Appendix 272: 1. Identify 2. Villify 3. Nullify 4. Destroy: Community Organized Stalking/”Coercive Persuasion” Ops Exposed by David Lawson (PI); summarized by webmaster & Eleanor White
Epigraph Quotes from “Cause Stalking” by David Lawson, P.I. (2007):
1) “The objective is to involve all available people in the operation, which is to destroy the target.”
2) These (stalking groups) are domestic terrorists. The FBI defines terrorism as, “the unlawful use of force or violence against persons or property to intimidate or coerce a government, the civilian population, or any segment thereof, in furtherance of political or social objectives.”
3) These groups are cults. A cult is a collection of individuals with a philosophy, an
organization and a system of beliefs which support their world view. Many organizations
fit this description. The use of tactics involving coercive persuasion is what separates cults from other organizations. Individuals who become involved with these groups lose their sense of self identity and take on the identity of the cult leader. Coercive persuasion used to be called brainwashing. There is nothing new about the use of this type of programming in criminal and religious groups, but its use is growing as these groups become larger and more
numerous.
David Lawson, P.I., author of “Cause Stalking” (2007) & “Terrorist Stalking in America” (2001)
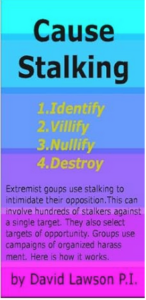
Eleanor White’s Summary of David Lawson’s Investigation Into Organized Stalking

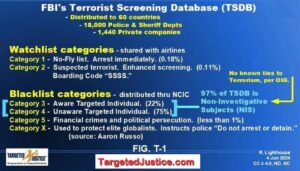
I. Webmaster Summary: Insights into gangstalking/domestic terrorism operations provided by Private Investigator, David Lawson in his short booklet, “Cause Stalking” (2007, above), reflect his direct experiences over 12 years “riding with” with low-level perpetrators that comprise the stalking cults/private armies. This is certainly organized crime. While much of the information seems solid, some of his conclusions seem questionable to me as well as other TIs.
Some of Lawson’s main points are summarized here:
1) Cause stalking/terrorist stalking has been used by extremist groups since the early 1990s, but it is not new.
2) These “organized programs of harassment include break-ins, property damage, assault and occasionally, even death.”
3) The goal of groups is to destroy their targets. Stalking groups feel they have god-like powers.
4) Stalking groups are well financed by corporations.
5) Members who join are generally blue collar workers who feel powerless, inferior, and angry. They include janitors, security guards, city workers, taxi drivers, cable, telephone, electrical company workers, firemen, policemen, phony census takers, fake preachers, pest control, locksmiths.
6) Stalking groups operate “above the law”- and have contempt for the law, courts, and police.
7) Stalkers are “having fun.”
8) Stalkers are considered disposable.
9) The sole financial beneficiaries are the leaders.
10) Anti-government groups are associated with militias.
11) Stalking groups are constantly recruiting especially angry and young people due to the high turnover rate.
12) Members patrol their territory (sector of a county) 24/7/365. They evaluate targets and report their findings to higher ups.
13) Stalkers often pretend to be police officers.
14) Stalking groups are of value to corporations and the politicians who work for them.
15) Group leaders remain in the background and receive political power and profit from the groups’ activities. Leaders identify the targets.
16) Stalking “causes” may include anti-abortion, animal rights, eco, and hate groups.
17) Common types of targets include government and corporate whistleblowers, civil rights and other types of activists, local politicians, Treasury agents, county clerks, police officers, judges, and targets of opportunity (newcomers/those without a support system).
18) Stalking groups profile their targets’ IQ, history, personality type. They often photograph targets. Photos are added to case files along with log of activities, friends, relatives, acquaintances, memberships, financial information, criminal history, health records, etc. Files of targeted individuals can be very large.
19) Surveillance is overt and done by large numbers of stalkers 24/7/365 for years.
20) Groups establish their base of operations very close to targets, commonly renting or commandeering neighboring apartments and homes. They maintain a vigil around the targets residence.
21) Groups systematically slander and smear targets, saying they are rapists, prostitutes, pedophiles, etc.
22) Groups and show targets’ neighbors fake case files of targets.
23) Groups maintain contacts with organized crime.
24) Stalking groups notify other stalkers as soon as targets leave their homes, either by cell phone or by business band radio.
25) Business band is widely used in small towns and pursuing targets becomes a sport.
26) Operations expand to include family, friends, and associates of targets.
27) The target is sensitized to the fact he/she is being stalked. He is constantly followed by cars with hadlights on, being photographed, etc.
28) Stalking teams will typically stand around a TI while he is making a purchase of sit near him in a restaurant.
29) Stalkers will observe as other stalkers harass a target.
30) Group members will engage the target in conversation and report the findings to other group members.
31) Victims typically experience: depression, anxiety and/or panic attacks, traumatic stress, PTSD, sleeplessness and/or nightmares, shame and guilt, self-blame, difficulty concentrating, headaches, fatigue or loss of motivation, difficulties with time (forgetting appointments, ), stomach problems, gastrointestinal disorders, eating disorders (weight loss or gain), feeling betrayed and/or violated, feeling powerless, helpless or out of control, increased blood pressure, loss of confidence and self esteem, overall loss of trust in people, problems with intimacy, problems with sex (sexual dysfuntion) withdrawal and isolation, suicidal thoughts or attempts, suicide/
32) Stalking groups use mind control tactics but do not have sophisticated weaponry (Webmaster: I question that.)
33) These groups control the help forums and many websites re: stalking so when real TIs provide them information, that information is used against the victims.
34) Group members will also try to befriend the target…. The goal is always to destroy.
35) It is a full time job for targets to protect themselves.
36) People in the stalking group are people with no skills, cowards, losers. But in the group they feel brave. It is all of them against a single target.
34) To protect themselves, targets must:
a) secure the residence. Do not leave any keys in the house.
b) it is a good idea to laugh at them and say, you’ve got to do better than that.
35) Groups communicate by business band or by radio (and cell phone!!!).
36) The average target is stalked for 4-6 years.
37) These criminal gangs are really private armies. They are domestic terrorists. They form a national network.
38) The groups are well-financed and operate as businesses
While his insights into the tactics used by stalking perpetrators are useful, Lawson is fairly vague about the identity of the “leaders:”
Lawson: “Group leaders do have political goals and the belief that the end justifies the means.” Lawson describes leaders as considering their members “disposable.” Lawson states that some leaders work for corporations and politicians (original book didn’t mention politicians.) Lawson states that leaders identify targets but don’t directly supervise the harassment group members.
Lawson describes leaders as having an “air of mystery”, “having worked for the CIA, NSA, or some other intelligence agency that doesn’t reveal information about their employees.” Lawson states that this “background” is likely mythology.”
Webmaster comment: Lawson’s discussions of (CIA) “coercive persuasion” (coercive thought reform) and cults in his Appendix C Mind Control may also indicate the CIA is the principal perpetrator. Indeed, Col. L. Fletcher Prouty’s book, “The Secret Team: The CIA and its Allies in Control of the United States and the World”, explains that in standard “counter-insurgency” doctrine carried out by the U.S. military-intelligence complex for many decades the CIA selects the “targets” and then the military tortures and/or kills them. I believe the same dynamic applies here, except that community stalkers perform the torture/elimination/coercive thought-reform/ aspects of these operations. In this case, government itself is waging covert domestic terrorism and warfare against members of its own population.
Here is what Lawson says about “coercive persuasion” as a tactic in Appendix C: Mind Control. To me, this is the most valuable part of the booklet and proves beyond a shadow of a doubt that the CIA is ultimately behind these programs!!!!!!!!!!
Synopsis of How Coercive Persuasion Works
Coercion is defined as, “to restrain or constrain by force…” Legally it often implies the use of physical force or physical or legal threat. This traditional concept of coercion is far better understood than the technological concepts of “coercive persuasion” which are effective restraining, impairing, or compelling through the gradual application of psychological forces. A coercive persuasion program is a behavioral change technology applied to cause the “learning” and “adoption” of a set of behaviors or an ideology under certain conditions. It is distinguished from other forms of benign social learning or peaceful persuasion by the conditions under which it is conducted and by the techniques of environmental and interpersonal manipulation employed to suppress particular behaviors and to train others. Over time, coercive persuasion, a psychological force akin in some ways to our legal concepts of undue influence, can be even more effective than pain, torture, drugs, and use of physical force and legal threats.
The Korean War “Manchurian Candidate” misconception of the need for suggestibility- increasing drugs, and physical pain and torture, to effect thought reform, is generally associated with the old concepts and models of brainwashing. Today, they are not necessary for a coercive persuasion program to be effective. With drugs, physical pain, torture, or even a physically coercive threat, you can often temporarily make someone do something against their will. You can even make them do something they hate or they really did not like or want to do at the time. They do it, but their attitude is not changed. This is much different and far less devastating than that which you are able to achieve with the improvements or coercive persuasion. With coercive persuasion you can change people’s attitudes without their knowledge a n d volition. You can create new “attitudes” where they will do things willingly which they formerly may have detested, things which previously only torture, physical pain, or drugs could have coerced them to do. The advances in the extreme anxiety and emotional stress production technologies found in coercive persuasion supersede old style coercion that focuses on pain, torture, drugs, or threat in that these older systems do not change attitude so that subjects follow orders “willingly.”
Coercive persuasion changes both attitude and behavior, not just behavior.
The Purpose and Tactics of Coercive Persuasion
(Webmaster comment: THESE ARE CIA MIND CONTROL TACTICS ALL THE WAY!!!!!!)
Coercive persuasion or thought reform as it is also known, is best understood as a coordinated system of graduated coercive influence and behavior control designed to deceptively and surreptitiously manipulate and influence individuals, usually in a group setting, in order for the originators of the program to profit in some way, normally financially or politically. The essential strategy used by those operating such programs is to systematically select, sequence and coordinate numerous coercive
persuasion tactics over continuous periods of time. There are seven main tactic types found in various combinations in a coercive persuasion program. A coercive persuasion program can still be quite effective without the presence of all seven of these tactic types. . .
TACTIC 1. The individual is prepared for thought reform through increased suggestibility and/or “softening up,” specifically through hypnotic or other suggestibility-increasing techniques such as:
A. Extended audio, visual, verbal, or tactile fixation drills; B. Excessive exact repetition of routine activities; C. Decreased sleep; D. Nutritional restriction.
TACTIC 2. Using rewards and punishments, efforts are made to establish considerable control over a person’s social environment, time, and sources of social support. Social isolation is promoted. Contact with family and friends is abridged, as is contact with persons who do not share group-approved attitudes. Economic and other dependence on the group is fostered.
TACTIC 3. Disconfirming information and non-supporting opinions are prohibited in group communication. Rules exist about permissible topics to discuss with outsiders. Communication is highly controlled. An “in-group” language is usually constructed.
TACTIC 4. Frequent and intense attempts are made to cause a person to re-evaluate the most central aspects of his or her experience of self and prior conduct in negative ways. Efforts are designed to destabilize and undermine the subject’s basic consciousness, reality awareness, world view, emotional control, and defense mechanisms as well as getting them to reinterpret their life’s history, and adopt a new version of causality.
TACTIC 5. Intense and frequent attempts are made to undermine a person’s confidence in himself and his judgment, creating a sense of powerlessness.
TACTIC 6. Nonphysical punishments are used such as intense humiliation, loss of privilege, social isolation, social status changes, intense guilt, anxiety, manipulation and other techniques for creating strong aversive emotional arousals, etc.
TACTIC 7. Certain secular psychological threats [force] are used or are present: That failure to adopt the approved attitude, belief, or consequent behavior will lead to severe punishment or dire consequence, (e.g. physical or mental iliness, the reappearance of a prior physical illness, drug dependence, economic collapse, social failure, divorce, disintegration, failure to find a mate, etc.). Another set of criteria has to do with defining other common elements of mind control systems. Robert Jay Lifton wrote a book called Thought Reform and the Psychology of Totalism which is considered to be a definitive work on the subject. If most of Robert Jay Lifton’s eight point model of thought reform is being used in a cultic organization, it is most likely a dangerous and destructive cult. These eight points follow:
Robert Jay Lifton’s Eight Point Model of Thought Reform
1. ENVIRONMENT-CONTROL. Limitation of many/all forms of communication with those outside the group. Books, magazines, letters and visits with friends and family are taboo. “Come out and
be separate!”
2. MYSTICAL MANIPULATION. The potential convert to the group becomes convinced of the higher purpose and special calling of the group through a profound encounter/experience, for example, through an alleged miracle or prophetic word of those in the group.
3. DEMAND FOR PURITY. An explicit goal of the group is to bring about some kind of change, whether it be on a global, social, or personal level. “Perfection is possible if one stays with the group and is committed.”
4. CULT OF CONFESSION. The unhealthy practice of self disclosure to members in the group. Often in the context of a public gathering in the group, admitting past sins and imperfections, even doubts about the group and critical thoughts about the integrity of the leaders.
5. SACRED SCIENCE. The group’s perspective is absolutely true and completely adequate to explain EVERYTHING. The doctrine is not subject to amendments or question. ABSOLUTE conformity to the doctrine is required.
6. LOADED LANGUAGE. A new vocabulary emerges within the context of the group. Group members “think” within the very abstract and narrow parameters of the group’s doctrine. The terminology sufficiently stops members from thinking critically by reinforcing a “black and white” mentality. Loaded terms and clichés prejudice thinking.
7. DOCTRINE OVER PERSON. Pre-group experience and group experience are narrowly and decisively interpreted through the absolute doctrine, even when experience contradicts the doctrine.
8. DISPENSING OF EXISTENCE. Salvation is possible only in the group. Those who leave the group are doomed. They get the same treatment as the group’s targets.
Coercive Persuasion is Used to Produce Deployable Agents
Programs identified with the above-listed seven tactics have in common the elements of attempting to greatly modify a person’s self-concept, perceptions of reality, and interpersonal relations. When successful in inducing these changes, coercive thought reform programs also, among other things, create the potential forces necessary for exercising undue influence over a person’s independent decision-making ability, and even for turning the individual into a deployable agent for the organization’s benefit without the individual’s meaningful knowledge or consent.
Coercive persuasion programs are effective because individuals experiencing the deliberately planned severe stresses they generate can only reduce the pressures by accepting the system or adopting the behaviors being promulgated by the purveyors of the coercion program. The relationship between the person and the coercive persuasion tactics are dynamic in that while the force of the pressures, rewards, and punishments brought to bear on the person are considerable, they do not lead to a stable, meaningfully self-chosen reorganization of beliefs or attitudes. Rather, they lead to a sort of coerced compliance and a required elaborate rationalization, based on the situation, for the new conduct.
In order to maintain the new attitudes or “decisons, sustain the rationalization or to continue to unduly influence a person’s behavior over time, coercive tactics must be more or less continuously applied. A fiery, “hell and damnation” guilt-ridden sermon from the pulpit or several hours with a high-pressure salesman or other single instances of the so-called peaceful persuasions do not constitute the “necessary chords and orchestration” of a sequenced, continuous, coordinated, and carefully selected program of surreptitious coercion, as found in a comprehensive program of “coercive persuasion.”
Truly peaceful religious persuasion practices would never attempt to force, compel and dominaté the free wills or minds of its members through coercive behavioral techniques or covert hypnotism. They would have no difficulty coexisting peacefully with U.S. laws meant to protect the public from such practices. Looking like peaceful persuasion is precisely what makes coercive persuasion less likely to attract attention or to mobilize opposition. It is also part of what makes it such a devastating control technology. Victims of coercive persuasion have: no signs of physical abuse, convincing rationalizations for the radical or abrupt changes in their behavior, a convincing “sincerity, and they have been changed so gradually that they don’t oppose it because they usually aren’t even aware of it.
Deciding if coercive persuasion was used requires case-by-case careful analysis of all the influence techniques used and how they were applied. By focusing on the medium of delivery and process used, not the message, and on the critical differences, not the coincidental similarities, which system was used becomes clear. The Influence Continuum helps make the difference between peaceful persuasion and coercive persuasion easier to distinguish.
Variables
Not all tactics used in a coercive persuasion type environment will always be coercive. Some tactics of an innocuous or cloaking nature will be mixed in. Not all individuals exposed to coercive persuasion or thought reform programs are effectively coerced into becoming participants. How individual suggestibility, psychological and physiological strengths, weakness, and differences react with the degree of severity, continuity, and comprehensiveness in which the various tactics and content of a coercive persuasion program are applied, determine the program’s effectiveness and/or the degree of severity of damage caused to its victims. For example, in United States v. Lee 455 U.S. 252, 257-258 (1982), the California Supreme Court found that “when a person is subjected to coercive persuasion without his knowledge or consent… [he may] develop serious and sometimes irreversible physical and psychiatric disorders, up to and including schizophrenia, self-mutilation, and suicide.”
Use of Coercive Persuasion on Targets
The tactics used by group leaders on their followers parallel those used on the groups’ targets. A major effort is spent by groups in trying to isolate their target from friends and family. Many targets do become isolated from them in an attempt to spare them. The harassment, wherever a target goes in public also tends to cause them to restrict their travels. Some stay home because they are afraid of break-ins and damage to their property.
Groups also attempt to control communications by intercepting mail and phone calls or trying to give the appearance that they do. They will sometimes even attempt to interrupt conversations a target has in public.
One of the purposes of a noise campaign is to attempt to interfere with the sleep patterns of the target. They will try to wake him up at night, as many times as they can. An effective noise campaign can be used to generate noise around the clock. Ideally, noise is synchronized with the target doing something, like turning on a tap, flushing a toilet, walking outside, walking near a window where movement can be seen, etc.
Groups try numerous tactics until they find those which cause the target to respond. Any response is considered to be a success. Then those tactics are repeated. The object is to train the target to respond like a dog does. Groups will also communicate with the target. Most communication is done by group members who make statements as they rush away. Topics can include what the target has done wrong or what he is doing wrong. They may also approach family members and make statements that the target is no good. Some statements involve threats against the target and/or his family. They try to make the target sorry for what ever it is he has done wrong.
Group members will also try to befriend a target. Their objective is to try to get the target to confess their fear and other feelings. Whatever information the target provides is used to entertain the group and provide a more effective attack. The control of time is also an important part of the attack. Simple time consuming tactics leave a target unable to leave a parking space or surrounded by slow moving vehicles, or having numerous people standing in line ahead of him, for the sole purpose of trying to keep him waiting as long as possible. A target spends more time trying to protect himself from attacks on his family and property. Some targets have become obsessed with trying to solve the puzzle of finding out who these people are or of keeping logs of license plates, etc.
Groups try to impose a system of rewards and punishments on their targets which involves additional harassment for communicating, and associating with other people. Laughing at or assaulting group members initially invites retaliation, but ultimately drives the group away. Group members are sensitized to all the tactics they employ. If a target uses their tactics on them, they react instantly. Police officers sometimes do bizarre things around them, like read the time from an imaginary watch on their wrists or talk on a cell phone which is upside down. It scares them. They get on their cell phones and try to reconcile what they have experienced with what they have been told.
However, there may be an equal probability that, as one 40-year TI informed me, “Jews are behind the whole thing.” In this case, secret gangstalking operations could be a major component of long-standing domestic terrorism/war operations carried out by this well-organized and well-funded “nation-within-a-nation” aka “deep state” against their perceived enemies. Both of these scenarios may also operate simultaneously. Certainly, I have personally observed that my stalkers/harassers include many Jews, Masons, and Mormons, etc.
II. Eleanor White article: American private investigator David Lawson spent approximately 12 years investigating stalking groups in the United States and Canada, mainly in the 1990s. He wrote about his experiences “riding with” these networked community harassment groups in two books.
The first, released in 2001, was: Terrorist Stalking in America
ISBN: 0-9703092-0-1
That book is now out of print. Lawson then produced an updated book on the same subject in March 2007: Cause Stalking
ISBN-13: 978-0-9703092-3-5
The community-based counterpart, organized stalking, is not well known to the average member of the public. This paper is to share some of David Lawson’s findings so the reader can begin to grasp what appears to be a relatively new type of crime. So new, in fact, that targets of organized stalking have great difficulty getting law enforcement officials to take it seriously.
Before sharing David Lawson’s findings, it should be pointed out that Lawson’s books contain two types of information: his observations, and his conclusions. David Lawson’s observations of the activities of the community organized stalking groups are a perfect match for the types of harassment reported by organized stalking targets. However, Lawson’s conclusions as to who is mainly responsible are puzzling to targets who have read his books. David Lawson claims that foreign terrorists and “anti-government” groups are responsible for the growing organized stalking crimes. Very few targets of organized stalking see evidence that Lawson’s conclusions match the targets’ experience. Lawson may have discovered those groups operating when he rode with the harassment groups, but anyone interested in finding the backers of local harassment groups would do well to suspend judgement on Lawson’s conclusions.
Right up front, targets of organized stalking report that LIES circulated about the targets are what fuel local hatred for the targets. One of the favourite lies being circulated is that the target is a child molester. This is routinely used against female targets as well as targeted men. Other lies are that the target has a serious criminal record, or is into the drug trade, or is a prostitute. So for those reading this paper who aren’t familiar with organized stalking, keep in mind that the obvious answer to “Why would people harass targets who are nobodies?” … is that once lies are circulated that the target is a major criminal, that target is no longer a “nobody.”
As to why certain people are chosen as targets, targets’ reports show that whistleblowers and activists are sometimes subjected to organized stalking as “punishment” for their activities.Other cases occur when a target is in line for a large inheritance, or has turned in a well-connected spouse for criminal activity such as pedophilia, or sometimes the target just “ticked off” someone who is well-connected to groups willing to do organized stalking. According to David Lawson, some targets are simply chosen for ‘practice.’ Here below are selected quotes from both of David Lawson’s books, starting with a “Concepts Table” for quick-click access to relevant sections:
Police awareness of organized stalkers
How David Lawson got involved
Characteristics of stalker recruits
Quotes from the stalkers
Stalker motivation statistics
Involvement of firemen and police
Stalkers’ attitude towards their cause
Stalking group leaders
Stalking group finances
Distinction, initial reasons vs. ongoing reasons
Lawson’s targeted group list
Sampling of stalking operations
Perps use adjacent apartments
Synchronized sounds
Stalkers entry into targets’ homes
Failure to recognize organized stalking
Vehicular harassment
Harassment on foot
Destruction of relationships
Noise campaigns
Synchronized movements (apartments)
Synchronized leaving home
Conclusion
SELECTED QUOTES:
Quotes are from David Lawson’s currently available book “Cause Stalking” except where noted from his original book, “Terrorist Stalking in America.”
Author David Lawson did interview perpetrators, (“perps”), targeted people (“targets”), and the police. Here is what the author heard from the police he interviewed:
[pg 79] “I also spoke with a few police officers from across the country. They confirmed the existence of stalking groups across the country. In general, they said that ‘cause stalking’ is primarily a civil problem where the plaintiff has to prove financial loss. They also said that there are free speech and grass roots issues involved. In fact, the police themselves are targets of these groups. In small towns, the number of members in these groups can easily exceed the number of police officers. In general, the police will not talk about stalking groups. One officer did say there is a storm brewing as groups become larger and more numerous.”Author Lawson explains here how he got involved and began to interact with the ‘cause stalking’ perpetrators:
“One day, several years ago, I was sitting in my house, and checking out the activity on my scanner. I heard a woman say that she was following a certain vehicle. She gave the location, the make and model of the car and the license plate number. A few days later, I heard the same woman on the same frequency (84) request backup at a certain location. A few days after that I again heard her broadcasting the position and details about another vehicle she was following. I listened to other people talking on that frequency and they didn’t give any indication that they were with any government agency but they were talking about arresting people. On another occasion, on the same business band frequency, I heard someone complain that an African American man was crossing the street. “All we could get him for is jaywalking” responded the leader. “Leave him for the police.”
People in the group would discuss where they would go for supper, after their shift was over, so I [the author] went too. I listened to a group of people openly discussing various activities as if they were the police. Real police officers were also sitting in the restaurant, listening to them. I later learned that their presence was not a coincidence. One man who had supper with the group drove a van marked with the call letters of a local AM radio station. I started listening to it. Most of the guests were people who said they had new revelations about Waco or Ruby Ridge, or had some inside story about government corruption. It is called hate radio. I also heard advertisements for the meetings of a local political group and I attended some.
“At the first meeting I attended, one young man flashed a phony police badge at me. No one paid any attention. Some of those in attendance were the people I had seen in the local restaurant. This was my introduction to the creepy world of anti-government extremists.”
David Lawson goes on to explain that he has observed “extremist groups” for several years while living in New York State, Florida, and Canada. He monitored the stalking groups’ public communications, attended meetings, and rode with them. The author defines the basic reason for being for these citizen stalking groups as CAUSE STALKING. Cause stalking means the group is assembled, under a leader with a “shadowy past”, for some specific cause. “Cause stalking has been used by extremist groups since the early 1990s. The basic system is alleged to have been developed by the Ku Klux Klan and refined through years of use.”
Some details about the typical cause stalking recruit: “Recruits tend to be blue collar workers who are at the bottom end of the job scale. They are janitors in apartments, hotels, etc., who have keys to get in any locked doors. They are security guards, who can let fellow members into places where they would not normally be allowed to go. They are city workers, who can, in many cities, follow a target around all day in their vehicles or have a noisy project underway near his [target’s] residence. They are taxi drivers, who are a network that is always on the road. They are cable, telephone and electric company employees who can interfere with a target’s service and spend time on patrol with the group, while they are on the job.” Those are the author’s words.
Here are a few quotes from the perpetrators themselves, from the original book: [From Terrorist Stalking in America] “We are like the police except we are ABOVE the police.”
[From Terrorist Stalking in America] “We are a citizen’s group that helps the police. We are trying to alert people in the area about this person [the target] before he gets to do what he did in the last place he lived.” [Eleanor White talking: All the cause stalking targets I know well did not commit ANY offenses. The stalkers are filled with LIES by their leaders.] [From Terrorist Stalking in America] “When I get the call, I go to whatever the address is. It doesn’t matter what they [targets] do, they can never get away from us.” [From Terrorist Stalking in America] “Who are we? We drive the ambulances that take you to the emergency room. When your house is burning, we put out the fire. We are security guards. We protect you at night. You only have electricity, phone and cable service because of us. We are janitors. We have the keys. We fix your cars. You don’t want to mess with us.”In “Cause Stalking”, David Lawson provides some details about the motivations of stalking group members not in the first book:
– 25% follow the nominal “cause” they were recruited under
– 25% actually participate in the harassment
– 75% harass occasionally or not at all
– 10% join out of fear of being harassed themselves
That 10% joining out of fear of harassment is quite interesting, as one of the most difficult barriers to educating the general public about organized stalking is why anyone would volunteer to harass others.
Lawson describes recruits to these groups as “… those who feel powerless, inferior and angry.” Common sense is that naturally, such people would be easy to recruit for street and adjacent to the target’s home harassment, but I would comment that lots of professionals put us (targets) down at every opportunity, declaring us mentally ill for even suggesting organized stalking is possible. These professionals don’t “feel powerless, inferior, and angry.”
And I doubt the many utility and city employees who participate feel “powerless, inferior, and angry” either. So while David Lawson has done a great job, some aspects of organized stalking have apparently escaped him. One comment Lawson makes is that “Firemen across the country, and even some police officers,
support these groups.”
I have heard a number of reports that vehicular harassment has involved an above average number of vehicles that bear stickers of firefighters, or, a few targets have traced perpetrator identities to firemen. One target discovered that a number of vehicular harassment cars, identified by license number, were parked in a police station parking lot.
My personal take on why some firemen and police might back these groups is that many have a heightened sense of community service. If they can be persuaded that the target has a criminal record, the worst case being that of a pedophile, it would be natural for firefighters and police to “help keep the target in line”.
The author concludes, as explained at a number of places in the book, that the “cause” the typical group is “working toward” is mainly an excuse to get the groups together. The main motivation of members who stay with these groups is the sense of power and belonging the group members derive. Having a “cause” enhances the feelings of power and righteousness, but group members, according to the author, are most concerned with how their fellow group stalkers feel about their “work” and accept them.
Lawson explains the attitude of the typical stalking group member towards the “cause” this way:
“Most active group members have only a general idea of the ideology of the group but they don’t particularly care.”
These groups come into being and are run by leaders. Here is what the author says about them in this book, a bit different and more clearly, when compared with the original book:
“Group leaders do have political goals and the belief that the end justifies the means.” Lawson describes leaders as considering their members “disposable.” Lawson states that some leaders work for corporations and politicians (original book didn’t mention politicians.) Lawson states that leaders identify targets but don’t directly supervise the harassment group members.
Lawson describes leaders as having an “air of mystery”, “having worked for the CIA, NSA, or some other intelligence agency that doesn’t reveal information about their employees.” Lawson states that this “background” is likely mythology.
How about financing these groups?
Although the author states that the pay is low, there are still very large expenses to harass people as thoroughly as targets report. Here is an example of what I mean by “large expenses”:
“Groups are well financed. They can afford to rent property wherever the target lives. If he drives across the country, he will be followed by supporters of similar groups in that area. If he travels by plane, group members will meet him wherever he lands in the U.S. They may even accompany him on a plane if they know his travel plan, and there is a good chance that they do.”
Here is what the author learned about their financing:
[From Terrorist Stalking in America] “The operations of many extremist groups are actually financed by corporations which use them to stalk their enemies or potential enemies.The groups are used as the private armies of those corporations. Some countries kill dissidents and in others they are jailed. In the United States, someone who is threatening to corporations or industries, like a whistleblower or activist, is likely to become the target of an extremist group.”The author makes several statements that these criminal stalking groups not only harass targets specified by their leaders, but also are FOR HIRE – a kind of “revenge service” for those wealthy enough to hire them.
There are two distinct reasons why targets are harassed:
– The initial reason targets are placed on the stalking groups’ “list”
– The reason the stalkers keep it up (always involves lies)
Those two reasons should always be kept separate in your mind, reader. David Lawson’s focus is mainly on the reason the stalkers continue to harass targets. David Lawson’s chapter on Selection of Targets may well be true, but it certainly doesn’t describe the thousands of people who don’t fit his list of targeted categories.
Here are some of the categories of targets Lawson records in “Cause Stalking”:
– Abortion clinic workers
– People guilty of mistreatment of animals
– County clerks and local politicians
– Police officers
– Judges
– IRS and Treasury agents
– Civil rights activists
– Government or corporate whistleblowers
One thing David Lawson makes clear in describing the targets is that “The ultimate goal of the groups is to destroy the targets.” Those who have been stalked by organized citizen groups which are fed lies report that these groups do destroy targets with great efficiency. Next, let’s look at some of the typical OPERATIONS these groups carry out. Here, I have retained a number of quotes from the original book because I feel they state the situation as well or better than the new book:
The first step, after a target has been selected, is to establish a personality profile “… which will involve an assessment of IQ, personality type, and history.”
“A target may also notice being photographed.”
[From Terrorist Stalking in America] “The primary characteristic of cause stalking is that it is done by large groups of people. A target will always be followed, but he is unlikely to see the same stalkers very often.”
…
[From Terrorist Stalking in America] “Many of these groups include hundreds of people.”
“Some authors refer to cause stalking as terrorist stalking.
Groups do not just stalk individuals. They employ organized programs of harassment which include breakins, property damage, assault and occasionally, even death. The children of a target are a favorite.”
[From Terrorist Stalking in America] “Firemen across the country, and even some police departments have a long history of supporting extremist groups. Fire trucks can sometimes be seen riding in extremist convoys, with their flashing lights turned on and their sirens screaming. They will also race to greet a convoy which is entering their town. The participation of firemen, city workers and utility company workers helps give group members an illusion of legitimacy and power.”
[From Terrorist Stalking in America] “City employees can be used to harass a target in many ways including tearing up the road in front of a target’s home. Employees of pest control businesses who have access to the keys for apartments and those who work for alarm and locksmith companies are also of interest.”
[From Terrorist Stalking in America] “Groups also attack targets of convenience. These people are selected because they are convenient targets, and not for any other reason. These include loners who tend to be more vulnerable to their harassment tactics than those with family and friends around them. Targets of convenience are used for practice.”
[From Terrorist Stalking in America] “In order to establish bases of operation, they will enlist the assistance of neighbors.
In many areas, they can do this by intimidation. Those who do not co-operate can be targeted, which includes harassment of their families and damage to their homes and vehicles.
“If they are dealing with individuals who do not know them, they can also appeal to their sense of patriotism and they can offer drugs, friendship, home repair, free taxi rides and whatever else they have to. In some cases they may even be able to get a key to the residence from a ‘patriotic’ landlord.”
[From Terrorist Stalking in America] “Surveillance is conducted 24 hours a day, 7 days a week. When a target leaves his residence they will alert the group, either by cell phone or by business band radio. Other members, who are patrolling the perimeter to watch for police and other vehicles driving in the area, will race to the location to begin pursuit. In small towns, where business band radio is widely used, these activities are a local sport among a small group. Anyone with a scanner can join in. Some targets have reported hearing an announcement on their scanners as soon as they turn their lights on in the morning.”
[From Terrorist Stalking in America] “In a typical apartment setting, they will attempt to lease, sublet, or otherwise have access to apartments above, below, and on both sides of the target. They will also “guard” the vehicles of a target in the parking lot.”
[From Terrorist Stalking in America] If [the target] flushes a toilet, he may hear a car horn honk, the sound of a power tool or hammering, for example. There will also be a large number of people coming and going, and accompanying rowdiness and noise.” [From Terrorist Stalking in America] “A common ruse used by these groups is that they are a ‘citizens group’ which assists the police and they are ‘just keeping track of’ a certain individual, for whatever reason. The illusion is reinforced by the case files they carry which are complete with photos of the target and look like those used by police.”
“During a search [of the target’s home or apartment] members who are on patrol anyway establish a perimeter around the residence to watch for police vehicles. In an apartment setting, entry will likely be gained through a member of the janitorial staff, pest control or alarm technician, since they have a right to enter.
They may even be able to approach a landlord and gain his co-operation, after convincing him of their ‘higher purpose’. He may also co-operate out of fear.”
[From Terrorist Stalking in America] “Others do not recognize that they are being harassed by an organized group. They just think that there are a lot of rude people in the world.”
“Interception of mail is standard practice.” … “Typically, targets notice that their mail is arriving late or they do not receive certain pieces of mail. They [targets] may overhear people at a nearby table in a restaurant talking about certain mail, and realize it is theirs, or someone may drive by [the target] waving their mail at them.”
“Interception of phone calls is also standard practice. This is done by telephone company employees who support the [stalking] group for ideological reasons or because they obtain some benefit.”
Eleanor White comment: I’d add to that one of the most likely reasons, because the phone technicians are told lies about targets.
“An objective is to isolate the target from his family and friends. He can tell them about all the strange things happening around him, but they will not understand and perhaps will think he is crazy. Sometimes other members of the family will receive the same treatment.”
“When a target is driving, standard practice is to surround his vehicle and attempt to control his speed. He will not be followed in close proximity by the same vehicles for a long distance. They do frequent trade-offs. Vehicles line up behind the target to take their turn.”
“In many parts of the country it is common to see groups of six to 30 or more vehicles driving around in convoys with their high beams on during the day. This is one of the ways a convoy can be identified.”
“Standard practice is to watch the target’s vehicles and this subjects them to damage including slashed tires, scratched paint, stolen license plates, etc.
Typically they would not cut the brake lines on vehicles or commit other similar acts of sabotage, but they would drain the oil or antifreeze over a period of time.”
[From Terrorist Stalking in America] “A target will be followed on foot wherever he goes. Anyone can go to the same public places he goes, and they will attempt to get into any other restricted places he goes, including hospitals, places of employment, etc. It has been said that it is possible to go nearly anywhere if you have a clipboard in your hand and it is almost true. They also like to wear name badges on a lanyard, and some carry phony police badges.”
[From Terrorist Stalking in America] “Common harassment tactics used by those on foot include pen clicking, in which they repeatedly click a ball point pen, key rattling, and rattling change in their pockets while standing behind the target.
Many tactics are tried and the result is observed. Those which evoke a response from the target are repeated. When a target sits anywhere in public, group members will attempt to sit behind him in order to create noise, by whatever means, including tapping their feet on the target’s chair. The objective is to harass the target constantly.”
[From Terrorist Stalking in America] “Groups attempt to interfere with any business and personal relationships which the target has. Typically, this interference involves character assassination from some anonymous individual and is not usually taken seriously by those who know the target. It can be effective with people who don’t know the target.”
“At work, the target will also experience character assassination. If he works in any position where he has to deal with the public, there will be a steady stream of customers who complain about him. If he is a real estate agent, he will have a steady stream of prospects who occupy his time but never make an offer.”
Let me, Eleanor White, give you an example of how brutal and serious this “character assassination” can be. One of our members, who prefers to remain anonymous, moved in with her husband and children to a house which, unknown to them, had been a methamphetamine lab. The chemicals used to brew meth apparently cause distinctive symptoms in the mouth. This family’s dentist felt he was “helping law enforcement” by reporting them to local law enforcement as meth users.
This was absolutely untrue, but the family didn’t even know the report had been made and had no way to correct it. (In fact, in some places, dentists are REQUIRED to report suspected cases of meth use.) Law enforcement in that area was apparently tied in to the citizen groups, and the family was harassed for many years. The husband died, apparently from exposure to these chemicals.
The lady, now a grandmother, steadfastly did detective work and eventually found out about her family’s reputation, with some help from a policeman who was a personal friend, from a different jurisdiction. This policeman admitted off the record that “meth mouth” can result in people being submitted to citizen harassment groups for harassment.
Character assassination is complete, and has life-destroying consequences!
“A common tactic use by groups is noise campaigns. Group members will drive by the target’s residence or work place, honking their horns, squealing tires, and making whatever other noise they can.”
“They will also make noise from whatever nearby properties they have access to. Typically, they will make noise when the target goes outside. Group members will also frequently knock on his door for whatever peculiar reasons they can dream up.”
“In an apartment setting, targets can expect to hear tapping on the walls in the middle of the night, hammering etc. from the upper and/or lower apartments, and possibly the apartments on both sides. They will continue to ‘work’ on these activities for as long as they can get away with them.”
[From Terrorist Stalking in America] “… It is not uncommon, in an apartment setting, for a target to hear someone moving from room to room as he does, from the upper or lower apartment. [Eleanor White talking: This requires commercial through wall radar or more advanced technology in many cases.]
“Often they occupy a nearby apartment, part time, when the owner is not there and he receives some benefit. A target may notice someone leaving a nearby apartment when he leaves his, and arrive when he arrives. In addition, he will often be accompanied in elevators by a steady stream of different individuals who go to the apartments being used by the group.”
What about the future, then? Let me close this review with a chilling quote from David Lawson’s first book, Terrorist Stalking in America, reporting what the author learned from some of the leaders:
“The leaders … are starting to balk at exposing their members to arrest for activities which amount to little gain for the movement. they say that anyone who is a target should be killed, and not just harassed for years.”
Eleanor White

Comments (0)