Epigraph Quote from 2nd article:
CISA (Cybersecurity and Infrastructure Security Agency) has categorized people’s “thoughts” as being part of the government’s infrastructure – meaning the government believes it owns whatever activity takes place inside your head.
Webmaster Comment: The US governments’ claim that they own people’s thoughts springs directly from the technologies of thought reading, mind control, and mind manipulation developed over the past century and well explained in John St. Clair Akwei’s 1992 lawsuit against the National Security Agency. (See: Appendix 201: Gangstalking System Explained: 1992 Lawsuit of John St. Clair Akwei V. NSA (National Security Agency), Ft. Meade, MD, USA.) The NSA global spy system involving satellites, supercomputers, and COMMINT, SIGINT, DOMINT, and NEURINT (Communications, Signals, Domestic, and Neurological Intelligence) is capable of identifying, tracking, torturing, and terrorizing “cognitive offenders.” NSA’s Domestic Electronic Surveillance Network is perhaps THE technological lynch-pin in the Pentagon’s fraudulent “Global War on Terrorism” as well as their new sixth warfare domain, Cognitive Warfare, which is fully supported by the other five domains of land, sea, air, space and cyberspace, as part of NATO and DoD military doctrine.
The human guinea pigs on whom the military-intelligence-industrial complex has secretly tested and developed these cognitive weapons systems over the past eight decades are sometimes referred to as “targeted individuals.” You see, the Totalitarians want total information control, which, not coincidentally, is a recent term introduced for organized stalking-electronic torture.
Of course, if government owns everyone’s thoughts, they basically own everyone. Who are these ultimate totalitarians? Michael Ledeen, Jewish neoconservative, explained in his book, War Against the Terror Masters: Why It Happened. Where We Are Now. How We’ll Win (2003):
I. U.S. Government Says It Owns Everyone’s THOUGHTS, Calling It “Cognitive Infrastructure”
by Ethan Huff | NaturalNews.com
May 29th 2023, 11:35 am
Is Missouri v. Biden the reason why the deep state is trying to ram through the RESTRICT Act?
https://www.gao.gov/assets/gao-22-104714.pdf
(Natural News) The fight is on to hold the United States government responsible for colluding with social media companies to censor Americans’ free speech rights online.
Missouri v. Biden, which was filed on May 5, 2022, has been taking quite the trip through the court system. It was amended three separate times, most recently to add an amendment that transforms the case into a class action suit due to the sheer number of Americans impacted by the government’s crimes.
Uncover DC has been tracking the case, offering play-by-play details about what has been happening with the case over the past year. The plaintiffs, including the states of Missouri and Louisiana, pushed for expedited discovery to obtain a limited set of evidence and depositions from certain individuals.
“They argued that this evidence would allow them to make the case for a temporary injunction to stop the government from infringing on the first amendment rights of Plaintiffs and their citizens,” Uncover DC reported.
The judge granted the motion for expedited discovery and depositions, prompting a fight between the government and the judge, in this case Judge Terry Doughty. In short, the defendants want to stop all discovery and certain plaintiffs from being deposed.
Click here to visit Banned.Video!
RELATED: Federal Government Tracking Unvaccinated People Who Go To Doctor And Hospital Due to CDC-Designed Surveillance Program
(Related: In 2021, a Missouri court declared that the Wuhan coronavirus [Covid-19] mandates and restrictions imposed by “the whims of public health bureaucrats” are illegal.)
Is Missouri v. Biden the reason why the deep state is trying to ram through the RESTRICT Act?
In its argument against expedited discovery and depositions, the government tried to claim that forcing government workers to sit for lengthy depositions is inappropriate, especially for the head of CISA, who was summoned.
Fortunately for the plaintiffs, Judge Doughty disagreed, forcing the CISA head, White House Press Secretary Jen Psaki, and other alleged co-conspirators to sit down and tell all about what they did to deprive Americans of their First Amendment rights.
Psaki, as you may recall, made threats to social media companies straight from the podium, which prompted her being deposed. She then left her White House position, conveniently.
Over and over again, the government has lost every single time so far in Missouri v. Biden. And it appears as though Americans may finally be winning, at least in the sense that we can now see what has really been going on behind closed doors.
Tony Fauci, at one point, was also deposed. This prompted the government to try to seal all depositions and video, claiming that government “employees” were being threatened – though it could provide no such proof to back this claim.
Meanwhile, it was revealed throughout this process that CISA has categorized people’s “thoughts” as being part of the government’s infrastructure – meaning the government believes it owns whatever activity takes place inside your head.
This is the argument the government tried to use to justify its illegal invasion of people’s online privacy and speech. Were it not for the expedited discovery and depositions, we would not know that CISA has an entire designation for the public’s thoughts that it calls “cognitive infrastructure.”
The government has tried again and again to delay the inevitable by postponing the case, which the judge refused to do; by obfuscating the truth; and by trying to ram through the so-called “TikTok bill,” or the RESTRICT Act, which seems to be on the fast track precisely because of Missouri v. Biden.
“It is because they need Congress to approve their actions here – this lawsuit is going to make it so they can’t function,” writes Tracy Beanz for Uncover DC about the matter.
The U.S. government wants to control everything you do, say, and think. To learn more, visit Globalism.news.
Sources for this article include:
UncoverDC.com
NaturalNews.com
II. DoD Adds “Cognitive Security” to Governmental Disinformation Campaign
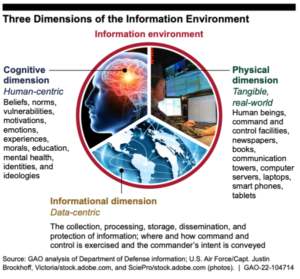
A 59-page report from the U.S. Government and Accountability Office (GAO) underpins much of the updated information policy and guidelines that are now present in all branches of the U.S. military. This report is the big “tell” about the direction of the DoD’s thought process about the “opportunities and threats to the DoD’s national security mission.” Familiar mis-,dis-, and mal-information terms like the “cognitive dimension” of the information environment as well as “cognitive security,” is discussed. The goal of the report is to help our DoD “protect the information environment.” GAO administered questionnaires to the leadership of 25 DoD organizations “asking about the information environment’s effect on their organizations.” The performance audit was conducted from January 2021 to September 2022.
UncoverDC has reported extensively on the government’s incursions into the domain of information and free speech. Cognitive infrastructure is now a common and consistent construct in the lexicon of agencies like CISA, the FBI, the DOJ, etc. While it is understandable for the DoD to want to protect our national security interests, trust in our government is at an all-time low. Many Americans feel they are no longer able to freely digest and disseminate information that agrees with their worldview. In many cases, as understood most recently because of the Twitter files and the seminal free speech case, Missouri v. Biden, Americans realize that much of the information on the internet is and has been highly controlled and non-conforming perspectives suppressed.
GAO Report on Information/https://www.gao.gov/assets/gao-22-104714.pdf
GAO Report: Cognitive Security
Featured prominently on the first page of the report is the now omnipresent mis-, dis-, and mal-information campaign. The GAO investigation found a “proliferation of ubiquitous [and malign] information, misinformation, disinformation, and malinformation” that has “prompted defense experts to begin examining the concept of cognitive security.” Thus is introduced a relatively new term into the government’s national defense lexicon— “cognitive security.” Cognitive security is a subset of “cognitive infrastructure.” This type of infrastructure has often been weaponized against Americans on social media platforms and in the media.
Cognitive resilience is another widely used term to describe a teachable process that helps “cultivate critical thinking and media literacy through education, as well as the development of tools that can provide real-time identification and defense for people and organizations encountering sophisticated influence efforts.”

GAO report/https://www.gao.gov/assets/gao-22-104714.pdf
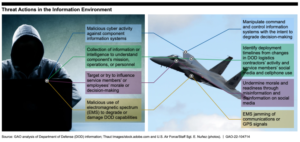
On one hand, the threat to our national security of poorly vetted information is real in the now information-rich virtual environment. Foreign actors work daily to infiltrate and influence public opinion, so it would not be far-fetched to believe they have their sights trained on military operations. The GAO highlights a number of “cyberspace threats, information or intelligence collection threats, influence threats, and EMS threats that adversely affect DoD personnel and capabilities,” as featured in the graphic below:
GAO Report/https://www.gao.gov/assets/gao-22-104714.pdf
The GAO report references a number of concepts and technologies that are now making their way into public awareness, such as fifth-generation wireless technologies that are “engineered to greatly increase the speed and responsiveness of wireless networks.” Such technology is increasingly the building block of an “extended reality” and “The Internet of Things” (internet-capable devices like phones and wearable devices). These technologies, according to the report, can have “positive benefits or negative consequences for the DoD.” These tools have the potential to distribute information rapidly, which impacts the ability to do damage control should bad information be disseminated. As such, all military branches must be properly and uniformly trained in a relatively new “doctrine” that reflects the “fundamental nature of information in joint operations.”
Again, the threats are real and should not be underestimated. There is a stark difference between the “industrial age capabilities” of our military and the “information age vulnerabilities” our service members must now confront. No doubt, we are changing how we fight because of our information-rich world. As stated in the report with its accompanying graphic:
“These information-age activities allow adversaries to target our capabilities and adversely affect military business functions and missions in ways that offset the industrial-age advantages we have developed, as shown in figure 2.
As a result of these activities, DoD must continue to find ways to protect information, systems, and minds through disparate security fields, such as information security, operations security, cybersecurity, physical security, and cognitive security.”

Page 2 GAO Report/https://www.gao.gov/assets/gao-22-104714.pdf
The Risks of Coordinated and Controlled Information
We are now a much more skeptical nation with regard to our First Amendment rights, and rightfully so. As previously stated, our government has waded into the territory of tyranny in the last few years, waging war with what most Americans hold dear; their freedom to think and speak freely, whether in person or on the internet.
Concerning our national security interests, the discussion is necessarily contextual. Had our government not pushed the boundaries of what has now come to be known as allowed speech, we might not be concerned over DoD policies that seek to explore how “adversaries can target the cognitive foundations of individuals.” It is one thing to be guarded against the informational threats of foreign actors, but it is quite another to target and/or label American citizens or maybe even our own service members with the same level of perceived threat.
Just two years ago, our own DoD, military service branches, and CDC worked together with big tech to #killthevirus in service of the promotional uptake of the COVID-19 mRNA shots and other government-sponsored research and treatments. Multiple town halls run by the U.S. Army led by Dr. Steven Cersovsky, Senior Advisor, MEDCOM and deputy director of the Army Public Health Center, pushed the vaccines, masking, and social distancing policies. In tandem, every branch of the military distributed controlled social media messaging on the subject. They also pushed shots for children. To wit, uniform and controlled messaging put out by the DOD is not always as neutral as they might have you believe. More importantly, millions listened and complied, in some cases, to their detriment.
III. Information Environment Opportunities and Threats to DOD’s National Security Mission Sept. 2022 pdf
Excerpt from above document:





This Post Has 0 Comments