Webmaster Introduction: In my opinion, the following seven power point presentations made by and for US Special Operations Command (USSOCOM) and their military and corporate partners clearly describe and detail the “technology,” systems, and personnel behind the international “organized stalking-electronic torture”/”targeted individual program” black operation. These ppt presentations indicate that this new form of unconventional warfare/low intensity conflict being covertly waged against innocent civilians placed on the Terrorism Watch List under the pretext of the so-called “War on Terrorism” is actually “multi-domain warfare.”
The following terms and technologies, depicted in these power point presentations, strongly suggest that so-called “Clandestine Tagging, Tracking, and Locating (CTTL)”, later termed “Hostile Forces- Tagging, Tracking, and Locating (HF-TTL), IS the “black” USAP (Unacknowledged Special Access Project) commonly referred to as the Targeted Individual Program/Organized Stalking-Electronic Harassment. Furthermore, TIs are obviously the expendable guinea pigs/test subjects for development of these technologies:
1) Tagging, Tracking, and Locating Human (High-value) targets aka “hostile forces” to support the Global War On Terrorism (GWOT)
2) Technologies include:
Nanotechnology (including Quantum Dot and Self-assembled Photonic Antenna)
Biotechnology (including “biomimetic devices for detection and identification at long distances” and “Taggants for Biological Signature Amplification, Translation,”)
Chemistry (including “signature enhancing Taggants” and “chemical/biochemical sensors for natural signatures”)
3) Participating agencies include: DARPA, Army Research Lab, NSA, DIA, Air Force Research Lab, DOE, and Industry
4) Human signature detection via skin spectral emissivities, thermal fingerprints at long distance
5) fieldable “bio-electronics”
6) bio-engineered signature translation and bio-reactive taggant (implant)
7) self-assembled photonic antennae
8) quantum dots
9) biometrics and tactical site exploitation (forensics)
10) Operation “Silent Dagger”!!!! This is also a Freemason’s term for their historical silent, slow, soft kill operations also termed the “White Glove”
11) Ground SIGINT (Signals Intelligence) Kit (GSK)
12) Joint Threat Warning Systems from the Air, Land, and Sea
13) RF (radio-frequency) and non-traditional (eg., optical/multi-band) Tags and R/Xs
14) “synchronize aquisition of signals intelligence (SIGINT) capabilities across the air, ground and maritime (warfare) domains”
15) SPECIAL RECONNAISSANCE, SURVEILLANCE, AND EXPLOITATION
16) Blue Force Tracking (BFT)
17) Special Operations Tactical Video Systems (SOTVS)
18) Sensitive Site Exploitation (SSE)
19) tiny satellites that keep tabs on targets from above (SpaceX rocket carrying the CubeSats—inexpensive satellites so small they can fit in the palm of your hand)
20) tracking satellites are part of the growing Special Operations focus on “high-value target” missions
21) tracking tags on enemies including radio frequency identification devices, quantum dots that could be used to track a singe molecule, and tagging measures such as insect pheromones
To acquire the high-value human “targets” needed to test and develop these clandestine weapons systems, the US government, through the FBI-DHS Fusion Centers and Neighborhood Watch Programs among others, has mislabeled innocent citizens as “terrorists” and “hostile forces.” Thus, ALL involved in these secret black ops are complicit in “crimes against humanity,” “war crimes,” murder, attempted murder, torture, terrorism, and TREASON. These individuals and institutions are the real terrorists and they are TRAITORS!
These black programs are funded via American tax dollars and deploy regular and irregular (citizen-based agents) forces as well as special forces against innocent citizens.
I. US Special Operations Command: Continuous Clandestine Tagging, Tracking, and Locating (CTTL)

by Doug Richardson SOAL-T WSO, Sept. 5, 2007
Also at: Continuous Clandestine Tagging, Tracking, and Locating (CTTL) Mr. Doug Richardson SOAL-T WSO5 September 2007 US Special Operations Command
Mr. Doug Richardson SOAL-T WSO 5 September 2007. The overall classification of this briefing is: UNCLASSIFIED and Locating (CTTL) The Ability to Locate, Track, and Identify Human Beings..
Highlights From PPT:
p. 3: Continuous Clandestine Tagging, Tracking, and Locating (CTTL)
– The Ability to Locate, Track, and Identify Human Beings and Other Important Targets
Directly Supports DoD’s Ability to Prosecute the Global War on Terrorism (GWOT)
Forces Require an Ability to Apply and Monitor Tags
Detect and Identify Targets Based on Their Unique Observable Characteristics Without Undue Exposure of Personnel to Risks and With Devices That are Sufficiently Clandestine to be Effective.
p. 4: Partnership between Assistant Secretary of Defense for Special Operations and Low Intensity Conflict (ASD SO/LIC), USSOCOM, and U.S. Army
Objective: Conduct a Collaborative Effort to Develop New Capabilities for Clandestine Tagging, Tracking, and Locating in Response to Priorities Established in a Quick-look Capability-based Assessment Conducted in Response to the Findings of the QDR
Approach: Transition Existing State-of-the-Art Technologies in Nanotechnology, Chemistry, and Biology to Operational Systems Through the USSOCOM Acquisition Process and Conduct RDT&E From Basic Research Through Prototyping to Provide Continuous Improvements in the CTTL Technology Available for Transition to the Operators. Specific Capability Projections Are Classified.
p. 7: CTTL– Key Enabling Technologies
Nanotechnology
Clandestine Devices
High Functional-density Devices
Self-organizing, Self-deploying Devices
Processing and Communications
Energy Harvesting
Biotechnology
Biomimetic Devices for Detection and Identification (ID) at Long Distance
Bio-based Devices for Detection and ID at Long Distances
Taggants for Biological Signature Amplification, Translation
Natural Signature Detection and ID
Chemistry
Signature Enhancing Taggants
Chemical/Biochemical Sensors for Natural Signatures
p. 8: CTTL– Partnership for Transition—
DDR&E and USSOCOM AE Executive Sponsorship and Oversight
USSOCOM Transition
PEO-Special Projects
PEO-Intelligence and Information Systems
Collaborative Execution of S&T
DoD Service Laboratories
Defense Advanced Research Projects Agency (DARPA)
ASD(SO/LIC) Coordinated Investments
Intelligence Community Research Organizations
DOE Laboratories
p. 9: CTTL — Key FY (Fiscal Year) 08 Outcomes
Taxonomy of Projects of Interest
17 BA 3
11 BA 2
8 Organizations
– DARPA
– Communications-Electronics Research, Development, and
Engineering Center (CERDEC)
Night Vision and Electronic Sensors Directorate (NVESD)
− Army Research Laboratory (ARL)
− National Security Agency (NSA)
− Defense Intelligence Agency (DIA)
− Air Force Research Laboratory (AFRL)
− Department of Energy (DOE)
− Industry
Fourteen Transitions Projected within 24 Months
p. 13: CTTL — Human Signature Detection
Skin Spectral Emissivities Measured
Thermal Fingerprints Determined
“Target” Reacquired 90 Minutes Later
Goal: Verification of Capability and Operational Value Within 2 Years
Human Thermal Fingerprint at Long Distance
p. 14: CTTL –Human Signature Detection —
Goal: Demonstration of Fieldable “Bioelectronics” Within 5 Years
Synthetic Dog’s Nose Sensor
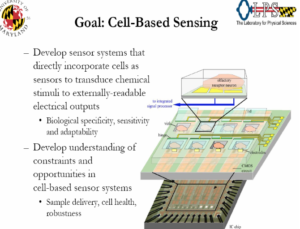
p. 15: CTTL — Signature Amplification/Translation
Bioengineered Signature Translation Bioreactive Taggant
Goal: Move Basic Research to Advanced Development in 3 Years
Current Capability – Bioengineered Signature Translation
p. 16: CTTL — Nano-scale Devices
Quantum Dots
Goal : Micro-scale in 12 Months, Nano-scale in 4 to 5 Years
Self-assembled Photonic Antenna
II. UNCLASSIFIED Mr. Douglas Richardson Program Executive Officer SPECIAL RECONNAISSANCE, SURVEILLANCE, AND EXPLOITATION
Highlights From PPT:
Graphics on p. 4:


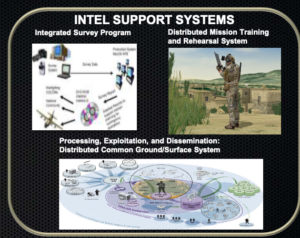

p. 6: Webmaster Comment: We “TIs” are here referred to as “Hostile Forces”

p. 7: HF-TTL (Hostile Forces- Tagging, Tracking, and Locating; formerly CTTL) Equipment

p. 8: Tactical HF-TTL Equipment

p. 9: Tactical Video Systems

p. 11: Sensitive Site Exploitation

p. 12: Sensitive Site Exploitation – Exploitation Analysis Center

p. 13: DISTRIBUTED COMMON GROUND/SURFACE SYSTEM SPECIAL OPERATIONS FORCES (DCGS-SOF)
(Projects Include Silent Dagger!!!! Webmaster: This the Freemason’s term for their historical silent, slow, soft kill operations also termed the “White Glove”)

p. 15: DCGS (DISTRIBUTED COMMON GROUND/SURFACE)-SOF FMV PED

p. 16: DCGS (DISTRIBUTED COMMON GROUND/SURFACE)-SOF SILENT DAGGER

Webmaster Comment: Again, please note that “Silent Dagger” is a Freemasonic term for secret, silent, slow kill operations of many Masons against a victim. Another Masonic term for this form of secret murder is the “White Glove.”
p 17: Union Dagger

p. 18: Joint Threat Warning System (JTWS)

p. 19: Ground SIGINT (Signals Intelligence) Kit (GSK)

p. 20: JTWS Air

p. 21: PRECISION GEO-LOCATION (PGL)

p. 22: JTWS Maritime

p. 23: Rapid Capability Program

p. 24: Rapid Capability Program

p. 25: Rapid Capability Program

III. SPECIAL RECONNAISSANCE Mr. David Breede, Program Executive Officer SPECIAL OPERATIONS FORCES INDUSTRY CONFERENCE EXPANDING THE COMPETITIVE SPACE
The Program Executive Office for Special Reconnaissance (PEO-SR) is responsible for the acquisition, fielding, and sustainment of intelligence systems for Special Operations Forces (SOF). The systems contribute directly to USSOCOM priorities to deter, disrupt, and defeat terrorist threats and sustain and modernize the force in persistent …
Highlights From PDF:
p. 2: Program Executive Office Special Reconnaissance Mission Statement
Webmaster: Insert the word “warfare” in front of the word “domains” and you realize that this is “multi-domain warfare,” i.e., integration of all six warfare domains, including sea, land, air, space, cyberspace and cognitive warfare.

p. 3: Program Executive Office Special Reconnaissance
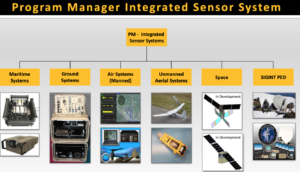
p. 6: Program Manager Integrated Sensor System

p. 7: Integrated Sensor Systems

p. 8: Program Manager- Technical Collection and Communication

p. 9: Technical Collection and Communications (TCC)

p. 13: US SOCOM – BAAST – 2020

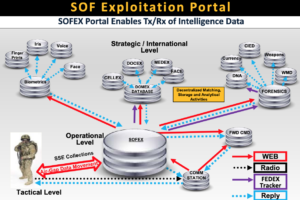
p. 16: SOF Exploitation Portal
IV. Successes / Lessons Learned: Adapting Technology to Enhance Technology to Enhance the Warfighter
Mr. Doug Richardson
SOAL-T WSO
4 September 2007
US Special Operations Command
https://ndiastorage.blob.core.usgovcloudapi.net/ndia/2007/disrupt/Richardson_USSOCOM.pdf
V. SPECIAL RECONNAISSANCE, SURVEILLANCE, AND EXPLOITATION by Douglas Richardson and David Breed (Special Operations Forces Industry Conference)
Clandestine Tagging, Tracking, & Locating (CTTL) Partner Nation Support. Integrated Survey Program (ISP) PEO SRSE Mr. Doug Richardson PROGRAM EXECUTIVE OFFICE SPECIAL RECONNAISSANCE, SURVEILLANCE, AND EXPLOITATION . … Blue Force Tracking (BFT) Special Operations Tactical Video Systems (SOTVS) Sensitive Site Exploitation (SSE)
VI. Portfolio Review and APBI Mr. Douglas Richardson
Hostile Forces – Tagging, Tracking, & Locating. Special Operations Tactical Video System. … And Theater Special Operations Command Partner With IC, Services, Industry Annually Insert Technology Updates … • Clandestine Tagging Tracking And Locating (CTTL): Develops And Prototypes …
VII. Mr. Douglas Richardson Program Executive Officer Special Reconnaissance, Surveillance, and Exploitation (SRSE)
From Power Point presentation: “Projects Include: Enterprise, Full Motion Video And Silent Dagger”
VIII. (Popular Mechanics Article) U.S. Special Ops Building Satellites to Track Terrorists Everywhere (2011)
The raid on Osama bin Laden’s compound this month highlighted special forces’ focus on finding high-value targets. Their hunt extends into space, too. An official with U.S. Special Operations Command has confirmed that his organization is testing tiny satellites that could keep tabs on targets from above.
An official with Special Ops revealed Wednesday that the U.S. recently launched mini-satellites that could clandestinely track high-value targets, like al-Qaida terrorists. “We sent up four satellites to demonstrate passing TTL [tagging, tracking, locating] data,” Doug Richardson, a civilian official at U.S. Special Operations Command, told an audience on Wednesday, referring to a December launch of a SpaceX rocket carrying the CubeSats—inexpensive satellites so small they can fit in the palm of your hand, and which have been used for scientific missions for a number of years.
Richardson, an official working in the Special Reconnaissance, Surveillance and Exploitation program in Special Ops Command, is responsible for several programs designed to help locate high-value targets using covert tracking tags: Hostile Force Tagging, Tracking and Locating, and Clandestine Tagging, Tracking and Locating. Unlike regular Tagging, Tracking and Locating technology—which is used to keep track of friendly forces—these programs are designed specifically to track down enemies and combatants, and thus employ covert tags.
These tracking satellites are part of the growing Special Operations focus on “high-value target” missions, best exemplified by the raid earlier this month that killed al-Qaida leader Osama bin Laden. Richardson presented his office’s work in a packed, standing-room-only auditorium at the Special Operations Forces Industry Conference in Tampa. The satellites may solve a fundamental dilemma of using tracking tags on enemies: how to follow them once they are in place, particularly in parts of the world like Afghanistan, where having a satellite in place to capture a signal can be a challenge. Presently, Special Ops commanders can’t just take over an entire military satellite to keep over a moving target. With a small and inexpensive CubeSat, they could.
Citing the sensitivity and classification of the topic, Richardson declined to go into detail on the specific types of sensors U.S. forces are developing and deploying. However, several methods are already on the market—some simple, and some strange. A number of companies have openly advertised covert tags using technology such as radio frequency identification devices, and also more elaborate technologies, such as quantum dots that could be used to track a singe molecule. Scientists have also proposed more exotic tagging measures such as insect pheromones.
“The thing worked,” was about all Richardson would say about the specifics of the Special Forces’ sats, but he added that there are plans to move forward and improve the system. That doesn’t mean, though, that these satellites are already being used. “The [system] I sent was just to test the theory that we could do it,” Richardson told PM.

































This Post Has 0 Comments