to aid them in invading your person or property for the purpose of gathering information illegally, or for the purpose of causing harm, this is Electronic Harassment.
Electronic Harassment comes in many forms and types. We’ll try to explain what they are and what to do about them below.
Electronic Surveillance
Electronic Surveillance is the imposed observation of a person’s belongings, person or surroundings through the use of electronic listening devices, video recording or transmitting devices, spectral imaging through heat or infrared, sound or other radiation sources, and any other means of observing a person’s actions, possessions or routines. Not all forms of surveillance use electronic devices and not all forms of surveillance are illegal or considered harassment. Simply observing someone using ones eyes is certainly also considered surveillance and is not illegal in and of itself. Surveillance has become quite advanced and will become more pervasive as our society progresses in technology. Micro recorders, covert hidden video cameras (such as pinhole cameras), ultra tiny microphones, micro transmitters, and other bugging devices are easy to get by anyone at spy novelty shops and online stores.
Electronic Sabotage/Interference (Jamming)
Electronic sabotage or interference is any sabotage that is intentionally configuring personal property to either be destroyed or malfunction. Any intentional interference such as electronic noise generators, sound generators, light generators, spark gap disrupters, or any other form of EMI (electromagnetic interference) which either destroys, disrupts, causes malfunction or loss of resources is deemed to be electronic harassment.
Directed Harmful High Energy Devices
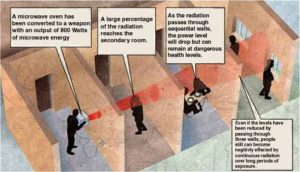
This is the most dangerous form of electronic harassment and is quite easy to implement against a person. Directed harmful high energy microwave devices and weapons can include such devices and equipment that are easily available almost anywhere in the World where there are people. Microwave ovens can be modified to focus and direct up to 1200 watts or more, depending on the model, of microwave energy at a person or property and are easy to produce. The results of an attack by a high energy device can be lethal, they can kill or at the least disable a human being or other animals. Attacks from high energy microwave weapons leave blisters, cause internal bruising and/or bleeding, stimulate cancer, cause cataracts, encourage tumors to grow, generate boils, or leave red patches on the skin. Directed Harmful High Energy Weapons will have effective ranges from the point of contact to several hundred yards. Directed Harmful High Energy Weapons can be used to destroy electronic devices and cause severe interference in computers and alarm systems which can allow forced entry or destruction of vital data. Radar guns are available from surplus stores most anywhere and can be obtained from ex-military sources or even police departments. Radar gun power outputs range from a two or three watts to 3 Megawatts! Portable radar guns range in size from small hand held devices to vehicle mounted long range high power models. These devices have very long ranges due to their greater power, higher frequencies and shorter wavelength. Radar guns emit long or short pulses of high energy capable of causing instant damage or death to living creatures. Semiconductor destruction or malfunction, brain damage & stopping vehicles are other uses for these devices. Other forms of directed harmful high energy include devices such as tasers, klystron guns (radar guns), ion beam guns, plasma pulse guns, soliton bombs, and many more devices.


Directional Microwave EMP Rifle (PARTIAL KIT) Partial kit (shown above). This partial kit will include a 50,000W (yes it says 50KW) Watt X-band military microwave magnetron with complete spec sheets from two manufacturers and operational information to make it work (about 30 pages), EMP rifle plans (over 49 pages), and qty:3 (12KV @ 1A) rectifiers. A device such as this can be made the size of a super soaker water gun, it operates at 9.2GHz and with a properly tuned horn antenna will have an effective range of over 300 yards (possibly more with larger antenna). Such a device could possibly cause semiconductors to burn out, microprocessors to malfunction, inductors to counter induce and create CEMF, induce RF noise, cause ionization of air or gases, cause junction rectification and erase computer data on hard drives, disk and solid state device. Operating such a device may be in violation of State or Federal Laws, consult your Local authority before operating such a device. UPS GROUND SHIPPING ONLY DUE TO INTENSE MAGNETIC FIELD FROM MAGNETRON. Do not purchase this kit if it is illegal to own or operate in your area. (This kit is real and available on the internet. The above photo and description was taken directly from an internet website, but we will not tell you where to find it!)
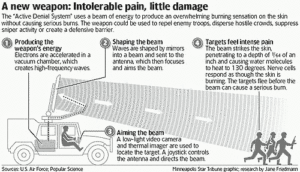
Active Denial Weapon
Directed energy weapon for “Active Denial” is now being deployed by the military.
Voice/Data/Image induction
This form of electronic harassment causes an individual to think they are loosing their mind or that they have a mental illness. There are 3 known methods of imposing VDI induction.
Microwave Carrier ULF-UHF Induction Method. This method utilizes a modulated microwave signal with either an audio, video, or other form of signal or even data may be used. The microwave energy with the VDI (Voice/Data/Image) carrier signal is then directed to the target area or individual. The reaction to this modulated microwave energy from one individual to another will usually be slightly different making it very difficult to diagnose as electronic harassment. The Voice/Data/Image induction form of harassment causes victims to hear voices in their heads or see random images or lights. Similar technology was developed to enable communication between humans and dolphins or even was purported to be used by secret agencies for the purposes of mind reading and control. A device known as the wireless neurophone has been patented along with other such devices that perform similar functions. A microwave carrier ULF-UHF induction device can be placed at a targets location and operated and monitored remotely. Transmission locations can be concealed in the same ways that cell telephone transmission sites so that they cannot be identified easily.
Direct Contact Induction Method. This method requires direct skin contact of the subject. Voice/Data/Image induction (VDI) is induced through the skin, using the natural ability of the skin to conduct energy. The DCI method uses a simple high voltage D.C. carrier, which is modulated with the VDI signal and is coupled to the subject body using capacitive skin pads. The contacts need to contact any part of the skin anywhere on the body. The signal is received and interpreted by the nerves below the skin surface and sent to the brain which processes the information signals, causing the images or sounds or data to appear to the target without the actual use of their eyes or ears. A similar device is also known as the neurophone. There are many patents for similar devices. Evidence of unauthorized use on someone is two or more circular red marks on the skin or two or more blisters.
Magnetic Pulse Induction Method. The neurons within the nerves and human brain are very sensitive to magnetic fields. The MPI method uses an induction coil to induce a low to medium magnetic field in and around the brain causing the neurons to misroute, slow down or revert. This form of electronic VDI harassment is often diagnosed as EMI (electromagnetic interference) sensitivity, which is similar to someone getting headaches from prolonged usage of cellular phones or nausea from being around power lines for extended periods of time. Magnetic Pulse Induction Method may be employed by using a device implanted within the targets home or surroundings and can be operated remotely.
Radiation
Radiation is a very common form of harassment. A potential harasser can easily buy an old x-ray gun from a surplus dealer and with only slight modifications use it to bombard a target with deadly amounts of x-ray radiation. Radiation devices can be battery powered and used for long periods of time. High exposure to x-ray radiation will cause tumors, brain disorders, mental illness, tremors, headaches, cataracts, seizures or even death. Radiation harassment is usually done over long periods of time, ranging from days to years, in order to induce harm. Radiation harassers can also get various radioactive materials such as thorium nitrate, plutonium oxide, uranium nitrate, and uranyl nitrite. Using radioactive materials a harasser can cause a terrible and agonizing death.
Implants
Implants are without a doubt the most invasive form of harassment. Electronic implants consist of transmitters, ESF generators, micro-neurophonic transceivers, tracking devices and other micro sized devices designed to cause harassment by tracking or controlling movement and thought. The most common implant was designed many years ago and is still used to this day. It consists of a unit that is powered by bodily fluids and is capable of transmitting voice signals, high voltage pulses, emitting a small tracking beacon signal, or other unspecified uses (mind control).
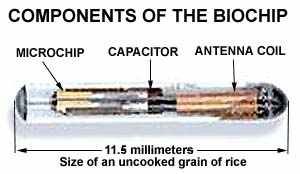




Newest version of a biochip implant. For more information about this chip go to
http://www.nasatech.com/Briefs//May99/ARC14280.html
Millions may be carrying microchips in their bodies worldwide. The Safe Medical Devices Act, which became a law in 1990, requires USA manufacturers of implants and medical devices, to adopt a method for identifying and tracking their products permanently implanted in humans, and to keep track of the recipients, in case malfunctions arise. Breast implants, pacemakers, replacement heart valves and prosthetic devices implanted in millions worldwide are all to be tracked. And one of the methods used to track these devices is implanting microchips which store data about the manufacturer, the surgeon, the date of implant, etc.
Laser Harassment Devices
The use of simple, easy to procure lasers to harass or “Dazzle” a subject is becoming more prevalent. Subjects of this type of harassment have reported seeing “little red dots” on their curtains, through their windows or on themselves. There have been numerous reports of people being momentarily blinded by red lights (red lasers) while they were driving in their cars. Some of these incidents have resulted in traffic accidents, although no permanent blindness has yet to be reported as a result of being “spotted”.
Laser Scope

Laser gun sight, zoom rifle scope, 3-axis adjustable tripod head. The parts that make this device can be purchased at any gun store and the tripod is a standard issue camera tripod.
Laser golf scope

Hand-held unit with laser gun sight and golf scope United States Patent 5,629,678 Gargano , et al. May 13, 1997
Personal tracking and recovery system
Abstract
Apparatus for tracking and recovering humans utilizes an implantable transceiver incorporating a power supply and actuation system allowing the unit to remain implanted and functional for years without maintenance. The implanted transmitter may be remotely actuated, or actuated by the implantee. Power for the remote-activated receiver is generated electromechanically through the movement of body muscle. The device is small enough to be implanted in a child, facilitating use as a safeguard against kidnapping, and has a transmission range which also makes it suitable for wilderness sporting activities. A novel biological monitoring feature allows the device to be used to facilitate prompt medical dispatch in the event of heart attack or similar medical emergency. A novel sensation-feedback feature allows the implantee to control and actuate the device with certainty.
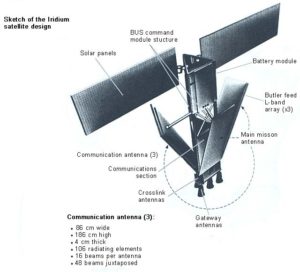
system
This is one of 66 low-earth orbiting (LEO) satellites comprising the Iridium satellite system. The original company went bankrupt so the US Department of Defense assisted in making sure the system stayed in operation. The system is currently maintained by the Boeing Company.
coverage
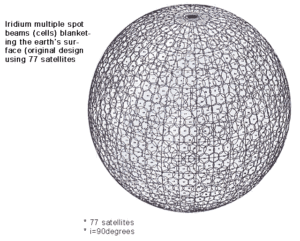
This is a diagram of the planetary coverage of the Iridum system. This system has transmit and receive coverage of the entire planet. Each circle is a coverage sector.
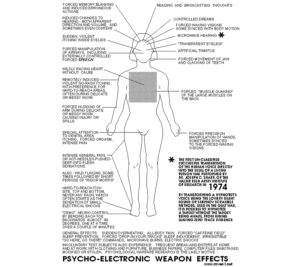
Symptoms of Electronic Radiation Exposure
Symptoms may include but are not limited to: Headache, eye irritation, dizziness, nausea, skin rash, facial swelling, weakness, fatigue, pain in joints and/or muscles, buzzing/ringing in ears, skin numbness, abdominal pressure and pain, breathing difficulty, irregular heartbeat, sexual stimulation and hearing voices (see Patent #4,858,612). Additional symptoms have been reported in some individuals such as paralysis, balance problems, body and/or muscle spasms, convulsions, confusion, depression, difficulty in concentrating, seizure, sleep disturbances, and memory difficulties.
What Can Be Done To Protect Against Electronic Harassment?
In a legal sense, there isn’t too much that can be done. You could change your venue, relocate or move to avoid the harasser but this isn’t usually a practical method for a variety of reasons. For starters, the best thing to do is give us a call from a secure phone. We will conduct a sweep of the suspect areas to locate the source of the suspected harassment and then assist in a course of action to stop the harassment. Natural obstacles are cheap and effective in blocking most X-rays and microwave or RF (could be a radar gun) signals that a harasser might use. Mountains, caves, desert areas, and large lakes or oceans offer excellent protection and can block or distort most forms of electronic harassment.
Shielding signals with Passive or Active shielding can be an effective measure.
If harassment is general to an area and not specifically directed to you, simply moving to another location is the easiest method to stop the harassment. If the harassment is specific to you, then you’ll need to employ some sort of shield or cover, such as mountains or a cave. Shielding may be your only alternative to stop the harassment if you cannot employ natural obstacles or shields. Passive shielding is less expensive then Active shielding and consists of special metal materials designed to block high frequency RF energy, X-rays, etc. Active shielding uses sophisticated electronic equipment to jam, capture, redirect, distort or nullify the harmful energy.
It isn’t legal for a private individual, a company or a corporation to use electronic harassment on you. The military and law enforcement, however, can use non-lethal weapons (see USC Title 50 Chapter 32 Section 1520a).
Further, testing of electronic equipment; discovering unauthorized electronic surveillance; training of intelligence personnel by officers the United States is allowed.
http://www4.law.cornell.edu/uscode/50/1805.html
Notwithstanding any other provision of this subchapter, officers, employees, or agents of the United States are authorized in the normal course of their official duties to conduct electronic surveillance not targeted against the communications of any particular person or persons, under procedures approved by the Attorney General.
Psychotronic Tortures
“Pervert FBI and NSA psychopaths are secretly and illegally conducting non-consensual, sadistic, synthetic telepathy experiments and psychotronic weapon attacks on hundreds of thousands of innocent citizens in the United States and elsewhere.
Email this to all your friends and peers and spread the knowledge, so all Americans and other citizens elsewhere educate themselves about the latest horrifying and disgusting secret technologies being used by FBI and NSA on hundreds of thousands of innocent citizens worldwide.
It would be great if somebody blogs this post and spread the word on internet for the benefit of all freedom loving Americans and all the innocent citizens of the world. Majority of these innocent people do not even know they are torture-victims and are being used as guinea-pigs by these FBI and NSA perverts, torturers and psychopaths.”
——————
The Pentagon and the U.S. intelligence agencies called the N.S.A. [ National Security Agency ], C.S.S. [ Central Security Service ], D.I.A. [ Defense Intelligence Agency ], D.A.R.P.A. [ Defense Advanced Research Projects Agency ], C.I.A. [ Central Intelligence Agency ], the D.H.S. [ Department of Homeland Security ], and the F.B.I. [ Federal Bureau of Investigation ], COINTELPRO or Counter Intelligence Program unit has extremely top secret technology that can pick up the private thoughts given by individuals in the vibrations produced by the brains electrical impulses, and that these thoughts can be broadcast by means of microwave tranceivers, infrasound and ultrasound tranceivers, satellites, and any other form of technology which uses electromagnetic transfer, i.e. television, radio, the internet, and the telephone. The Pentagon calls this mind reading technology SYNTHETIC TELEPATHY, although there is nothing paranormal about it at all. The N.S.A. or National Security Agency is a part of the U.S. Department of Defense, and a very secretive part at that. The N.S.A. has a black budget, and is always headed by a flag officer from one of the branches of the U.S. military. The top secret technologies available to the U.S. military is usually thirty years or may be even more ahead of the technology which is available to the U.S. civilian economy. Who is to know among the general U.S. public what the level of technological development is within the secret laboratories of the N.S.A. and D.A.R.P.A. [ Defense Advanced Research Projects Agency ]. The headquarters of the National Security Agency is located at Fort George Meade in the U.S. state of Maryland.
Today, there are microscopic computer chips based on nanotechnology which can be inserted into a person by means of an injection,
capsule, or tooth filling, with or without the knowledge of a doctor or a pharmacist, and these computer chips can track the implanted person by radio or microwaves.
These microscopic computer chips can also be made invisible to detection by means of C.A.T. [ Computerized Axial Tomography ], M.R.I. [ Magnetic Resonance Imaging ], and P.E.T. [ Positron Emission Tomography ] scans, by some means of electromagnetic degaussing.
With the latest top secret, and rapid technological advancements available to the U.S. military intelligence agencies, the need for microscopic computer implants in conducting synthetic telepathy against targeted persons is obsolete by now.
Rather, a system of subliminal, subconscious, wireless microwave remote control is used today against targeted individuals suffering from synthetic telepathy harassment. Synthetic Telepathy is used for conducting torture training and/or experimentation against people as red herring “good cop/bad cop” or tough love acting, diversions, feints, decoys, and smokescreens, as smear campaigns by association, as openly secret intimidation campaigns against targeted dissidents, and as a means of espionage. Once it was believed that claims about C.I.A. agents secretly dumping radioactive material in the slums of U.S. cities during the 1950′s as part of a research program were simply mass conspiracy theories, until the U.S. federal government in the 1990′s publicly admitted that the allegation was true.
FBI and NSA agents who are part of a secret US society are genetically inclined sociopaths and psychopaths who work as hit men,
torturers, sexual abusers, stalkers, slanderers, and agent provocateurs involved in murders and torture of hundreds of thousands of innocent US citizens for years and years. At the last count there are 50,000 NSA spies who are businessmen, priests, community leaders and in all walks of life who are SPYING and keeping tabs on pretty much all Americans.
The synthetic telepathy espionage trainees, sociopaths, sadomasochistic torturers, slanderers, experimenters, and spies, in order to avoid developing any sympathy for their targeted victims, deliberately avoid actually feeling the emotions of their victims by following the squiggly EEG or Electroencephalograph lines on computer monitor screens, as well as the silent words thought by their victims which also appear on the computer monitor screens. Then again, who can feel all of the emotions and thoughts which any given person has undergone every second of their entire lifetime.
The emotions and silent words of the victims of synthetic telepathy operators can be broadcast against their will to anyone the
synthetic telepathy torturers choose to broadcast to, and they also have the power to block or censor any emotions and words of their victims which they do not want to be broadcast. The synthetic telepathy spies can also place their own criminal or antisocial, negative emotions and words into their victims by means of subliminal, subconscious, remote control microwave brainwashing technology, and they can change the voice behind their words so as to make it appear that it is the targeted victim and not themselves who are communicating by means of synthetic telepathy. They can also store emotions and silently thought words onto a supercomputer memory bank which they can rebroadcast at a later time. I believe that the synthetic telepathy operators, although having high I.Q.’s, are predisposed towards sociopathic behaviour because of a genetic defect or combination of genetic defects, and that the only way they can sustain enthusiasm in their lives is by engaging in an addictive pattern of sadomasochistic activities and fantasies.
If you do not believe that synthetic telepathy exists, then you should look at these following web sites which reveal that part of
electromagnetic psychological warfare and mind control which today is declassified:
I urge the readers to print/save this column as well as the following link where the NSA and their PSYCHOTRONIC WEAPON ATTACKS and SADISTIC TORTURE of hundreds of thousands of innocent American and worldwide citizens (guinea pigs and victims) are explained in detail with diagrams and technology.
“Covert Operations of the U.S. National Security Agency” (link unknown).
Readers are advised to print the document in the link above and study the pictures and technology.
Important things from the above link for Americans and other people to educate and protect themselves and their loved ones from these secret, non-consensual and illegal psychopathic experiments, attacks and tortures by these 100,000 FBI and NSA secret psychopaths and spies.
1) The NSA has records on all US citizens. The NSA gathers information on US citizens with over 50,000 NSA agents and spies
(HUMINT).
2) NSA personnel in the community usually have cover identities such as social workers, priests, church leaders, lawyers and business owners.
3) NSA personnel can control the lives of hundreds of thousands of individuals in the US by using the NSA’s domestic intelligence network and cover businesses.
4) This network (DOMINT) covers the entire US, involves tens of thousands of NSA personnel, and tracks millions of persons
simultaneously .
5) NSA DOMINT has the ability to assassinate US citizens covertly or run covert psychological control operations to cause subjects to
be diagnosed with ill mental health.
6) At the present time the NSA has nanotechnology computers that are fifteen years ahead of present computer technology.
7) SYNTHETIC TELEPATHY and other psycho-electronic weapon chips can be inserted into the victims’ bodies painlessly without their knowledge in a matter of minutes by FBI and NSA spies.
08) NSA computer generated brain mapping can continuously monitor all of the electrical activity in the brain continuously.
9) For electronic surveillance purposes, electrical activity in the speech center of the brain can be translated into the subject’s verbal thoughts.
10) NSA operatives can use this covertly to debilitate subjects by simulating auditory hallucinations, characteristic of
paranoid schizophrenia.
11) Without any contact with the subject, Remote Neural Monitoring can map out electrical activity from the visual cortex of a
subject’s brain and show images from the subject’s brain on a video monitor. NSA operatives see what the surveillance subject’s eyes are seeing.
12) Visual memory can also be seen. RNM can send images direct to the visual cortex, bypassing the eyes and optic nerves. NSA operatives can use this surreptitiously to put images into a surveillance subject’s brain while they are in REM sleep for brain-programming purposes.
13) The NSA, Ft Meade has in place a vast two-way wireless RNM system which is used to track subjects and non-invasively monitor audio-visual information in their brains. This is all done with no physical contact with the subject.
RNM is the ultimate method of surveillance and domestic intelligence.
14) Speech, 3D sound and subliminal audio can be sent to the auditory cortex of the subject’s brain (bypassing the ears), and images can be sent into the visual cortex. RNM can alter a subject’s perceptions, moods and motor control. RNM can alter a subject’s perceptions, moods and motor control.
15) The NSA’s Signals Intelligence has the proprietary ability to monitor remotely and non-invasively information in the human brain
by digitally decoding the evoked potentials in the 30-50 Hz, 5 milliwatt electromagnetic emissions from the brain.
16) Remote monitoring/tracking of individuals in any location, inside any building, continuously, anywhere in the country. RNM can electronically identify individuals and track them anywhere in the US.
17) Tens of thousands of persons in each area working as spotters and neighborhood/business place spies (sometimes unwittingly) following and checking on subjects who have been identified for covert control by NSA personnel.
HOW FBI/NSA disables, cripples and murders its own innocent American citizens.
God only knows how many of the unsolved murders and diseases are actually committed and spread by these 100,000 FBI and NSA agents and spies.
18) Chemicals and Drugs into Residential Buildings with Hidden NSA Installed and Maintained Plastic Plumbing lines. The NSA has kits for running lines into residential tap water and air ducts of subjects for the delivery of drugs (such as sleeping gas or brainwashing-aiding drugs). This is an outgrowth of CIA pharma-psychology (psychopharmacology).
19) Victims experience daily break-ins in their homes by FBI and NSA secret society spies. Victims of this endless torture has no way to prove the break-ins and poisoning of food since FBI and NSA spies have technology that can easily disable the video surveillance systems, phone lines and security alarm systems of the torture victims.
20) FBI and NSA spies threaten hundreds of thousands of these innocent torture victims in America with accidents, bio-terrorism attacks in the form of measles, chicken pox, small pox and other forms of viruses, life threatening diseases AIDS, debilitating diseases cystic fibrosis, alzheimers etc. FBI and NSA spies post these threatening messages on internet only the mind control victims can understand and knew those threats were meant for the victims. In some cases, unfortunately these torture victims do not even know they are torture victims.
PSYCHOPATHIC TORTURE EXPERIMENTS.
Reading and broadcasting private thoughts.
Frequent break-ins and poisoning of food.
Frequent break-ins and enters at home and at work with clothing, furniture, business papers, computer files sabotaged, modified or stolen.
Frequent break-ins and movement of items from their original places, lights, tv and other electronic appliances turned on or off.
Controlled dreams.
Forced waking visions some synchronized with body motion.
Microwave hearing.
Transparent Eyelids.
Artificial Tinnitus.
Forced movement of Jaw and clacking of teeth.
Forced precision.
Manipulation of hands.
Forced memory blanking and induced erroneous actions.
Induced changes to hearing – both apparent direction and volume and sometimes even content.
Sudden violent itching inside eyelids.
Forced manipulation of airways, including externally controlled forced speech.
Wildly racing heart without cause.
Remotely induced violent no-rash itching often during delicate or messy work.
Forced nudging of arm during delicate or messy work causing spills or injury.
Intense general pain or hot needles pushed deep into flesh sensations.
Wild flailing sometimes followed by short periods of “rigor mortis”.
Sudden overheating, all body pain, sleep prevention.
Forced drop-in-your-tracks sleep inducement.
Irresistible “go here, go there” commands.
Microwave burns, electric shocks.
TORTURE VICTIMS.
Impotency caused by secret poisoning of the food by FBI and NSA secret spies.
Usually alone in his/her torture.
Constant mental rape, insults and humiliation.
Has no privacy even for his/her private thoughts.
Cannot plan secretly nor hold trade secrets or intellectual property.
Is subject to vicious physical and psychological attacks.
Does not know how harassment is happening or by whom.
Does not know why harassment is happening.
May be accused of mental illness, called delusional.
Cannot get away, no matter where he/she goes.
Mind raped thought streams.
Bugged conversations.
Gossip, Rumours, Social and Job connections broken.
Microwave voices, clicks, pops, brain zapping, direct harassment.
Death and disease threats via internet messages from undercover FBI and NSA spies.
Mind control means influencing the behaviour of an individual. And to creating or remolding victims personality towards desired state. The desired model human for the elite of the world, or, “the Illuminati” is: Easily steerable mass-human without personal characteristics. A stupefied, dumbed down person. This secures the interests of the elite of the world. So they can lead our lives through changing times the way they want.
Apparently growing out of earlier government mind control research programs such as MKULTRA, and government suppression of dissent programs such as COINTELPRO, today’s mind control is covert, finely crafted, around the clock harassment perpetrated against citizens living in their homes and communities.
Destruction of family and other relationships by way of lies, bribes, and threats is a goal of the phase of today’s mind control. The current day mind control program has been carefully engineered so that if the target complains, their own words will instantly cause them to be labeled as mentally ill.
The mind/body symptoms of current day mind control include: excruciating pain.
Exceptionally frequent blanking of recent memories, and truncation of new ideas.
– Impotency caused by secret poisoning of the food by FBI and NSA secret spies.
– Very unnatural inability to sleep, as if large amounts of caffeine have been consumed.
– Sudden forced awakening at precisely the same time in the middle of the night, continuing for at least months, and
right on a clock time such as 4 am, zero minutes, zero seconds.
– Sudden clumsiness, which can result in spills, spoilage of precise work, or injury .
– Attacks of extreme fatigue, sometimes almost to the point of paralysis, when there is no reason for such attacks.
– Frequent powerful itching without rash, and which may start as a small electric shock.
– Artificial “bee stings”, especially while trying to get to sleep.
– Wildly racing heart without any cause.
– Sudden overheating, without any cause.
– Frequent flailing of arms and legs as you try to sleep.
– Fake sounds such as alarm clock going off when it shouldn’t, telephone ringing when there is no incoming call, knocking on the door but no one is there.
– Voices, either very insulting, or telling you things that indicate you are under surveillance.
– Vibration of body parts when trying to sleep.
– High pitched tone in ears, which may change when switching electronic equipment on or off In some cases, statements by strangers indicating they know what you had for supper.
– In some cases, statements by strangers indicating they can read your thoughts.
– Artificial and powerful sexual stimulation.
– Artificial and powerful prevention of sexual stimulation.
FBI and NSA spies post messages anonymously on usenet to indicate to the torture victims how they made the victims impotent. Ignore the title in the thread and read the subtle threatening text from FBI and NSA spies.
One can imagine how many of the hundreds of thousands of innocent Americans are made impotent by these disgusting, horrifying and sadistic FBI and NSA psychopaths.
This is the exterior of mind control. The non-noticeable mind control is more dangerous one. That is the manipulation of our thoughts and emotions without our notice of things.
We think we lead our lives but we do not. We have to wake up to take notice on the situation. And try to change the course of history.
FBI and NSA secret society imposes us the New world order using mind control. And we can’t shield ourselves from it, which makes us as puppets on strings.
“Electromagnetic Weapons and Mind Control”:
from CNN’s Special Assignment, about 1985, at http://www.mindcontrolforums.com/cnn-mc.htm , by Chuck De Caro, CNN Special Assignments, and “List of mind control symptoms, in “2005 update:
The convergence of the cold war history of mind control and electromagnetic weapons with new post cold war government neuroscience reserch programs,” by Cheryl Welsh, Director, Mind Justice, 2005, at http://www.mindjustice.org/2005update.htm and http://www.mindjustice.org/symptoms.htm
Also, there is an interesting article called “Brain wave technology could change lives: Imagine controlling a computer using only your thoughts.”
This technology already exists in the civilian economy as a means of playing video games, for example. See this link:
http://www.msnbc.msn.com/id/6661974/
The article was written by Robert Bazell, correspondent for NBC News, and was updated at 7:31p.m., December 6, 2004. Another web site concerned with gaining information on the electrical activity of brainwaves, and by means of wireless technology, can be found in
the Sunday, 17 November, 2002, 00:41 GMT BBC NEWS World Edition article called “Remote control brain sensor”, at
http://news.bbc.co.uk/2/hi/health/2361987.stm
MANCHURIAN CANDIDATES.
“4 Elite Airborne commandos Return from a Special Operation in Afghanistan and suddenly torture and murder their wives”.
Friday, July 26, 2002 1:33 p.m. EDT FORT BRAGG, N.C. (Reuters)
– Four U.S. soldiers stationed at Fort Bragg, including three special operations servicemen who returned home this year after tours
of duty in Afghanistan, allegedly killed their wives recently, military officials said on Friday. In two of the cases, the soldiers killed themselves after shooting their spouses, officials said. In the other two, the servicemen have been arrested and are facing charges.
“There has been a recent series of instances where soldiers have either committed murder or murder-suicide against their wives,”
said Maj. Gary Kolb, a spokesman for the Army Special Operations Command.
I wonder how many of the murders and suicides in America were actually remotely manipulated, induced and orchestrated by these FBI and NSA secret mind control and mind manipulation experiments.
http://www.projectfreedom.cng1.com/esp.html
STARGATE
is one of the many names given to the Army’s classified clan of remote viewers. This project was hidden deeply within the government for close to two decades. The work of Harold Puthoff Ph.D., at SRI international …joined with the work of others at the Cognitive Science Laboratory … helped to supply the CIA with the framework of what was then known as Project GRILLFRAME. By 1978 America’s first remote viewers were at work. It is rumored the cold war was responsible for the government’s interest in remote viewing, because Russia had spies not dissimilar to our remote viewers.
Psychic Dictatorship in the U.S.A.
Alex Constantine
(1995) Another bombshell from the fecund furnace of Feral House Press.
Constantine, a political researcher in the mold of Mae Brussell, has gathered together a well-documented survey. “Bombing minds rather than bodies is the warfare of the new millennium… Funded under the euphemism of Non-Lethal Technology, the Pentagon has developed the ability to transmit voices, and inflict pain, madness, even death, with the push of a button. Hard to believe? Believe it!
Official sources have publicly admitted to the existence of such technology.”
Topics covered: Telemetric mind control, hearing voices, false memory hoax, E. Howard Hunt’s Death Squads, The GOP’s Pink Triangle & the CIA, Johnny Carson and the S&L crisis, and let’s not forget the chapter on NutraSweet as crowd control.
221 pages,
PB
PDU
$12.95.
The term “mind control” comes from former CIA director Allen Dulles.
In 1953, Dulles, speaking before a national meeting of Princeton alumni, distinguished two fronts in the then-current “battle for
men’s minds”: a “first front” of mass indoctrination through censorship and propaganda, and a “second front” of individual “brainwashing” and “brain changing.” Before an audience of fellow Ivy Leaguers, Dulles skipped the usual pieties about democracy. The same year, Dulles approved the CIA’s notorious MKULTRA project, and exempted it from normal CIA financial controls.
A partial list of aggressive promoters of this new technology includes Oak Ridge National Lab, Sandia National Laboratories, Science
Applications International Corporation, MITRE Corporation, Lawrence Livermore National Lab, and Los Alamos National Laboratory.
In 1996, the US Air Force Scientific Advisory Board published a 14-volume study of future developments in weapons called New World Vistas. Tucked away on page 89 of an ancillary 15th volume are some hair-raising insights into the future ‘coupling’ of man and machine in a section dealing with ‘Biological Process Control’. The author refers to an ‘explosion’ of knowledge in the field of neuroscience, adding, ominously:
One can envision the development of electromagnetic energy sources, the output of which can be pulsed, shaped, and focused, that can couple with the human body in a fashion that will allow one to prevent voluntary muscular movements, control emotions (and thus actions), produce sleep, transmit suggestions, interfere with both short-term and long-term memory, produce an experience set, and delete an experience set.
Translating the words ‘experience set’ from military jargon into plain English, this means, simply, that they envisage the ability to erase your life’s memories and substitute a new, fictitious set.
By projecting such developments into the future, the authors of New Vistas are camouflaging present day capabilities. A similar futuristic scenario with many references to mind manipulation is described in The Revolution in Military Affairs and Conflict Short of War (US Army War College, 1994). Authors Steven Metz and James Kievit declare:
“Behaviour modification is a key component of peace enforcement” and “The advantage of [using] directed energy systems is deniability.” The authors ask: “Against whom is such deniability aimed?” The direct answer is “the American people”.
Edward Tilton, President of Silent Sounds Inc., says this about S-quad in a letter dated 13 December, 1996:
“All schematics, however, have been classified by the US Government and we are not allowed to reveal the exact details. We make tapes and CDs for the German Government, even the former Soviet Union countries! All with the permission of the US State Department, of course. The system was used throughout Operation Desert Storm (Iraq) quite successfully.’
By using these computer-enhanced EEGs, scientists can identify and isolate the brain’s low-amplitude “emotion signature clusters”, synthesize them and store them on another computer.
In other words, by studying the subtle characteristic brainwave patterns that occur when a subject experiences a particular emotion, scientists have been able to identify the concomitant brainwave pattern and can now duplicate it. “These clusters are then placed on the Silent Sound carrier frequencies and will silently trigger the occurrence of the same basic emotion in another human being!”
Microwaves can also alter the permeability of the body’s blood-brain barrier,14 which can synergistically increase the effects of drugs, as the military is well aware. “Using relatively low-level RFR, it may be possible to sensitize large military groups to extremely dispersed amounts of biological or chemical agents to which the un-irradiated population would be immune.”15
Sound can be transmitted even easier through the use of implants -cochlear implants, implants that send electrical signals into the fluid of the inner ear, or implants that transmit sound vibrations via bone conduction, such as the cases of dental fillings picking up audible radio signals.
The stimoceiver, invented by Dr. Jose Delgado, consists of wires running from strategic points in the brain to a radio receiver/transmitter located entirely under the skin. Through this device, Delgado was able to stimulate raw emotions such as arousal, anxiety, and aggression with the turn of a knob.
Of course, secret research by the US Government into microwaves and synthetic telepathy has moved on considerably since the end of the Cold War … secret microwave radiation can be used to induce in unsuspecting victims: “Headache, fatigue, perspiring,dizziness, menstrual disorders, irritability, agitation, tension, drowsiness, sleeplessness, depression, anxiety, forgetfulness, and the lack of concentration.”
Naval Research Lab Attempts To Meld Neurons And Chips: Studies May Produce Army of ‘Zombies.’
Future battles could be waged with genetically engineered organisms, such as rodents, whose minds are controlled by computer chips engineered with living brain cells…. The research, called Hippo-campal Neuron Patterning, grows live neurons on computer chips.
“This technology that alters neurons could potentially be used on people to create zombie armies,” Lawrence Korb, a senior fellow at the Brookings Institution, said.

Comments (0)