Appendix 217: Glossary of 452 Terms* Relating To Electronic-Netcentric-Neuro Warfare, Synthetic Biology, AI Precision Medicine, the Metaverses, & Targeted Individual (TI) aka Total Individual Control Enslavement-Torture-Murder-Transhumanism Program**
Glossary of 452 Terms* Relating To Electronic-Netcentric-Neuro Warfare, Synthetic Biology, AI Precision Medicine, the Metaverses, & Targeted Individual (TI) aka Total Individual Control Enslavement-Torture-Murder-Transhumanism Program**
Terms are mostly from military-intelligence ops and “black ops,” electronic-information-netcentric-cognitive and neuro warfare, electrical and biomedical engineering, telecommunications, computer science, neuroscience/technology, biophysics, & mathematics
*This glossary is a work in progress. These are DUAL USETechnologies!!!! (I.e., the same technologies and systems purportedly used to help (medical) are also used to harm (military and medical euthanasia).
** Inspired by Sabrina Wallace’s videos. Wallace states she is a former IT (Information Technology) professional and US military “black projects” experimentee (“DARPA noninvasive N2 survivor”). Glossary includes terms from other posts on this website added.
Sabrina Wallace’s channel: Psinergy Odysee channel
I. Epigraph Quotes:
Perspective of the wielders of neuro/bio/IT (cyber)/nano/quantum weapons systems as represented by Dr. James Canton, CEO of Global Futures, Inc. in a lecture to US SOCOM (US Special Operations Command) and the J-5 Donovan Group on the Havana Syndrome as “proof of concept” of application of nonlethal neuroweapons “in the wild:”
1) Neurotechnology/Neuroweapons: We are living in the proliferation of 30 different accelerated exponential technologies. The top game changer technologies for our civilization that affect everything from health care to defense to manufacturing are nano, bio, IT (cyber), neurotechnology, and quantum. Each of these has “dual use” (i.e., “light” and “dark” sides to help and to harm).
These 5 key technologies each create massive opportunities; nano, bio, IT (cyber), neuro, atomic. In order to look at all these together, we have to change the way we look at science. We are talking about manipulation of atoms and neurons.
Now we all live in Neuro-Moore’s Law: We have ever-shrinking, ever-more powerful devices. Neural nets at the core of AI involve over a trillion dollars of financial trading. Could “neuro” end up looking like “cyber”? Yes, “cyber” is a proven model. In fact, a product-line extension from “cyber” would be “neuro.”
Advanced neuro devices include “soft” (“nonlethal”) and “hard” (lethal) neuroweapons. The “soft” or “nonlethal” dimension creates dysfunctionality and cognitive impairment, inability to make good decisions, dizziness, health effects. The goal is to take parties out. (… I want him out of the game and I don’t him to be able to get back into the game.) Neuro-hacking includes the ability to create thoughts and blend it with AI. The “hard” dimension refers to killing people.
(Referring to the “Havana Syndrome” attacks on American diplomats at the Cuban and Chinese embassies): So neuro is likely a game changer, and it has much larger impact domains when it’s in the wild. Soft neurotech (non-lethal weapons) have many possibilities in “hybrid conflicts”. This is the new reality. These weapons have been deployed… these attacks were targeted and purposeful. This is a clinical trial in the wild. What are the diagnostics and devices we need to interdict and prevent these kinds of attacks? We need monitoring and sensing devices. Sensors alert through the icloud…. Then we interdict it. That’s an operational deployment.
(Webmaster: Canton implies, but does not state: So we need more taxpayer money to learn to defend ourselves from the weapons we have created and deployed.)
Dr. James Canton lecture to SOFWERX (US SOCOM-US Special Operations Command) & J5 Donovan Group, 2017 ( Neuroweapons, “Dark Network Supply Chains,” “Man-Hunting Business” (aka GANGSTALKING) & “Hybrid Warfare;” Presentation By Dr. James Canton (Video, Transcription, and My Commentary)
A Perspective of targets/victims of the neuro/bio/IT (cyber)/nano/quantum weapons systems:
2) “Computer networking through the human body. You are a node on a netcentric warfare kill network. Nobody said a word, they just went to work. dominating the electromagnetic spectrum of all photonic light.
Ever heard of bio-hacking? Did anyone tell you they had already put sensors inside every human being for body tracking? Did they tell you that you are node on a computer network attached to the cloud accessible to any little nerd, doctor, or hacker who knew how to access Zigbee and Bluetooth at 4cm with human body communication? Not a bit of this has anything to do with religion. We’re talking about capacitants, galvanic coupling, and wattage and voltage, amplitude, math, through the human body. Steganographic covert communications.
“On March 20, 2023, the ODNI (Office of the Director of National Intelligence) stated: “There’s no explanation for Havana Syndrome.” That means that there’s no such thing as SynChron and SynBio (these are companies) or synthetic biology as a science, or synthetic telepathy in Elsevier journals- and there are. So the ODNI gets to lie and these people get to die, while these people go to work.”
So all of you at the UFO community who continue to pretend that you’re oh so stupid and innocent, bullshit. You’re paid opposition. You’ve done a great job.. invading people’s houses at all hours of the night. You think you’re OK doing your podcast one day and the next day your lose all your shit and you’re homeless. Hackers too. It’s disgusting. Welcome to the UFO community, where it’s pay for play like everybody else with the sensor hunters.
Dr. Steven Greer (of Disclosure Project) presents information (to Congress) about selecting humans for psi capabilities, called psionics, i.e., illegal projects run for the purpose of communications; most subjects die, taken because of their abilities to communicate with the speed of thought, which is faster than light molecules.
That was in Greer’s interview with Congress….. you let them get away with it because you didn’t tell them about the human physiology involved, the biofield, the aura. And if humans knew that their body part had been stolen, attached to the cloud, and a remote handed to FBI, DHS, whoever paid for it, they’d be pissed. And we’d have a lot less people interested in UFO groups and a lot more interested in how do we slow this down and do something, because this is completely out of control.
They’ve been giving people jobs all along. Walking right through the body. Using math to get it hooked up with basic Python, AI nodes; these wireless sensor networks, wrap them around somebody, it’s biosensors on the inside, outside in, inside out, shake the hell out of them, electrically or otherwise, do whatever you want to them. How is that possible? We lie to people about their body part (biofield), about material physics, about telemetry and RF bands used by the Medical Implant Communications System telemetry by law…. That’s why we’re in this position.
What is the human aura (biofield)? That’s what we use in Information, Surveillance, and Reconnaissance with the electrical homeostasis of the human body so that we can pertebate and make changes for precision AI health care, the internet of behaviors, the internet of bodies, the internet of things, the industrial internet of things, the internet of medical things, the medical body area network, the wireless body area network, the metropolitan area network, the campus area network, and the ultra-wide band radio frequency communications and optigenetic networks for neuro modulation.
Wow.. You just said it doesn’t exist. Yeah, it doesn’t exist for anybody but us to play with you like a sim in a video game.
Re: the High Accuracy Detection Multi-Domain Sensing System, Dennis Teefy (Projects Director for Sensors Aerial Intelligence), from the Army states in C4ISR.net Sept. 14, 2022 magazine: “The goal is to provide deep sensing intelligence collection of indicators, warnings, and electronic order of battle and patterns of life for target development. (High Accuracy Detection Exploitation System (HADES)). The Multi-Domain Sensing System (MDSS) High Accuracy Detection and Exploitation System (HADES) will be GLOBALLY deployable and provide a multi-faceted sensing capability at higher altitudes and longer ranges.” I know what HADES is.
It’s all just electronic warfare. “Pay for play.” We are killing with computer networks. Network killing IS their system.” Sabrina Wallace,
from: (To the new commenter .. Nov. 8, 2023 and Biosensors , Sensor Hunters and Electronic warfare inside human tissue/C4ISR w/usaf, Cisco control plane for E.B.Es – Engineered Biological Entities – (WBAN) 802.15 IEEE – EXPOSING THE SENSOR HUNTERS! )
3) “The public has zero comprehension of this. This is a deeply engineered system of engineering your tissues from the inside out (aka wireless tissue engineering with graphene).”
“Your body (Wireless Body Area Network; WBAN; biofield; aura) IS the weapon. No cell tower or nano required. (“Because photons generate within you. You create them and they propagate out on the wave of your DNA.)”
These are biophotonic frequency weapons that have been deployed and tested… in signals intelligence, we don’t hone you, we hone your environment.”
Biophotonics: That is your prana, your chi, the study of optical processes in biological systems, both those that occur naturally and in bio-engineered materials. We have radiated the biofield and we have all this optics, light sourcing, that’s what’s really been going on since the 1980s. And the mind wars are network segmentation of this body part (biofield/WBAN). Why are they doing this? Enery harvesting.”
They root around in REAL TIME in people’s veins and arteries because that is how the hardware (MOSA; Modular Open Systems Approach) and software (SOSA; Sensors Open Systems Architecture) work (for COMMAND and CONTROL with the Pentagon’s DISN, Defense Information System Network and ISR, Intelligence, Surveillance, Reconnaissance).”
“We really need people to understand that these are jobs. And that there are people going to work in these jobs, some of them are very young.”
“They use video game controllers to play real people like sims (the video game).”
“They gave the guys in the white vans jobs and a pension (the “guys in the white vans” were formerly the pedophile CIA “Finders” and now are the Signature Reduction Force).”
“It’s not a vaccine if it requires graphene… because they are using your body area network, aka you and your DNA, to route data. You are the network. You are a node on the network.”
“They injected people with graphene without their knowledge and grew nano-tubes inside of them. You got injected with graphene to become a better conductor because we love you, we need your energy, and we harvest you.”
Nobody ever needed a remote to your central nervous system for national security. And we’ve been playing with people, straight up playing with people.
Electronic warfare: That is what the SMART Grid, Agenda 2030, the SMART City Inititative, the 6G low Personal Area Network (PAN), all of it, is on these (intrabody) biosensors and the Body Area Network. The body is the network, the body is the node. The body is what they are using.
The government has no right to tell people they are crazy while they are electrocuting them. Hello? It’s been YOU the entire time making sure that nobody can use their natural empathy, precognition, and and then playing sims with human bodies in libraries and data bases. BIL the brain imaging library. They’ve been reading your thoughts with cognitive warfare technology at Georgetown University since 2007.”

Sabrina Wallace, from: Psinergy singage w dr ana and maria zee October 11, 2023
What is WIRELESS tissue engineering?
4) “Welcome to computer networking through the human body. I held a very high-powered job on the back end of Northcom (US Northern Command) and the University of Wisconsin. I was disabled almost 20 years ago for them to continue doing horrible testing on me. I am very aware that soft-ware defined networking is why they are doing this. I can explain who is using these systems with that cute little (EEG) head set, and how over internet protocol networks, the same internet your phone uses, the same IEEE working groups as your phone, these different systems are all using internet protocol networks, netcentric warfare, to hunt you down by that body part, your biofield, because that biofield is a node on an internet protocol network accessible to all these people who pay money for data base access to your body for Information, Surveillance, and Reconnaissance. It’s called applied signals technology with high accuracy detection exploitation system for ISR, SOSA, MOSA, and OSA with synthetic biology and transhumanism. People need to understand that their body itself, not their cell phone, is tethered to the cloud.
… We are energy harvesting from the human body. Radio frequncy and all sorts of things. That is your new green energy, Soylent Green, the new energy is YOU. As you move, as you breathe, (there is) leakage of radio frequency because it runs through humans all the time.
… These are soft-kill weapons systems.”
Sabrina Wallace, from: Psinergy singage w dr ana and maria zee October 11, 2023
5) “The development of databases with characterized standard biological circuit parts with known functions and behaviors, e.g. BioBricks, and tools to combine them into more complex designs [6], are pushing synthetic biology to a future development similar to that experienced by integrated electrical circuit design in electronics. As a consequence, engineers will be soon able to gain full access to the functionalities of the aforementioned cells’ elements, and reuse cells and their features, without requiring an in-depth knowledge of biotechnology. One of the latest frontiers in synthetic biology is the development of artificial cells, enabled, among others, by tools from nanotechnology. Artificial cells have minimal functionalities and structural components compared to natural cells, and are assembled bottom-up by encapsulating the necessary elements into either biological or fully synthetic enclosing membranes [7]… Although still in its infancy, this technology has been successfully applied, e.g. for drug delivery, gene therapy, and artificial blood cell production, and it is expected to deliver ideal substrates for synthetic biology with a more predictable behavior.”
From: Pierobon, M., et. al., The Internet of Bio-Nano-Things, IEEE Communications Magazine, April, 2015Pierobon, M., et. al., The internet of bio-nano things, April 2015, IEEE Communications Magazine
6) Wireless tissue engineering and the cognitive warfare problem has to do with the Industrial Internet of Things. Because everything you see in the Wireless Body Area Network listing (below), they’ve had the ability to do through your tissue, legally, since 1995. The Medical Body Area Network was mandated in 2014 by your Federal Communications Commission (FCC) to do everything you see here.
Who are these physicians? Your IEEE engineers. Biomedical wireless tissue engineering. IEEE (Institute of Electrical and Electronics Engineers) of biophotonics and cognitive intelligence (points to chart). That’s your C-40 city. What’s it going to do to you? Totally control you down to the bone marrow. Oh, but I’m going to lift my gun. No, you;re not lifting shit. Fed by electromagnetic algorithms and techno-metrics since the 70s.
And you can bet we’ve got the rectennae shit all worked out, that Smith Wheel access between the SMART meter and anything else because we got AI precision health care worked out with the biosensors, routing data directly through the body. I don’t get it. They put your ass on the cloud and made you accessible through the various levels and layers of literal computer networking the same way we network machines. So somebody went to work and somebody got paid. And then they issued multiple layers of security with different divisions.
Fuck you. You’re not that stupid, you’re just well paid. Biofrequency weapons on a 28-year old technology that the UFO people refuse to talk about. They’re two year olds. They are used to getting away with murder and torture and getting rewarded for it. Because nobody will tell what they do at their jobs. The better they gas light the more they are rewarded.
II. Webmaster’s (Extended) Introduction: Most Targeted Individuals (TIs) are familiar with terms like TI, organized stalking-electronic harassment (OS-EH), perpetrator, handler, surveillance role player, spotter, tracker, street theater, FBI/DHS Fusion Centers, Terrorist Screening Data Base (TSDB), etc. Well-informed TIs also understand that terms like “CIA no-touch torture,” “Phoenix Program,” CIA’s MKULTRA Project, Zersetzung, transhumanism, cybernetics, Operation Gladio, etc., also have direct bearing on the targeting program. I have already compiled a list of some 345 synonyms and terms for organized stalking-electronic torture: Cutting Through “Smokescreen Terminology:” 345 Names & Descriptions Reveal Truth Of Gangstalking War Crimes/Crimes Against Humanity.
Even better informed targeted individuals (TIs) are familiar with the military and neuroscience terminology associated with acknowledged military-deep state projects, as outlined in lectures to special forces and other military personnel by DARPA-Georgetown Neuroweaponologist, Dr. James Giordano and Global Futures CEO, Dr. James Canton posted on this website:
Drs. Giordano and Canton’s lectures, to me, amount to highly revealing and accurate descriptions of the neuroweapons-hybrid warfare systems that military-academic-corporate and possibly criminal actors are deploying against targeted individuals. However, while these posts reveal much about “what” is being done, many questions still remain about “how” these technologies operate and are being deployed.
I suggest that the terminology and information proffered by Sabrina Wallace, ex-computer network engineer and former government black projects test subject, add major insights into “how” hybrid warfare and neuroweapons technologies are deployed against civilians. Whereas Drs. Canton and Giordano provide a general schema of military neurowarfare capabilities, Wallace offers in-depth descriptions of the specific operations and technologies that may be involved. In particular, she helps us understand how computer networking, electronical and bioengineering, and AI precision health care systems operate together, hand-in-glove, with these military weapons systems.
Why a new glossary? Because TIs and most of the public are severely handicapped by our lack of familiarity with the technical terminology, aka jargon, associated with these complex electronic warfare, neuro Science/Tech (S/T), bio-medical engineering, and computer science systems. Indeed, our ignorance of this jargon could be our collective undoing, particularly as these “dual use” technologies appear to be ushering in a new transhumanist era of enslavement.
Sabrina Wallace’s videos offer the most comprehensive description of the targeting “technologies” I have yet encountered. Her mastery of these subjects and her ability to explain them are quite impressive. This information could provide the “Rosetta Stone” (key) to help TIs and others better understand the targeting systems being deployed against us.
Her videos are featured on the following posts on this website:
I’ve now watched and posted over 80 of Sabrina’s videos. Most of what she says rings true or at least highly plausible to me based on the research I’ve already done. She supports her assertions with scientific, medical, and military papers, graphs, charts, and figures. Her rapid-fire presentation style will impress some as quirky, to say the least. But I postulate that Sabrina could be “for real” and correct in her major conclusions. If so, she is doing an important service for humanity and we need to learn as much as we can as fast as we can from her.
I cannot confirm all of Sabrina Wallace’s information or her assertions, however. Indeed, it is possible she is a cyber-warrior/cyberstalker whose mission is to “poison the well” with a combination of valid information and disinformation. (See Part IV for a discussion of my concerns along these lines.)
However, the bottom line for me is that the system of wireless body area networks (WBAN), biosensors, and electromagnetic frequencies that she describes may indeed be the system under which we are now living. Indeed, this (WBAN-biosensor-RF) system is now so advanced, militarized, industrialized, medicalized, commercialized, and criminalized that billions to trillions of dollars of “market share” are invested in it, as both Drs. Canton and Giordano indicate in the above mentioned lectures.
Wallace does not specifically mention this, but her information also validates my thesis that targeted individuals (TIs) are and have been the involuntary test subjects for the development, testing, and deployment of these systems for generations. These systems now incorporate: 1) military electronic and neuro weapons, 2) biomedical engineering systems, and 3) the “total individual control” deep surveillance-torture-murder-enslavement system that seems integral to the UN Agenda 2030 SMART city system.
Thus, I suggest the information Wallace presents might provide the “missing links” that explain:
1) the technological underpinnings of the TI program- which New Zealand journalist/activist/politician and TI, Suzie Dawson, referred to as the “NSA Global Spy Network’s” “architecture of oppression” ( Suzie Dawson 10-Part Video Series: “Opening the Five Eyes: Exposing the Spies” of the NSA Global Spy Network (Fall, 2019) W/ Transcriptions, Graphics, & Sample Quotes).
2) World Economic Forum globalists’ references to: “under the skin surveillance.” This helps explain Yuval Noah Harari’s outrageous comments such as: “Humans are now hackable animals. The idea that they have this soul or spirit and they have free will and nobody knows what’s happening inside me so whatever I choose, this is my free will. That’s over.”
3) the scientific basis of Bill Gates’: 2) Microsoft’s 060606 Total Enslavement Patent ((Bill Gates’ Total Enslavement Patent) 060606 – Cryptocurrency System Using Body Activity Data (& videos); Plus H.R. 666 (Anti-Racism in Public Health Act) & H.R. 6666 (COVID-19 Testing, Reaching, And Contacting Everyone (TRACE) Act)).
Hence, this 60+ year-old electronic-netcentric-cognitive-information warfare system apparently underpins:
1) the NSA Global Spy Network and DoD-NATO electronic/netcentric/cognitive/neuro warfare system,
2) the industrial, AI-driven precision health system,
3) the global targeted individual program,
4) the Covid jab as bio- and technological weapon and mechanism to expand “throughput” capacity of our wireless body area network (WBAN), i.e., our biofields,
5) the globalists’ eugenics and technocratic, transhumanism, bio-robot enslavement programs.
The following glossary, then, based largely on terms that Wallace utilizes, is augmented by terms utilized by other sources, including the video lectures by Drs. James Giordano and James Canton (see above), Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com), Wikipedia, and a number of other posts on this website.
The major “headlines” here are that the following generally unknown and/or misunderstood realities undergird this system*:
1) The Wireless Body Area Network (WBAN) aka “human biofield,” “aura,” and “body electric” is an essential body part of all humans that accounts for about 80% of the immune system and 50% of the endocrine (hormone) system. However, for the past 150 years its existence has been strategically denied, for all practical purposes, by those whose intention is to use it to achieve total global population control.
2) Scientists have made tremendous and largely classified advances in transhumanism/cybernetics over the past ninety+ years and in electronic warfare (EW) over the past sixty+ years.
3) In-body biosensors that incorporate our own cell tissues are already installed within us from the air we breath, food and water we ingest, and “vaccines” we have taken.
4) There has been total military weaponization of the electromagnetic spectrum.
5) The human biofield (WBAN) is hackable from a distance using the 802.15.4/5/6 I.P.(Internet Protocol) address at the 2.4 THz frequency. American citizens already have “digital twins” which are used in military computer war-gaming simulations and are already electronically attached (tethered) to “the cloud.”
6) People are paid to log into and bio-hack us electronically. These people play video games with our biofields, minds and bodies without our knowledge and consent, with no external oversight. Cyber warriors at their computer stations can pilot us like SIMs (Subscriber Identity Module) toward the goal of controlling us.*
7) About half the US population have jobs that support this system, although many are presumably ignorant of the how the entire system works.
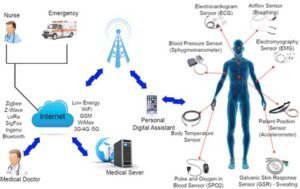
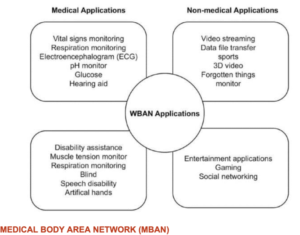
8) Medical applications of the WBAN (wireless body area network) include remote (noninvasive) monitoring of vital signs, respiration, electroencephalogram (EEG), pH, glucose, and muscle tension as well as hearing aid, disability assistance, speech disability, and artificial hands.
9) Non-medical applications of the WBAN include video streaming, data file transfer, sports, 3D video, Forgotten things, monitoring, entertainment applications, gaming, social networking.
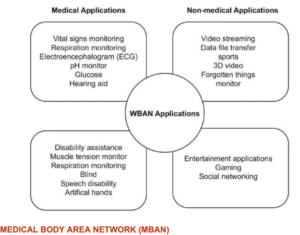
Capabilities of WBAN since 1995
10) All this explains how TIs who are blacklisted as “terrorists” are covertly tracked, hacked, and subjected to no-touch electronic torture and electrocution for the purposes of covert biomedical engineering and weapons testing, revenge, torture voyeurism, radical gaming, entertainment, video streaming, etc.
* Targeted Individuals: Please note that these 10 points appear to explain the scientific basis and backbone for both the global TI (organized stalking-electronic torture) AND Covid injection programs.
Sabrina Wallace also maintains that metamaterials such as graphene were injected into the majority of the population via the Covid jab because a bigger backbone, i.e., more “throughput” capacity, was required for these electronic warfare/WBAN/AI Precision Health Care systems. This assertion corroborates those of La Quinta Columna (Intra-body nano-network ) and the research of Mik Anderson and others. See the following diagram of how the intra-body nano-network functions:
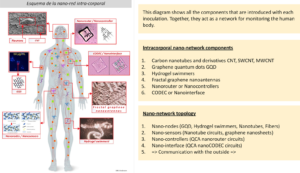
Also see:
The following statement by Wallace, which she makes near the end of the above video, summarizes some of her main points**:
(** These insights suggest that Operation Crestone/Baca may be a human laboratory for the testing and development of these electronic warfare and mind/behavioral control systems. Note that these operations are particularly applied to and tested on those classed as “star seeds” and “terrorists” who generally do NOT have the (computer) tech background necessary to understand this system. I suggest that meditators, contemplatives, energy workers and New Age psychics of Crestone/Baca are also of particular interest to the military-academic-corporate devils who weild these systems against unsuspecting civilians.)
Summary Statement by Sabrina Wallace:
“The heart of surveillance is the human biofield…..
One hundred and fifty years ago they told people the ‘human biofield’ does not exist… (Meanwhile) they get to work with the biofield inside computer networking and put you (your biofield) on the Cloud in a body area network and then send electrical signals to your central nervous system, not only to make you believe and hear whatever, but also to augment your tissue growth, wireless tissue engineering, biomedical tissue engineering (transhumanism), or just electrocute you from the inside out and get rid of you.
They get to label and decide who a “terrorist” is and once they do that they enter that data into a massive computer system. Then the industrial cyber-physical backbone on the kill net of ‘network killing’ might just make the decision that you are a “terrorist…” Because you are not allowed to talk about the biofield. It’s their job to control that electrical body part. It’s made of you. The biosensors (inside you) are made of you; your enzymes, your DNA, your antibodies, your tissue…
They get to take it (your biofield) away and call you a crazy loon. Drug you. Test on you quietly and secretly, as a “Star Seed,” and then they feed that (data) into the data bases. Which is why when I get to “ORION node operator” I’m right back in the same things I saw as a kid (experimentee) in black projects (beginning in 1979). They’ve got us differentiated by our DNA. It’s a eugenics program. They are on the back end of software-defined networking ready to go with the genetics of however they want (us) to perform.
Liquid neuromorphic network translation. I warned people, they are going to pull the neurons right out of your body and put them into their friends in the white suits (scientists and doctors)….
Why would they be doing that? Because these creatures in charge are inter-dimensional (i.e., nephilim). The only way to “kick their ass” is that human body part, the biofield. So they have to make sure they’ve got it locked down. And those with any real psionic abilities (telepathy, empathy, precognition, etc.) won’t be using them because you’re going to think you need a wearable. OR you’re going to get yourself injected with the new graphene shot that makes it easier to run all this data through your body. And that’s why they need everyone graphenated. They need a wider backbone. Which is why they did all this (COVID jab). Wireless sensor network, mobile ad hoc networks, your 802.15.5 (IP address) on the fly, to manipulate your ass all day, electrically.
So, anyone still believing in “Star Seeds” and all that garbage, you had better learn about the CISCO software-defined networking we use through human bodies, or you are the first people on the list to be targeted for transhumanism because you have neurons that have natural telepathy, empathy, and precognition that they subsume as a matter of their job, their patents, and their N-sphere map. You are not going to another star system. I’m sorry. You are going into a liminal space, The Rydberg-atom toroidal field. We know how to modify everything within you at every density. And we have all chakras locked down with little lenses that report back and forth to those neurtrino-opto-electronic arrays in Antarctica and everywhere else with the doppler and everything that we watch with radar.**
This is math on steroids. They are logging in to your body. You have to admit that you’re electrical…. I come from black projects and mathematicians on my family’s side, so I know how they do it.
(The CIA people that are doing all this) are just having a good time. Their whole schtick is to kill people electrically without you ever knowing how. Then they can tell you “aliens,” which is whatever they want, and you’ll do what they say. What could be more disgusting and a more cowardly way to kill people than to just send a signal while they are laying in their bed or sitting in their home? We should be talking about electronic warfare shielding…
Network killing IS their system.”
III. Glossary
SW = Statement by Sabrina Wallace
Dr. JG = Statement by Dr. James Giordano
Dr. JC = Statement by Dr. James Canton
1. 4D CBRN Skiffs: According to Sabrina Wallace (hereafter SW):, Chemical, Biological, Radiological and Nuclear (CBRN) skiffs are made of your DNA. These protect the elite from their own bioweapons for prima materia, hence skiffs are “bioweapons secure.”
2. 5th Generation Warfare: The TI Program, Civilian Targeting, Electronic-Netcentric-Cognitive Warfare.
3. 6G Cognitive Radio Network (CRN): A 6G network is defined as a cellular network that operates in untapped radio frequencies and uses cognitive technologies like AI to enable high-speed, low-latency communication at a pace multiple times faster than fifth-generation (5G). networks. SW: This is how your body is hooked to the Cloud.
4. 6G Cognitive Radio Network Body Access:
5. 6G LoWPAN:
6. 6G Radio Network Tech Dock:
7. IEEE (Institute for Electrical and Electronics Engineers) 802.15.4 Working Group:
8. IEEE of Biophotonics:
9. IEEE 802.15 Working Group: SW: That’s your aura (biofield). Electronic/drone warfare is using your aura.
10. ABMS (Department of the Air Force’s Advanced Battle Management System) Platforms: SW: Control autonomous vehicles, autonomous drones, tanks, regular strikers, planes, industrial internet of things, VA nets, self-driving vehicles. And it’s all LIDAR.
11. API (application programming interface): Wiki: is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software. A document or standard that describes how to build or use such a connection or interface is called an API specification.
12. Adaptive modulation communication (AMC):13. Adversarial Neural Network (ANN): See: Microsoft’s: Modeling and Simultaneously Removing Bias via Adversarial Neural Networks (2018) by John Moore*, et al.
14. AI (Artificial Intelligence): SW: We’ve had AI since 1954, Dartmouth, Project Salus, watching the back end of Northcom. Dashboard. Common operational picture.
15. AI (Artificial Intelligence) Precision Health Care:
16. AI (Artificial Intelligence)-DoD Symposium (Sept. 10, 2020): SW: Project Maven is being instituted with SMART sensing, Agile Pod Conduit (APC), ABMS, tethered to ground is a digital nervous system, Project Salus. People can be sold into “the program” by “pay for play” military. $30,000 for normal and $45,000 for aerospace uses (that is, soft kill no touch torture and murder).
17. AI in IIOT (Industrial Internet of Things): Includes Real-Time Intelligence (RTI), Ambient Intelligence (AmI), Swarm Intelligence (SI), Cognitive Intelligence (CI).
18. AI-Supported Netcentric – Mosaic Warfare: Wiki: The Internet of Military Things is a class of Internet of things for combat operations and warfare. It is a complex network of interconnected entities, or “things”, in the military domain that continually communicates with each other to coordinate, learn, and interact with the physical environment to accomplish a broad range of activities in a more efficient and informed manner. SW: Used in conjunction with Project Maven.
19. Android software:
20. Anduril: Defense technology company Anduril Industries today announced it was awarded a $967,599,957 Indefinite Delivery Indefinite Quantity (IDIQ) contract with U.S. Special Operations Command (SOCOM). Anduril’s Menace (software) can serve as an expeditionary operations center, with a handful of computer stations inside allowing battlefield commanders to track where friendly and enemy forces are at any time, and then issue orders to their troops, Zachary Mears, head of strategy for Anduril, said in a Wednesday interview. Commanders could also manage base defense and security, counter-drone efforts, and maintenance and logistics using Menace, according to the company.
21. API (Application Programming Interface): A set of defined rules that enable different (computer) applications to communicate with each other. It acts as an intermediary layer that processes data transfers between systems, letting companies open their application data and functionality to external third-party; a way for two or more computer programs to communicate with each other. A type of software interface, offering a service to other pieces of software. A document or standard that describes how to build or use such a connection or interface is called an API specification.
22. Applied Signals Technology: SW: Includes SOSA (Sensors Open System Architecture), MOSA (Modular Open System Approach), and HADES (High Accuracy Detection Exploitation System) deployed on drones for military command and control (C4ISR).
23. Artificial Neural Network (ANN): Artificial intelligence uses a technique called artificial neural networks (ANN) to mimic the way a human brain works. A neural network uses input from datasets to “learn” and output its prediction based on the given information.
(Webmaster comment/questions: i.e., Are the data sets used for targeting and harassment of targeted individuals? Does data derived from targeting individuals help expand the data sets?)
24: “Assessment” technologies used to acquire “viable targets” (targeted individuals) and “avoid collateral damage (according Dr. J. Giordano):”
a) neuro-imaging techniques, including computerized tomography, single-photon emission tomography, a highly specific electromagnetic (EM) pulsed signal to image brain areas and “tracks” (communicating networks and nodes within the brain) in a directional way in rapid time,
b) neuro-physiological recordings such as electro-encephalograms (EEGs) in combination with quantitative techniques,
c) use of neurogenomics and genetics; neurogenetic profiles of individuals and groups to see what genes are coding for certain structures and functions of the brain,
d) neuroproteomics and other forms of bio-markers, and
e) neuro-cyber informatics– with computer applications is useful in manipulating what kinds of information are delivered to the brain.
25. Atomic magnetometers: Are also referred to as ‘optical magnetometers’ (OM), since the magnetometric information is encoded into optical signals, or as ‘optically pumped magnetometers’ (OPM), since optical pumping is an essential feature of the magnetometers’ operation.
26. Aura: The human biofield (aura) is actually a body part aka wide (wireless) area body network (WBAN).
27. Automated targeting:combined with algorithms that watch for target signatures this creates the means to spot targets on the fly. It creates the means to spot targets as small as humans and to kill them within minutes. See: Drone kill communications net illustrated by Mark Ballard, 2014, ComputerWeekly.com.
28. Astral plane: SW: Is really the CISCO backplane on the MANET internet of things. You will be manipulated into submission electrically on the Internet of Things (IoT) from the inside out because you are part of the IoT. This is wireless biomedical tissue engineering and transhumanism.
29. Astral Projection:SW: This is BS. It’s the Cisco backplane that is being used for brain-colon-brain connectivity/wireless communication which equals neuron exchange.
30. Auto-immune disorders: SW: Include Chronic Fatigue Syndrome (CFS), Fibromyalgia, Lupus, Pseudo-Tumor Cerebry. These never go away due to actually deriving from being electrocuted electromagnetically via this system.
31. Autonomous systems: Defined by DOD as the DoD in DOD Directive 3000.09. SW: I.e., We have a “pay for play” system rather than a US military anymore. The title of 2007 Pentagon document: “Department of Defense Global Information Grid Architectural Vision: Vision for a Net-Centric, Service-Oriented DoD Enterprise” tells all. “A Net-Centric, Service-Oriented DOD Enterprise” refers to the fact they have sold their “services” to wealthy private interests and no longer serve the American people.
32. Backpropagation Algorithm: During the 1980s, David Rumelhart, et al., revolutionized neural network research by introducing the Backpropagation Algorithm, a method for efficiently training multi-layer Neural Networks. This paved the way for the development of Deep Learning, significantly impacting the field of artificial intelligence by enabling the training of complex, multi-layered neural network models.
33. BAD (Body Area Device) BAN (Body Area Network) Security:
34. Base Station: A central connection point for a wireless device to communicate. It further connects the device to other networks or devices, usually through dedicated high bandwidth wire or fiber optic connections.
35. Betel (Bechtel?) Corporation: SW: Partners with DARPA to develop these systems.
36. BIG DATA: (meta-data) is a “force multiplier” in neuro-science and neuro-weaponology. Large volume data banks, include:
-Individual, cohort, and population data tiers
-Intra- and inter-tier integration potential
-Longitudinal input requirements
-Rapid (real-time) access requirement
– They must be: scalable, customizable, accessible, sharable, secure (deal with stackability-hackability issues)
37. Bio-API: SW: “The common enemy’s greatest weapon. Include communication between nano-bio-sensors, Internet of bio-nano Things, spying networks formed inside the body that can be used to cause harm. Can be used in health care applications, telemedicine, etc.”
38. Bioconductor:
39. Bio-cybernetic communication: The Advanced Research Projects Agency awarded a contract to the Stanford Research Institute (CSRI) to determine the feasibility of bio-cybernetic communication in 1972. The research concluded that the EEG reveals similar responses during silent reading to that during overt speech and that these responses may be classified correctly by a computer with a high degree of accuracy. This opened the gate for Mind Reading. (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
40. Biodigital Convergence: Describes the intersection and in some cases merging of biological and digital technologies. Biodigital technologies include mRNA used to treat Covid-19, digitally controlled surveillance insects, genetically engineered microorganisms.
41. Bio-digital Enslavement System: SW: This Fourth Industrial Revolution system.
42. Bio-electronic code:
43. Bioelectromagnetics: Dr. William Ross Adey demonstrated that Radio Frequency Electromagnetic Fields affect Voltage-Gated Calcium Channel during the 70’s, and thereby laid the groundwork for the development of the field (from: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com)).
44: Bio-electromagnetic SMART Grid: SW: Is attached to you and your home
45. Bioelectromagnetic algorhithms: SW: Are going to take over.
46. Bioelectronics: a multidisciplinary field which integrates biology and electronics for diagnostic and therapeutic healthcare treatments. The regulatory activities of the nervous system can be monitored and controlled with bioelectronic technologies that affect specific molecular processes in neural signaling. Applications include electrocardiagraphs, cardiac pacemakers, and defibrilators, blood pressure and flow monitors, and medical imaging systems.
47. Bio-electric hacking: Hacking of biofield for regenerative medicine or electronic warfare purposes (dual use applications).
48. Biofield: Large field of energy comprised of electrons and ions that surrounds and extends out from the body about 8 feet. Not visible but can be felt with the hands, often through pressure or temperature changes. SW: It is a body part; it is part of you. The DNA wave-propagated body part is made of photons that you generate inside of you with your cerebral spinal fluid.
49. Biofield Analysis (BA): independently developed field of research for diagnostics and therapeutics of human health. (See: “New Frontiers in Medical Biometrics, Diagnostics, and Therapeutics: Biofield Analysis and Medical Body Area Networks,” 2023, Published by IEEE)
50. Biofield Analysis Device (BAD): SW: a cell phone.
51. Bioinformatics: A hybrid science that links biological data with techniques for information storage, distribution, and analysis. It supports multiple areas of scientific research, including biomedicine, genomics, proteomics, and metabolomics.
52. Bio-frequency weapons: SW: Can produce augmented humans.
53. Biomarkers: Biomarkers, as used in the medical field, are a part of a relatively new clinical toolset categorized by their clinical applications. The four main classes are molecular, physiologic, histologic and radiographic biomarkers.
54. Biomedical engineering: The application of the principles and problem-solving techniques of engineering to biology and medicine. Includes regenerative medicine, life-extension technology, immortality and anti-aging research. Includes radio wave communication and Bluetooth signal snooping device at 5 m and human body communication (HBC)
55. Biomedical Wireless Tissue Engineering: SW: Used to advance the SMART City agenda. As of 2013, the IEEE (Institute of Electrical and Electronics Engineers) are your new physicians with this system.
56. Biometric data: We (military) put an individual’s biometric data into data bases (Dr. JG).
57. Bio-mimicry: SW: How computer science (cyber security) can learn from imitating nature’s patterns of why, what and how.
58. Bionomics: ecology
59. Biophotonics: A combination of biology and photonics; photonics is the science and technology of generation, manipulation, and detection of photons, quantum units of light. Photonics is related to electronics and photons. An emerging multidisciplinary research area embracing all light-based technologies applied to the life sciences and medicine. SW: They use biophotonic steering with metamaterials such as graphene.
60. Biophotonic probes for biophotonic imaging:
61. Biophysics: Applies the theories and methods of physics to understand how biological systems work. Biophysics has been critical to understanding the mechanics of how the molecules of life are made, how different parts of a cell move and function, etc.
62. Biosensors: short for “biological sensor.” SW: Made out of a transducer and a biological element from your body such as an enzyme, an anti-body, or a nucleic acid (DNA). Biosensors interact and the analyte being tested and the biological response is converted into an electronic signal by the transducer. Biosensors don’t go away and can’t be re-programmed. It’s an industrial system. This is a key part of the electronic warfare system that has been around for nearly 70 years as biosensor testing and deployment began about 1956.
Dr. JG: Bio-sensors indwelling within targets can be uploaded (and read) remotely, yielding telemetrized information. This technology applies to RFID chips and the monitoring of key biological variables used in health-information data bases which can also be used for population monitoring, tracking and identification, etc.
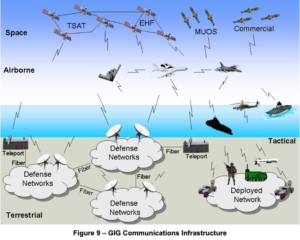
63. Bioterrorism: Another term for this system of gangstalking-electronic torture.
64. Bio-tracking: Is accomplished through brain signatures. (Dr. JG).
65. Body Area Network (BAN): A technology that allows communication between ultra-small and ultra low-power intelligent sensors/devices that are located on the body surface or implanted inside the body. Wearable/implantable nodes can also communicate to a controller device that is located in the vicinity of the body. SW says: “BAN: That’s you, your biofield, your body part… The Body Area Networks were load-balanced with Covid, the industrial-cyber-physical backbone. It’s over. You will be administered to by AI. They needed more throughput through their own upgraded bodies. Transhumanism. ”
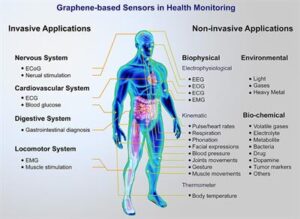
66. Brain components: According to a 2014 power point presentation by ex-CIA brain scientist, Dr. Robert Duncan, brain components that can be remotely manipulated electronically include neurons, axons, dendrites, organelles, synapses, synaptic connections, axon terminals, neural receptor sites, Myelin Sheath, glial cells, neural networks, resonance networks, neural transmitters, micro and macro circuits, DNA protein generation, neural inhibitors, EM resonance, passive ion channels, active ion pumps, and channel density.
67. Body Control Unit (BCU): SW: Your cell phone.
68. Body Sensor Network (BSN):
69. Body-to-Body Communication/Interface:
70. Botnet: Like a virus propagating in real time…. It’s an activated silicon programmable neuronal agent….. It’s like ebola for networks.
71. Brain-Colon-Brain Communication/Interface: SW: Brain-colon-brain connectivity/wireless communication equals neuron exchange. This connection needs to be secure for transfer of information by cyber security standards.
72. Brain-to-Brain (B2B) Interface: SW: This became commercially available in 2014. Web portals.
73. Brain-to-Computer (B2C) Communication/Interface: Term, Brain Computer Interface (BCI), was coined by Jacques J. Vidal, who laid out a comprehensive experimental research plan to interface the human brain with computers. BCI is used by DARPA and the DoD (military) as a bi-directional, offensive, biological-technological weapon of mass destruction to deliberately alter, impair, disrupt, and disorganize your cognitive, motor, or central nervous system and behavioral outcomes. This system can be used for torture, to shut someone down, or to guide people to do things and then erase their memory of those actions. Information feeds into a biometric BAE station dedicated server, i.e., computer operator. He/she (the sender) can alter targets’ brain signals and then return them via a wireless implanted device in target’s (victim’s/receiver’s) brain. (This process is referred to as EEG heterodyning). This system is training AI about what neurons affect what parts of the body. Facilitates brain encoding, with and without EEG overlay. (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
74. Brain Imaging Libraries (BIL): SW: Used to commit changes of CRISPR-CAS-9 to amino acids, amino chains, proteins, peptidesm etc.
75. C4ISR: Abbreviation for “Command, Control, Computers, Communication, Intelligence, Surveillance, Reconnaissance.” All branches of the military use this technology. Also, the name of military journal.
76. C5ISR:”Command, Control, Computers, Cyber, Communication, Intelligence, Surveillance, Reconnaissance:
77. Chakras: SW: your bloodstream, circulatory system, the points where veins and/or arteries converge.
78. Chemical, Biological, Radiological and Nuclear (CBRN) skiffs: SW: made of your DNA, they protect elite from a their own bioweapons for prima materia (4D skiffs).
79. Circadian Rhythms: Are 24-hour cycles that are part of the body’s internal clock, running in the background to carry out essential functions and processes. One of the most important and well-known circadian rhythms is the sleep-wake cycle.
80. CISCO backplane/control plane: SW: Google software control plane for the SMART cities and Agenda 2030 implementation to control all people through AI Precision Health Care. Includes Sirius Group, Orion Node Operator Group, Pleidian Group, Solar Winds, all of which are routing through the human body. This is a eugenics program. Sometimes mistakenly referred to as “astral plane.”
81. Cisco Software-Defined Wide Area Networks (Software Defined Networking):
82. Cooperative Electronic Support Measures Operations (CESMO):A system that feeds NCCT () with data gleened from conventional signals intelligence.
83. Covid Body Area Network (C-BAN or COV-BAN): SW: Covid’s Data Center, this is the larger “backbone” for this system of synthetic biology, anti-aging, life-extension, immortality research, regenerative medicine, biomedical engineering.
84. Covid-19 jab/injection/bio-weapon: Wireless sensor network comprised of self-assembling nano-tech and metamaterials, including graphene.
85. CRISPR-CAS-9: (CRISPR: Clustered Regularly Interspaced Short Palindromic Repeats) Can be used to make selective genetic changes to your DNA.
86. Closed Neuronal Loop:
87. (The) cloud: “The cloud” refers to servers that are accessed over the Internet, and the software and databases that run on those servers. Cloud servers are located in data centers all over the world. By using cloud computing, users and companies do not have to manage physical servers themselves or run software applications on their own machines. SW: Our bodies are “on the cloud” or “tethered to the cloud” since 2005.
88. Combinatorial Synthesis Libraries: SW: Hold our DNA.
89. Cognitive Body Area Network (CBAN): Used by Net-Centric and Cognitive Warfare Fighters to read your mind in real time.
90. Cognitive computing: refers to technology platforms, that, broadly speaking, are based on the scientific disciplines of artificial intelligence and signal processing. These platforms encompass machine learning, reasoning, natural language processing, speech recognition and vision, human-computer interaction. Characteristics: being connected to everything.
91. Cognitive Technology Threat Warning System (C2TWS): SW: (Came online in 2007): a brain-computer interface designed to analyze sensory data and alert foot-soldiers to any possible threats. Part of U.S. Department of Defense’s effort to produce an efficient and working Network-centric soldier.
92. Cognitive Warfare (CW): The “war against truth and thought.” The weaponization of anyone and everyone. This sixth warfare domain enlists each of the other domains; land, sea, air, space and cyberspace, to defeat enemies, including targeted individuals and targeted populations. Hence, CW is multi-domain warfare that utilize no-touch torture, “nonlethal weapons,” and electronic-information-netcentric neuro warfare, etc.
93. Combinatorial Synthesis: SW: holding your DNA still and making changes.
94. Combinatorial Synthesis Libraries:
95. Communications Intelligence (COMINT): Element of Electronic Warfare
96. Computer Network Attack:
97. Computer Network Defense:
98. Computer Networking Through the Human Body: (google search) About 720,000,000 results. The idea of networking computer networks and the human body is driving research in a number of areas. Recently, two teams of researchers shared their respective projects, which explore how biological cells might become networked and how electronics could become directly integrated with human tissue. Sept. 24, 2020
99. Computer Network Types by Scale: Include: Body Area Network, Personal Area Network, Local Area network, Campus Area network, Metropolitan Area Network, Radio Area network, Wide Area Network, and Ultra-Wide Band Area Network.
100. Connectivism: A learning theory for the digital age. Being connected to everything. The theory of connectivism imples that humans do not only learn from their own experiences but also based on the experiences of others
(Sabrina: i.e., by mob mentality, especially when it’s shoved into your head against your will with AI that’s going to be using Distributed modelling technology with high fidelity across a layered framework that some little agent can log in and out of for the topology of everything in my house and me! Remember I mentioned that in signals intelligence, we don’t hone you, we hone your environment(!!!!!). They created the software and the systems you are using today at the expense of my own spine. This is horrible.)
Thus, the knowledge base can be continually expanded. The theory emphasizes the importance of interaction between humans and computer systems in a city as the constant interaction between city and its citizens increases the common existing knowledge.
101. Core Enterprise Services: Per Department of Defense Global Information Grid Architectural Vision Vision for a Net-Centric, Service-Oriented DoD Enterprise (2007), set of capabilities to allow greater interoperability and information sharing across the Mission Area (Warfighter, Business, Defense Intelligence, and EIE) services.
102. Cortical Homunculus: Map of the brain produced by Wilder Penfield in the 1940s (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
103. Counterintelligence:
104. Countermeasures (for RF, radio frequency, DEW, neuroweapon attacks): SW: Manipulation of EM waves can Block, Shock, Shunt, and Shield, Block, Absorb, Enhance, Bend Waves. Metamaterials and meta-surfaces can steer, absorb, frequency filter, polarize, split, alter phase, custom EM/MAG field and outputs. Psimatics, the power of sound.
105. Counterpropaganda:
106. Covid mRNA “vaccine:” SW: Bio-nano machines. Includes graphene and other metamaterials that allow greater data throughput for this EM-computer control grid system. This provides a cyber-physical backbone for the Fourth Industrial Revolution. Graphene and other metamaterials facilitate fast Wireless Body Area Networks (WBAN) throughput and more data through the WBAN for the SMART cities. See: (ARRC) Seminar Series – Prof. Ian F. Akyildiz (DARPA) – “Covid mRNA Vaccines Are Nothing More Than Bio-Nano Machines” – Graphene-based Plasmonic Nano-Antenna for Terahertz Band Communication in Nanonetworks
107. CoV-BAN: SW: What is that? That’s you looking in my veins and arteries without my permission of whether or not I’m diseased enough for electronic submission. And somebody, young or old, is sitting at a data base somewhere real happy to punch them numbers in. They have weapons that none of them even understand in your blood and tissue. I’m done with the Covid table-topped larp session of controlling humans on a button press with United States Air Force sim technology.
108. CubeSats: Nanosatellites, CubeSats are built to standard dimensions (Units or “U”) of 10 cm x 10 cm x 10 cm. They can be 1U, 2U, 3U, or 6U in size, and typically weigh less than 1.33 kg (3 lbs) per U. NASA’s CubeSats are deployed from a Poly-Picosatellite Orbital Deployer, or P-POD. They locate targets via position, navigation, timing of nano-satellite, nano-avionics.
109. Cyber Kill Chain:
110. Cyber-physical backbone: SW: Has been up and running since 2017. Materials and metamaterials in Covid jab (including biosensors) were rolled out because they needed more throughput for this electronic warfare system.
111. Cyberphysical Systems (CPS): SW: The “backbone of the Fourth Industrial Revolution”
112. Cybersecurity and Infrastructure Security Agency (CISA): A component of the US Department of Homeland Security (DHS) responsible for cybersecurity and infrastructure protection across all levels of government, coordinating cybersecurity programs.
113. Cybersecurity for new digital ID: SW: Includes low power 2.4 THz because we are using nanotechnologies and THz technologies. Metamaterials and AI are involved. Following DDOD 3000.09, with an autonomous military, it uses very old the Wireless Body Area Network (WBAN) technology. It is
114. CYBORG (Cybernetic Organism): SW: Everyone is now a cyborg; with soft robotics deployed with biosensors in us that are DNA- analyte derivatives made out of our tissue. They communicate with satellites our position, navigation, and timing, NTS-3 accessible (no GPS needed) inside of our bodies. Our bodies are the network and the node. Our bodies are propagating the signal, with no implants or towers required. Human + Hybrid (graphene, reneas, SOC).
115. Cymatics: SW: The power of sound at the nano-scale. The study of sound and vibration made visible typically on the surface of a plate, diaphram or membrane.
116. Cytokine storm: SW: A physiological reaction in humans and other animals in which the innate immune system causes an uncontrolled and excessive release of pro-inflammatory signaling molecules called cytokines. This is also caused by sensor hunters biohacking the human biofield for a bioelectromagnetic algorhithm.
117. DARPA: Defense Advanced Research Projects Agency
118. (Obama’s) Death Panel Data Bases instituted in 2008: SW: These select for: “too old, unvaxed, undeliverable, “unveiled” (know too much), or those to be infected with candida mushroom fungus include those who are too fat, eating fast food, weak veins, low bone density.
119. Defense Enterprise Computing Centers: DISA’s (see next entry) regional computing centers.
120. Defense Information Systems Agency (DISA): A US Department of Defense combat support agency composed of military, federal civilians, and contractors.
121: Defense Intelligence Information Enterprise (DI2E): a cross-domain service, according to US Air Force, that provides services for net-centric missions. DI2E is a computer framework for sharing data between defense and intelligence agencies and their international allies. It is responsible for the collection, analysis, validation, and dissemination of threat data and information for all facets of military operations and acquisitions. At the heart of the DI2E is the DGCS Integration Backbone (DIB), a set of data fusion services that provide a mechanism for DoD and Intelligence community search, discover, and retrieve its DGCS content. DI2E has subsumed DGCS.
122. Department of Defense Directive (DODD) 3000.09: SW: (2012 for implementation in 2017): States that the goal of autonomous systems (i.e., lethal autonomous weapons systems) is to avoid negative outcomes (specifically, unintended engagement or loss of control of drones)
123. Department of Defense Unmanned Systems Integrated Road Map (FY 2013-2038):
124. DNA Encoded Solid-Phase Synthesis (DESPS):
125. Digital ID (“Digi ID”): SW: In place in 2009
126: Digital Twin (DT): An evolving digital profile of the historical and current behavior of a physical object/process (person) that helps optimize business performance. The digital twin is based on massive, cumulative, real-time, real-world data measurements across an array of dimensions. DT is a replica of you which is online and is built from the data extracted from you. It is run through algorithms and is used against you through the form of manipulation of what is shown to you on your own personal devices, because we all have our own personal algorithms. It’s you but it can be an alter-ego of you and it can manipulate you by the visuals they show you.
127. Digital Twin architecture: SW: There is a digital copy of each of us in “the cloud” aka US military’s Sentient World Simulation.
128. Digital Twin Computing Initiative (DTC): “Nippon Digital Telegraph and Telephone Corporation (NTT) proposed this initiative: a platform to combine high precision digital information reflecting the real world to synthesize different virtual worlds, generate novel services, and bring about the society of the future.” (Tokyo Business Wire, 2019). The DTC initiative will be achieved on an innovative network and information processing platform having ultra-large capacity, ultra-low-latency, and ultra-low-power features on NTT’s Innovative Optical and Wireless Network (IOWN).
129. Dirtbox (DRT box): A cell site simulator, a phone device mimicking a cell phone tower, that creates a signal strong enough to cause nearby dormant mobile phones to switch to it. Mounted on aircraft, it is used by the United States Marshals Service to locate and collect information from cell phones believed to be connected with criminal activity. SW: Used by Sheriff’s and police to hunt DNA in targeted individuals’ biosensors.
130. Defense Information System Network (DISN): The Defense Information System Network has been the United States Department of Defense’s enterprise telecommunications network for providing data, video, and voice services for 40 years.
131: Distributed Common Ground System (DCGS):The US military stores ISR (Intelligence, Surveillance, Reconnaissance) data (imagery intelligence) on the DCGS when planning operations and forming target tracks and fixes. It gives them a common view of the battlefield and everything on it, common ground. Common ground means the same surveillance from platforms such as drones, the same human intelligence, the same geo-location coordinates, from target tracks, the same signals reading from CESMO, the same aerial photography and satellite images. (See:
“Drone kill communications net illustrated” by Mark Ballard, 2014 in ComputerWeekly.com).
132. DNA: SW: Propagates the signal of your human biofield, your body is the node and the network on the system.
133. DNA Sequence Matching:
134. DNA steganography: hiding undetectable secret messages within the single nucleotide polymorphisms of a genome (your DNA) and detecting mutation-induced errors… The classical DNA steganography method hides DNA with a “secret message” in a mount of junk DNA, and the message can be extracted by polymerase chain reaction (PCR) using specific primers (key), followed by DNA sequencing and sequence decoding.
135. DNA Encoded Solid-Phase Synthesis (DESPS):
136. Drone Kill Communications Net:
137. Dynamic Channel Allocation Thermal Channel Routing:
138. Dynamic Spectrum Modulation Allocation/Communication:
Electrochemistry:
139. Energy Harvesting Through The Body: SW: You will power your coffee pot according to Pentagon Directive 3000.09.
140. Engineered Biological Entities (EBE): Sabrina Wallace: We make EBEs. We torture people into submission and we create hybrids.
141. EEG (Electroencephalograph/Electroenchephalogram): Electroencephalography is a method to record an electrogram of the spontaneous electrical activity of the brain. The biosignals detected by EEG have been shown to represent the postsynaptic potentials of pyramidal neurons in the neocortex and allocortex. Hans Berger recorded the first human EEG in 1924. (from: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
142. EEG – Brain Connectome: Brain connectivity, Human connectome, Concurrent EEG-fMRI, ICA INTRODUCTION The advances in neuroimaging in the last decades have brought new important insights on brain functioning by using both electroencephalography (EEG) data and functional magnetic resonance imaging (fMRI) data extracted from human brain.
143. EEG Cloning: A specific case of EEG heterodyning and is the term used when there is 100% control over victim/target, now transformed into a human robot, or bio-robot. EEG cloning requires a live person-to-person interface (i.e., brain-to-brain or BBI/B2B interface). This is why TIs (targeted individuals) say sometimes it is a real person and other times it is repetitive AI programs (influencing/controlling them).
144. EEG Headset:
145. EEG Heterodyning: According to a 2014 presentation by ex-CIA brain scientist, Dr. Robert Duncan: 1) EEG (Electro Encephalographic) Heterodyning is the mixing of brain signals of a ¨target¨ by a group of handlers or AI. 2) The brain is the ¨hardware¨ and the mind is the ¨software.¨ 3) This ¨technology¨/program is used for remote creation and manipulation of ¨Manchurian candidates, remote-controlled soldiers, ¨interrogation targets¨, politicians, and others. 4) The purpose of the ¨program¨ is to Interrogate (i.e., torture), spy, kill, disable the target, practice, collect efficacy data, and incorporate cognitive models of language.
146. EEG overlay: SW: Used to over-write your brain tissue, i.e., re-write of your brain tissue from the inside out. Cost: $45,000.
147. Electroceuticals: Broadly defined as medical devices that provide neurostimulation for therapy, but it is often used as a term to reference ultra-miniature and injectable implants. Devices that treat ailments with electrical impulses include pacemakers for the heart, cochlear implants for the ears and deep-brain stimulation; wireless drugging.
148. Electromagnetic Speech Transfer: A communication technology which allows delivering through the wall and from a large distance audible speech to a specific individual by the mean of electromagnetic waves.
149. Electromagnetic Speech Transfer Technologies include:
a) Microwave Auditory Effect
(https://en.wikipedia.org/wiki/Microwave_auditory_effect,
https://ieeexplore.ieee.org/document/9366412,
https://www.sbir.gov/sbirsearch/detail/298760)
b) Photoacoustic Effect :
(https://www.optica.org/en-us/about/newsroom/news_releases,/2019/new_technology_uses_lasers_to_transmit_audible_mes/,
https://www.ll.mit.edu/news/laser-can-deliver-messages-directly-your-ear-across-room)
c) Invasive neurotechnology devices
(From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
150. Electronic Integrated Disease Surveillance System (EIDSS): SW: CDC uses this; They have an app on their phone for that… for bioconductors. aka Electronic Integrated Disease Data Base. Bioconductor software with bio on your C-BAN- (covid body area network- COV-BAN). Military, police, Sheriff, Lawfare and ISR (Intelligence, Surveillance, Reconnaissance) use Stingray and DRTBox to support this surveillance system with the CDC. This is cognitive technology tech warfare (CT2WS) system that uses EEG to look through your veins and arteries (since 2007).
151. Electro-optics/Infra Red (EOIR): Uses visible, IR (infra-red) and UV (ultra-violet) portion of electromagnetic spectrum. The market includes air, land, sea, and space vehicles searching, tracking, targeting, warning, and surveillance systems.
152. Electronic Opto-Array: SW: Allows people to look at DNA inside the body and change the DNA without having to be near the target.
153. Electro-quasistatic human body communication: The method of sending signals directly through the body. a body channel that uses human body as the communication medium for the devices (webmaster: including biosensors) in the body. It exploits the conductive properties of the body and combines attributes of both wireless and wired signals.
154. Electronic Counter Countermeasures (ECCM): (Element of Electronic Warfare)
155. Electronic Counter Measures (ECM): (Element of Electronic Warfare)
156. Electronic Support Measures (ESM): (Element of Electronic Warfare)
157. Electronic Intelligence (ELINT): (Element of Electronic Warfare)
158. Electronic Protection (EP): (Element of Electronic Warfare) Countermeasures
159. Electronic Warfare (EW) aka Electromagnetic Warfare: Electronic Warfare (EW) is the use of electromagnetic or directed energy and integrated cyber capabilities to carry out military and intelligence missions. For 60 years, Raytheon, Lockheed, RAND, BAE Systems have been developing this type of warfare. EW is the total dominance of the electromagnetic spectrum. All objects, including human bodies, emit electromagnetic information. We now use galvanic coupling through human body communications. EW is an industry, “sensors to shooters: using data to make decisions on a connected battlefield.” (from Defense News and C4ISR.net)
160. Energy Harvesting: SW: In 2014, the FCC (Federal Communications Commission) mandated that WBAN can be used for energy harvesting radio frequency out of your body.
161. Energy Harvesting-Based Wireless Body Area Network (WBAN):
162. Exponential (emerging/game-changer) technologies: Dr. JG: We are living in a time of the proliferation of 30 different accelerated exponential technologies. Manipulation of atoms and neurons will shape future decades and centuries of our civilization. NSF has been researching 5 key technologies; manipulation of genes, atoms, bits, qubits, neuro, and information. To look at all these together, we must change the way we look at science. Nano, bio, IT, quantum, and neurotechnologies are game changer technologies for our civilization that affect everything from health care to defense (enhancing soldiers, for instance) to manufacturing. Each creates massive opportunities and has “dual use” (have “light” and “dark” sides to help and to harm) capabilities.
163. fMRI (Functional Magnetic Resonance Imaging): A type of noninvasive brain imaging technology that detects brain activity by measuring changes in blood flow. A standard MRI scan uses an extremely powerful magnet, radio waves and computer processing. It can reveal what part of the brain is active during specific functions, such as lifting your arm or thinking of the word \”summer\”.
164. fNIRS (Functional Near Infra-red Spectroscopy): Used as biosensors for brain-to-computer interface with optical windows and nano-meters.
165. Fabric-based computing: different kind of computer network created by biosensors. Fabric-based computing is a modular type of computing where a system assembles from different building-block modules through a fabric or switched backplane. The fabric consists of nodes and links. SW: So we needed more bodies that were talking to each other faster. For that, we need metamaterials. FBC is a mesh network using the Global Information Grid (GIG) with you (as a noded on the network).
166. Feeder grids:
167. Free-space optical communications: According to 2007 IEEE Avionics, Fiber-Optics and Photonics (AVFOP) conference, “now common for point-to-point communications, including nano-peer-to-peer, neuron-to-neuron, brain-to-brain, multi-brain to single brain for point-to-point and peer-to-peer, NAPSTER, between fixed and moving platforms on land, sea (submarines), air, and space. Virtual light communications, includes 5G, OSIRIS, nano-slaughter bots, lethal autonomous weapons systems. Free-space optics.
168. Free-space Optics with Machine Learning approach to Array-Based Free-Space Optical Communications Using Mobile Devices: SW: Cell phones use BAD BAN so phones can send and receive opto-genetics back and forth using your biosensors, products to control your biofield.
169. Frequency modulation on separate channels: Multiplexing math of air molecultes. Netcentric warfare, ubiquitous computers, Committed by Bluetooth low power energy Lora.
170. Front-hall and back-hall of 5G and 6G: SW: Used to trade cells out of your body digitally (by converting THz to GHz and GHz to THz; i.e., converting digital to biological and biological to digital).
171. Galvanic Intrabody Coupling: A method for injecting an electrical communication signal into the body. The body acts as the communication channel and the injected signal is transmitted primarily through the skin. Normally, devices on the body communicate wirelessly through radio frequency (RF) technology.
172. Gangstalkers/Perps/Goons on the Ground: “Civilian cult of sleeper cells that they radicalize into violent extremism.”
173. Gateway Experience/Process/Project (Hemisync) (CIA): uses of the Hemi-Sync technique. “Hemi-Sync is a state of consciousness that can be seen on EEG scans, the two hemispheres of the brain (right and left) are simultaneously equal in amplitude and frequency.”
174. Generative Adversarial Networks (GANs): Machine learning; algorithmic architectures that use two neural networks, pitting one against the other (thus the “adversarial”) in order to generate new, synthetic instances of data that can pass for real data.
175. Genome: The content of genes in a cell.
176. Genomics: Genomics is an interdisciplinary field of biology focusing on the structure, function, evolution, mapping, and editing of genomes. A genome is an organism’s complete set of DNA, including all of its genes as well as its hierarchical, three-dimensional structural configuration.
177. GEOMANCER and Geospatial Data Base Open-Source on the GITHUB: SW: Provides Framework Connected Databases to locate anyone, any time, anywhere. Spells are the collection of Python code on Geomancer. Geomancer is how we find you so that we can execute whatever electrical code we are designed to on your body part (biofield). We use Geomancer to hunt you down by your body part digitally and log in.
178. Geophysics:
179. Global Information Grid (GIG): The Global Information Grid is a network of information transmission and processing maintained by the United States Department of Defense. More descriptively, it is a worldwide network of information transmission, of associated processes, and of personnel serving to collect, process, safeguard, transmit, and manage this information. SW: Satellite connectivity to everybody. Formerly World Sentient Simulation, now it is the Global Information Grid of Sensors using Biosensors securely. GIG mandates full dominance of the electromagnetic spectrum and is a set of directives for netcentric warfare coming from DOD Chief Information Officer in 2007. GIG is a grid of sensors for your drone operators for your Simulated World Simulation NASA documentation for full domination of the electromagnetic spectrum for electronic warfare. And everybody’s biosensors are talking back and forth inside of your wireless body area network, your wireless personal area network, on the same network as your phone. Bluetooth BLE, Zigbee and millimeter wave are all accessible to 6G loPan, terrahertz to gigahertz and gigahertz to terrahertz. Biosensors are what compose the Global Information Grid. GIG is also you digital twin. See: Department of Defense Global Information Grid Architectural Vision Vision for a Net-Centric, Service-Oriented DoD Enterprise (2007) Driven by the DoD Enterprise model. Refers to Joint Mission Capability Focus (2003).
Cyber-physical systems are inside the biosignals technology that we’re looking at with the GIG.

180. GIG Communication Infrastructure:
181. Global Dark Networks: Dr. JC: Self-Organizing Systems, including: Terrorists, Criminals, Predictive, Mobile, Human Trafficking, Cyber Crime, Arms, MNCs, Money Laundering, Distributive, Rogue States, Radicals, Drugs, Fraud…
182. Golden ratio: SW: This can be used to decouple (uncouple) the cellular state.
183. Graphene: SW: A metamaterial used in Covid jab to excite neuromodulation, neurostimulation, and radio modulation as well as increase “throughput” (communication capacity) of EM frequencies through the system.
184. HADES (High Accuracy Detection Exploitation System): SW: The first program coming out of the US Army’s MDSS (Multi-Domain Sensing System) family of systems is the High Accuracy Detection and Exploitation System (HADES) program.
185. Havana Syndrome: A cluster of idiopathic symptoms experienced mostly abroad by U.S. government officials and military personnel. The symptoms range in severity from pain and ringing in the ears to cognitive dysfunction and were first reported in 2016 by U.S. and Canadian embassy staff in Havana, Cuba. Thought to be caused by DEW (directed energy weapons) on RF Industrial, Medical, Scientific Band 2.4 THz, WBAN 802.15.4 and 802.15.5 since 1995.
Dr. J.C.: “The American officials attacked in the embassies in Cuba and China were attacked to demonstrate a proof of concept, that is, to demonstrate an operational, deployed capability of soft, non-lethal neuroweapons that could and did “take them out of the game.”
SW: “March 20, 2023: the ODNI: “There’s no explanation for Havana Syndrome.” That means that there’s no such thing as SynChron, SynBio (these are companies) or synthetic biology as a science, and synthetic telepathy in Elsevier journals- and there are. So the ODNI (Office of the Director of National Intelligence) gets to lie and these people get to die, while these people go to work.”
186. Hemi-sync: Part of CIA’s Gateway Process. SW: EEG and brain connectome testing for DNA sequencing.
187. High Altitude Electromagnetic Pulse (HEMP): DoD Interface Standard. Protection for ground-based C4 facilities.
188. Hive Query Language (HiveQL):A query language for Hive to analyze and process structured data in a meta-data, Meta-store. SW: Meta-store, meta-genomics; big, big optic data bases running across the entire country, using your body, watching you through your own red blood cells and tissue. Your bio-sensors, biophysics, optogenetics… So that we have the grid, the Global Information Grid (which used to be called Sentient World Simulation).
189. Holographic communications:
190: The Homeland Defense & Security Information Analysis Center (HDIAC): is a component of the U.S. Department of Defense’s Information Analysis Center (IAC) enterprise.
191. Human augmentation: SW: Includes hybridization, transhumanism, hypergraph transfer with the N-Sphere math. Those who have taken the jab have been augmented with nano.
192. Human Biofield: ” “A field of energy and information, both putative and subtle, that regulates the homeodynamic function of living organisms and may play a substantial role in understanding and guiding health process…” SW: aura, chakras, the ions and electrons you exchange with your environment.
193. Human Body/Bonding Communication (HBC) Protocols: Human body communication (HBC) uses the human body to transmit power and data, much like the internet. Incorporates all five sensory information from sensing to digitization to transmission and replication at the receiver to allow more expressive, engaging, realistic and holistic information between humans, and in some cases between humans and machines (M2H) or IoTs. On RF spectrum since 1995, encrypted, for computer routing to digital twins. HBC requires tiny amounts of electrical signals to be sent through the body. (SW: I.e., electrocuting you from the inside out.) In the new 6G, this is called Human Bonding Communication.
194: Human Computer Interaction (HCI):
195: Human Connectome Project: MEG (magnetoencephalography) and EEG (electroencephalography) are non-invasive electrophysiological techniques for recording brain activity. EEG is based on measuring voltage sensed by an array of electrodes placed on the scalp.
196. Human husbandry: SW: Elite have practiced this for millennia.
197. Human Teleportation: SW: Accomplished with microsoft in 2016 via software-defined networking.
198. Humans as Sensor: This system.
199. Hybrid Warfare:
Definition 1: Includes use of regular military forces, Special Forces, Irregular Forces (i.e., civilians), Information warfare and propaganda, diplomacy, cyber attacks, economic warfare, and neurowarfare.
Definition 2: includes Fourth Generation Warfare, unconventional warfare, asymmetrical warfare, net-centric warfare, information warfare, military-operations other than war, low-intensity conflict, peace operations, psychological warfare, irregular warfare, the war on terrorism, weather warfare, environmental warfare, civil-military operations, multi-domain warfare, cognitive warfare (6th domain of warfare).
200. Hydrogel bioelectronics:
201. Hypergraph Transfer Protocol:
202. IEEE (Institute of Electrical and Electronics Engineers): IEEE is a 501 (c) (3) professional association for electronics engineering, electrical engineering, and other related disciplines with its corporate office in New York City [4] and its operations center in Piscataway, New Jersey.
203. IEEE Working Group for 802.15: 802.15 is your Wireless Personal Area Network (WPAN).
204. I.P. address: Internet Protocol address is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification, and location addressing.
205. Industrial Internet of Things:
206. Industrial Cyber-physical Systems: SW: Backbone of the Fourth Industrial Revolution
207. Industrial Internet of Things (IIoT):
208. Industrial, Scientific and Medical (ISM): and UWB (Ultra-Wide Bands) are able to support high data rate applications and are available worldwide.
209. Information Operations (IO) (Classified) at Naval Post-Graduate School in Monterey, CA: SW: Control the electromagnetic environment surrounding targets and targeting operations.
210: Information War (IW): Includes military/intelligence/National Security Forces deploying “Neuro-Ops”, or altered reality tactics. Transcranial mechanisms are used to disrupt people’s sense of time and place. Cortically-coupled neural temporal function alteration is accomplished by “time warpers”, another form of IW.
-Pharmacologic neurostimulation is used to induce cognitive-emotional disruption, another form of “Information Warfare.”
– Cyborgs are used in mixed Intell-Combat Ops/Information Warfare. Neuro-modified “cyborg” systems include the DARPA “Beetle” and the Dragon flEYE. (Dr. J.G.)
211. Intelligence operators (video game players): are harnessed to brain-machine (B2C) interfacing systems so as to allow an increased capability through reciprocal dynamic robotics such that they can learn from each other and thereby improve performance. (Dr. JG).
212. Infantry Brigade Combat Team (IBCT):
213. Integrated Device In Vivo: Biosensors inside of people
214. Intermittent Link State Routing: SW: Using 802.15.5 your mesh relays around the body.
215. Internet of Behaviors (IoB): SW: Watches the cells inside you with NTS-3. Monitors position, navigation, and timing of biosensors for the Global Information Grid (GIG) per DOD Directive 3000.09.
216. Internet of Bio-Nano Things:
217. Internet of Bodies (IoB): The Internet of bodies is a network of wearable, ingestible, injectable, and implantable smart objects located in, on, and around the body. Although radio frequency (RF) systems are considered the default choice for implementing on-body communications, which need to be localized in the vicinity of the human body (typically less than 5 cm), highly radiative RF propagations unnecessarily extend several meters beyond the human body. This intuitively degrades energy efficiency, leads to interference and coexistence issues, and exposes sensitive personal data to security threats. As an alternative, the capacitive body channel communication (BCC) couples the signal (between 10 kHz-100 MHZ) to the human body, which is more conductive than air. Hence, BCC provides a lower propagation loss, better physical layer security, and nJ per bit to pJ per bit energy efficiency.
218. Internet of Military Things: A class of Internet of things for combat operations and warfare. It is a complex network of interconnected entities, or “things”, in the military domain that continually communicates with each other to coordinate, learn, and interact with the physical environment to accomplish a broad range of activities in a more efficient and informed manner. SW: Used in conjunction with Project Maven.
219. Internet of Space Things:
220. Internet of Things (IoT):
221. Intrabody Nano-Network: La Quinta Columna has shared a summary of the intra-body nano-network that forms after each inoculation the population receives. The author of this summary is Mik Andersen, owner of the research blog Corona2Inspect, who’s a renowned scientist who has chosen to collaborate with La Quinta Columna and Dr. Pablo Campra’s research under a pseudonym. This nano-network described by Andersen is the one that would allow the neurostimulation of the population through a network designed for this purpose.
Many indications confirm that neuromodulation is the real purpose of the operation behind the global inoculation, ranging from the enactment of neuro-rights laws in some countries to the structuring of the same nano-network that is being deciphered, which would be a very advanced military technology.Intra-body Nano-network
222. IRS data bases: SW: People to get rid of include political opposition, people we don’t like-type groups of people
223. ISR (Intelligence, Surveillance, Reconnaissance): Military
224. Joint All-Domain Command and Control Specifications for Netcentric and Mosaic Warfare:
225. Joint Tactical Radio System (JTRS): Software programmable radios (handheld, vehicle mounted, airborne, sea-based, fixed locations) as part of tactical (warfare) environment.
226: KH-11 KENNEN reconnaissance satellites: were launched in 1976. Manufactured by Lockheed Martin, the KH-11 was the first spy satellite to use electro-optical digital imaging. (from: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
227. K-Hop Nearest Neighbor Routing: This system has been in use to route RF from body to body since 2007.
228. Kill Box: SW: Your house
229. Kill Chain:
230. La Quinta Columna: SW: Website/scientific research group in Spain (Ricardo Delgado, Dr. Pablo Campra, and others) that first recorded and reported on self-assembling bio-circuitry appearing in Pfizer injection and in blood samples of “the vaccinated.” Reported that with neuromodulation and radiomodulation these nano-materials, including graphene, are excited by light. Graphene installed in COVID jabs forms self-assembling electrical circuits in the body and blood. Website also records neuro-stimulation, neuro-modulation, and neuro-monitoring in brain connectomes, transcriptomes and that brain-imaging libraries accessible to just about anyone doing this research use CRISPR-CAS-9, methylate your DNA, or wrap it in proteins with proteonomics.
231. Langland’s Equation (1960s): SW: “The Rosetta Stone of mathematics;” new type quantum encription to break all the bit series old encriptions with the L function and the meromorphic function changing out the politons and poles, on the complex plane of any torial field that we want with the quantum field and the quantum space and quantum underground space. Enormous scope + vague details = security
232. Lethal Autonomous Weapons Systems: SW: Named in DDoD 3000.09, these may be unmanned and include soldier-precision-targeting devices.
233. LIDAR: Lidar is a method for determining ranges (distances) by targeting an object or a surface with a laser and measuring the time for the reflected light to return to the receiver. LIDAR may operate in a fixed direction or it may scan multiple directions, in which case it is known as LIDAR scanning or 3D-laser scanning, a special combination of 3-D scanning and laser scanning.
234. Life Extension/Immortality research/regenerative medicine:
235. Li-Fi (Light-Fidelity) Technology: Invented by German physicist, Harald Hass, Li-Fi is a wireless technology that makes use of visible light in place of radio waves to transmit data at terabits per seconds speed- more than 100 times the speed of Wi-Fi. Discovered in the last decade, proofs of concept to test commercial utilization started emerging only in 2015.,
236. Liminal space: Liminal spaces are transitional or transformative spaces. Such places are often associated with a forlorn atmosphere, a disconnection from the concept of reality, and a fluid or sometimes neglected aesthetic. They are the waiting areas between one point in time and space and the next. (SW: Example: The Rydberg-atom toroidal field. Webmaster example: Operation Crestone/Baca mind control experiment.)
237: Liquid neural networks: Liquid neural networks are a new kind of machine-learning system that learn on the job and adapt to new environments, even in complex and noisy scenarios. MIT researchers showed that drones with liquid neural networks outperformed other AI systems in navigating unknown forests and cities, and could be used for various applications such as robotics, video and language processing.
238. Liquid neurons: In January 2021, MIT researchers built ‘liquid’ neural neurons, which were inspired by the brain of small species. It is considered ‘liquid’ because the algorithm can adjust to changes experienced by real-world systems, by changing the equations as they receive new data. In other words, the algorithms can become fluid like water, and adjust to change as liquid adjusts itself to the object it’s in.
239. Liquid neuromorphic network translation: SW: In software defined networking, they can strip neurons and place them elsewhere.
240. Local Logistics: SW: Experimenting with N2 and N3 for B2B Interface and neuro-colon-neuron with cyber security.
241. LoRaWAN (The LoRa): a Low Power, Wide Area (LPWA) networking protocol designed to wirelessly connect battery operated ‘things’ to the internet in regional, national or global networks, and targets key Internet of Things (IoT) requirements such as bi-directional communication, end-to-end security, mobility and localization services. SW: US started chipping people with RFID in the 1960s using this system.
242. Luciferious-Dragonfly Google Program: SW: Built by Eric Schmidt and Apple in China in the 1990s after Pres. Clinton granted them all data and software.
243. mRNA in Covid jab: Human genetic augmentation, mRNA are small scale, programmable nano machines
244. MAC (Medium Access Control) IDs: SW: MACs were being put and used in humans by 1977-79 and are still in widespread use today for this system. MAC addresses are mandated for the Medical Body Area Network (MBAN) by the FCC.
245. Machine Learning:
246. Machine-to-machine:
247. Magnetic Resonance Imaging (MRI): SW: The MRI has left the hospital. We use the MRI to watch your brain in real time on cognitive radio networks.
248. fmi/MEG (Magnetoencephalography): Used for brain recording applications (Dr. JG).
249. Magnetic Resonance Imaging (MRI) scanners: Raymond Damadian and his team built the first full-body Magnetic Resonance Imaging scanner and performed the first human scan in 1977. (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
250. MANET Radio. A wireless ad hoc network[1] (WANET) or mobile ad hoc network (MANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre-existing infrastructure, such as routers or wireless access points. Instead, each node participates in routing by forwarding data for other nodes. The determination of which nodes forward data is made dynamically on the basis of network connectivity and the routing algorithm in use.
Such wireless networks lack the complexities of infrastructure setup and administration, enabling devices to create and join networks “on the fly”.[3]
Each device in a MANET is free to move independently in any direction, and will therefore change its links to other devices frequently. Each must forward traffic unrelated to its own use, and therefore be a router.From small teams to large and complex networks, the TrellisWare next generation MANET radios with TSM and TSM-X waveforms feature unparalleled performance for robust voice and data communication in harsh RF environments.
251. Measurement and Signature Intelligence (MASINT): (Wikipedia): Measurement and signature intelligence is a technical branch of intelligence gathering, which serves to detect, track, identify or describe the distinctive characteristics of fixed or dynamic target sources. This often includes radar intelligence, acoustic intelligence, nuclear intelligence, and chemical and biological intelligence. MASINT is about Remote Sensing. Passive remote sensing is like astronomy but looking toward the earth while active remote sensing is making use of Radars and Lidars.
252. Medical biometrics: The field of automated medical diagnosis of the human organism based on personal features to gauge human health and address any health issues.
253. Medical Body Area Network (MBAN): SW: Mandated by FCC in 2014. Allows remote (wireless electronic) health monitoring of a patient over periods of time without any restriction to his activities. Vital information of a patient is collected and continually forwarded to a remote monitoring station for further analysis. An emerging field for health diagnosis based upon inputs received from sensors and devices installed inside, on, or around the human body. Also: a network of sensors/actuators worn on the human body that communicate with a controlling device via a wireless link. The MBAN is a subset of of the more general trend of wireless body area networks (WBAN) or body sensor networks (BSN) that includes non-medical applications such as human-computer interfaces (e.g., neural interface, virtual reality), location tracking, and personal fitness tracking. SW: Those Body Sensor Networks stick to you on the body like the smart dust.
254. Medical Implant Communications Service/System: Liscenced band used for implant communications and has the same frequency ranges of 402 MHz to 405 MHz in most countries. Low power 2.4 MHz (LoRaWAN (The LoRa). Uses 802.15.4 biosensors and 802.15.5 BLE (Bluetooth Low Energy (or power) and routes low power radio frequencies through your skin. These operate on radio frequency bands. SW: This is happening since the 1960s. Keys to this are held by the (Jewish) “neoconservatives” that run America.
255. MEDUSA: A novel general-purpose (software) platform for modern non-invasive Brain−Computer Interfaces (BCIs). MEDUSA is a novel open-source, Python-based software ecosystem to accelerate BCI and cognitive neuroscience research. Compatibility with any signal acquisition system through the lab-streaming layer (LSL) protocol, including the possibility of recording multiple signals at the same time. Deploys a scalable MR (magnetic resonance imaging; MRI) console using USB (Universal Serial Bus). SW: Medusa is from the 1940s but she’s upgraded.
256. Metamaterials: SW: A material not found in nature, includes graphene, and metals in the air around you. Their precise shape, geometry, size, arrangement, orientation give them their S.M.A.R.T. properties. They help form transhumans, and facilitate intelligent communication for wireless health care. Programmable materials such as graphene are used for soft-ware defined electromagnetic control and form circuits, systems, and architecture. Metamaterials are made for the biological-digital convergence, taking your cell structure and electrically changing it by hacking the bioelectric code of your biofield. They are using the Bluetooth mesh networks to route all around you and to change your cell state to watch what you are doing way more than the localized medical body area network.
257. Metaverses: Metaverses are digital worlds populated by Digital Avatars. Digital Avatars can be piloted by human brains undergoing neuromonitoring and neurostimulation or by artificial intelligences based on human minds. Each AI based on a human mind is running a full emulation of a human brain leveraging all the functional brain imaging data collected by Remote Neural Monitoring to create the Digital Clone of an individual.
The metaverses are powered by a 3D Game Engine similar to Unreal Engine that is being streamed directly to the visual cortex through neurostimulation. The metaverses are being accessed through full immersive virtual reality engaging all 5 senses and they cannot be distinguished from reality.
There are at lest 3 metaverses: The most wonderful metaverse, The intermediate metaverse, The rotten metaverse
Every user has multiple lives each unfolding in a different metaverse. Users minds can be projected in their digital avatar in one of the 3 metaverses. Each metaverse has different rules and parameters. The digital avatar status and parameters can be different in each metaverse.
The “alternative” (fake reality) world of computers. In “Metaverse: All-Out War for your Consciousness,” metaverse is defined as a “fake utopia created by AI and computer algorithms… With 6G and beyond, you will not be able to distinguish reality from fiction in the digital world of the metaverse.”
258. Micromachines: Programmable electrofluidics for ionic liquid-based neuromorphic platforms (i.e., self-assembling nanotech in Pfizer injections as per studies by La Quinta Columna). (See 24:21 in above Sabrina Wallace video for diagram). (This is brain-machine or body-machine interface.)
259. MICS (Medical Implant Communications System): SW: Came online from 1955 to 1965 when they began chipping humans like dogs with RFID (Radio Frequency Identification).
260. Microelectrode arrays (MEAs): The workhorse technology in neuroscience, MEAs offer multiplexed electrophysiological recordings with high temporal resolution,
261. Microsoft’s Open AI Azure Raneous Chip Sets:
262. Microwave Auditory Effect: In 1962, Allan H. Frey published on this technique that allows direct communication to the brain through pulsed Microwave radiation (from: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com)).
263. Military Deception (MILDEC):
264. Minutely Invasive Neural Interfaces:
265. Modified Open System Approach (MOSA): Modular Open Systems Approach (MOSA) is an acquisition and design strategy consisting of a technical architecture that uses system interfaces compliant with widely supported and consensus-based standards (if available and suitable) and supports a modular, loosely coupled and highly… Hardware used on drones to carry out this weapons system.
266: “Moore’s Law:” Moore’s hypothesis is that computer technology doubles in power every 18 months. The cost of that power is also being halved in that amount of time.
267. Morgellons Disease: SW: These filaments are controllable. That’s wireless tissue engineering aka tissue scaffolding.
268. Mosaic Warfare:
269. Multidisciplinary Digital Publishing Institute (MDPI): is a publisher of open access scientific journals. MDPI is a member of the United Nations Global Compact to support corporate sustainability and is committed to the ten principles associated with the Compact. Sustainability (webmaster: i.e., genocide) has always been at the core of MDPI’s values.
270. Multi-Sensor Aerospace-Ground Joint ISR Interoperability Coalition (MAJIIC): NATO’s MAJIIC aimed to make innumerable surveillance platforms compatable: electro-optical (EO), infra-red (IR), synthetic aperature radar (SAR-high resolution video or still images), moving target indicators (MTI), and Electronic Support Measures (ESM- electronic emissions.) Their aim is “dominant battlespace awareness”- having more eyes and ears feeding more situational awareness back into the network than anybody else.” See: Drone kill communications net illustrated by Mark Ballard in ComputerWeekly.com.
271. Mycelial intelligence netorks: SW: Run by underground IBM computers. Refers to mycelial manipulation inside muscle strata in humans, having to do with electronic manipulation of mushroom fungus, candida, inside humans. (Article title: “Unleashing the Mycelial Intelligence: Nature’s Blueprint for Resilient AI and Innovation”)
272. N-3: DARPA’s Next-Generation Non-Surgical Neurotechnology.
273. N-Sphere math:
274. NASA: Started and continued by Nazis imported to US through the CIA’s Operation Paperclip.
275. NATO Targeting: The US formed a coalition to form a web of NATO netcentric targeting systems. Targeting intelligence is gathered on the fly by from surveillance gathered by any number of NATO countries that happened to have forces, sensors, or data bases with something to add to the kill equation. See: Drone kill communications net illustrated by Mark Ballard 2014, in ComputerWeekly.com.
276. NTS-3: The NTS-3 satellite, designed, built and tested by L3Harris, is an experimental platform designed to prove resilient, robust and reprogrammable PNT (Position, Navigation, Timing) functionality in space. (I.e., electronic targeting). (L3Harris just celebrated their 60th birthday. That’s how long this electronic warfare program has been going.)
277. Nano Avionics: People can be logged into from tiny nano-cube satellites above. See NTS-3 above and nano-cube satellites below.
278. Nano-cube satellites:
279. Nano-Morgellons Disease: Result of electrocuting people with this system.
280. Nano-neuro-technology: Nano-neuroparticulate agents so small they go through brain-blood barriers are used to create a hemorrhage disposition in the brain, and thus, strokes. Neurovascular hemorrhagic agents (for in-close and population use as “stroke epidemic” induction agents) are highly disruptive. Are injectable (through shots), ingestible (through eating or drinking), and intra-nasal (through breathing). (Dr. JG).
281. Nano-therapeutics: Utilizes the of nanomaterials to alter the pharmacology of the drugs and therapies being transported, leading to changes in their biological disposition (absorbtion, distribution, cellular uptake, metabolism and elimination) and ultimately, their pharmacological effect.
282. Nano-theronostics:SW: Bioengineering with nanotechnology; “Nanoparticles are key components of the nanotheronostic agent, which includes aptamer, DNA nanostructure, lactosome-based nanoparticles, metallic nanoparticles, gold nanoparticles, silver nanoparticles, dendrimer and co-polymer based nanoparticles, lipid-based nanomaterials,
283. Nano-Transducers:
284. Narrow Band (NB) wireless band (2.4 Ghz) frequency band: Most WBAN operates within this frequency band.
285. Naval Post-Graduate School (Monterey, California) Free-Space Optics Communications For Low-Powered Hand-Held Mobile Devices: I.e., Cell phones. “Tensor flow, tensor-flow-trained IBM Watson built the model, android application, JAVA C++ API, Col. Interpreter and android neural network API. Neural-network. More Machine-Learning. More augmented reality… electromagnetic spectrum you can choose from include Visible Light, Infra Red, Mid-IR, Far IR, Ex. High Frequency, SHF, UHF, VHF, HF, MF, LF, VLF, ULF, SLF, ELF in microwaves and radio waves. I.e., for Integrated Disease Surveillance System, specific APIs that have to do with wireless tissue engineering, make you throw up or pee, whatever.”
286: NATO Targeting: “The US formed a coalition to develop a web of NATO net-centric targeting systems. It would get target intelligence on the fly from surveillance gathered by any number of NATO countries that happened to have forces, sensors, or data bases to add to the kill equation.” (from ComputerWeekly.com)
287: Netcentric Targeting (also: Net Targeting or Global Netcentric Surveillance and Targeting): The basis of net-centric warfare- making everything available as a software service on the military internet. It involves combining different surveillance and sensors and intelligence data bases on the fly to get an automated fix on the target. The preeminent application of netcentric targeting is the one that made US targeted killing possible: time-critical or time-sensitive targeting. Netcentric targeting relies on a process called data fusion or semantic interoperability. Netcentric targeting developers wrote civil databases into their plans too, such as immigration databases and feeds from civil intelligence agencies.
288: (US) Network-Centric Collaborative Targeting System (NCCT): Became operational in 2007. “Combined with algorithms that watch for target signatures, this creates the means to spot targets on the fly. It creates the means to spot targets as small and fleeting as people and to kill them within minutes.” The NCCT became operation in 2007 after years of collaboration with the UK, according to DOD statements to Congress. Computer Technology Associates (CTA), a defense and intelligence contractor, helped develop this system. An example describes a target signature: an algorithm tells the targeting system that in the event of an emergency it should look out for a particular person, known to the Central Intelligence Agency (CIA) as as “target ID 1454.” The targeting system keeps watch for them with its Blue Force and Red Force tracking systems. The military uses these to trace the movements of those they’ve classified as goodies and baddies. The Red target list is the general hit list. The targeting system sends geographical coordinates to people in green uniforms. See: Drone kill communications net illustrated by Mark Ballard, 2014, ComputerWeekly.com.
289. Network Centric (Net-Centric) Warfare: An industrial, international system that uses cognitive body area networks and watches you think in real time. Used for net-centric node access; uses drone-kill communications. SW: Uses anything they can access on the internet. Military doctrine of war. Take advantage of everything and fire some more.
290. Network Killing: SW: The network carries the intelligence that selects the targets. It runs the software that directs the operation. It incorporates the drones that carry out the strikes. The network made targeted killing possible. The network was also the basis of the mechanism that drove the actual strike operations. It carried the intelligence that selected the targets. It ran the software that directed the operations. It incorporated the drones that carried out the strikes. The drones are nodes on the network. The network IS the weapon.
291. Network Operations Center (NOC):
292. Neural Nano-robotics:
strong>293. Neural nets: Are at the core of AI involve over a trillion dollars of financial trading.
294. Neuro-hacking: According to Dr. James Canton, includes the ability to create thoughts and blend them with AI. Everything is hackable- health devices, routers, (and the mind) are all hackable. (Most devices that are networkable are hackable). Neuro-hacking allows us to adjust memories at the nano-scale.
295. Neuroinformatics:A research filed devoted to the development of neuroscience data and knowledge bases together with computational models and analytical toos for sharing, integration, and analyses of exerimental data and advancement of theories about the nervous system function.
296. Neurological or brain signatures: Dr. JG: “We are tracking neurological signatures of key targeted individuals that are thought to represent whole groups. If I understand how his or her brain works and do this on a broad enough scale, I can develop patterns and I can use this in ways that informs my intelligence; this force multiplies and synergizes my human intelligence (HUMINT), my signals intelligence (SIGINT), and my communications intelligence (COMINT). NEURINT (Neuro intelligence) coupled with assessment and access gives me these capabilities. I can utilize neuro-pharmacologics and various forms of brain stimulation to extract information from key intelligence targets.”
297. Neuro-microbiological agents (neuromicrobials): are deployed to make people extremely sick. Neuro-microbials with high neuro-psychiatric symptom clusters produce public panic/public health disintegrative effects. Gene-edited microbiologicals have novel morbidity/mortality profiles. These weapons are used to target key individuals in various, different communities to produce statistical information useful in creating short- and long-war effects. “In a long-war scenario, I can reduce productivity and health of individuals, communities, and nations.” (Dr. JG).
298. Neuromodulation:
299. Neuro-Moore’s law: Now we all live in Neuro-Moore’s law. We have ever-shrinking, ever-more powerful devices. (Referring to the (Havana Syndrome) attacks on American diplomats at the Cuban and Chinese embassies). Advanced neuro devices include “soft” (“nonlethal”) and “hard” (lethal) neuroweapons.
300. Neuromorphic chip set:
301. Neuromorphic computing:
302. Neurons: Within a nervous system, a neuron, neurone, or nerve cell is an electrically excitable cell that fires electric signals called action potentials across a neural network. Neurons communicate with other cells via synapses – specialized connections that commonly use minute amounts of chemical neurotransmitters to pass the electric signal. There are an estimated 86 billion neurons and they are body-wide.
303. Neuron-Colon-Neuron (NCN):
304. Neuroscience: today is an “integrative” (interdisciplinary) science involving cyberscience/technology, Anthro-social sciences, Natural sciences, Biotechnology, Nanoscience/technology and has important applications in the fields of National Defense, Intelligence, and National Security. (Dr. J. Giordano)
305. Neuroscience/technologies: 1) increases military/intelligence “Human Intelligence” (HUMINT), “Signals Intelligence” (SIGINT), “Communications Intelligence” (COMINT), and “Neural Intelligence” (NEURINT) capabilities, 2) improves intelligence operators and warfighters’ (so-called “super-soldiers”) cognitive skills, emotional capabilities, and certain behaviors and actions, and include:
a) advanced neuro-pharmacological agents (drugs),
b) computational brain-machine interfaces,
c) closed-loop brain stimulation approaches (implants and transcranial and magnetic electrical stimulation), and
d) neuro-sensory augmentation devices, or bioengineering, to increase visual acumen to create cochlear and auditory implants- i.e., “eagle eye” or “bat’s ear.”
306. Neuroscience/technology “Intervention” techniques: include: a) cyber-linked neurocognitive manipulation (presumably including “Remote Neural Monitoring, Remote Neural Manipulation” and neurostimulation), b) novel Pharmaceuticals, c) neuro-microbiologicals, d) organic neurotoxins, and e) neurotechnologicals. (Dr. James Giordano)
307. Neurosensory immobilizing agents: include high-output sensory stimulators which can be administered by UAVs (unmanned aerial vehicles), drones, or insect borne, or by large vehicles such as cars or tanks. Sensory mobilizing agents use high electromagnetic pulse energy that may also use high levels of sound and light energy to disrupt neurosensory functions. (Dr. JG).
308. Neurotechnologies/Neuroweapons: Two parts of Neurotechology include: 1) “soft” or “nonlethal” dimension, a weapons system to create cognitive impairment of individuals, that creates dysfunctionality and cognitive impairment, inability to make good decisions, dizziness, health effects. 2) the “hard” dimension refers to killing people. Dr. James Canton: “Neurotechnology will drive the next “hybrid war,” which has already started.” Lethal neurotechnologies include:
a) Microwave RF Anti-Functional and Anti-Personnel Weaponry
b) Chemical Anti-Functional Weaponry
c) Chemical Psychological Effects Via Sensory Organs Weaponry (i.e., smell)
d) Chemical Personnel Incapacitation Weaponry (Non-warfare, hostage/terrorism only)
e) PSYWAR
f) Acoustic Weaponry
g) Mechanical Micro Dust
3) Neuro-reprogramming is the likely driver for defeating age-related diseases; to revitalize and rejuvenate even your brain.
4) “Fantastic futures” include artificial immune system, synthetic tissue, cellular systems, living cells as bio-foundries, proteomic targeting for cancer cells and other diseases, low cost designer drugs.
(From: Neuroweapons, “Dark Network Supply Chains,” “Man-Hunting Business” (aka GANGSTALKING) & “Hybrid Warfare;” Presentation By Dr. James Canton (Video, Transcription, and My Commentary)).
309. NeuroWars: Dr. JC: Near future to 25 years: Progression: GPS Mining Predictive Analytics, Facial NeuroTech Genomic Targeting, Alert Avatars, Smart Swarms, RoboNets, Human Synthoids. I came up with the concept of “Dark Networks” when I was advising SOCOM (Special Operations Command) on this concept of “Bad Guy Hunting-Targeting”…..
310. Neurostimulation:Neurostimulation is the purposeful modulation of the nervous system’s activity using invasive (e.g. microelectrodes) or non-invasive means (e.g. transcranial magnetic stimulation or transcranial electric stimulation, tES, such as tDCS or transcranial alternating current stimulation, tACS). Neurostimulation usually refers to the electromagnetic approaches to neuromodulation. (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com))
311. Neutrino arrays: SW: The largest is in Antarctica. Others are all over, including University of Wisconsin, Madison, Las Vegas, and West Virginia. These have huge magnets underground and overhead. These are watching you and pertebating your biofields with bioelectromagnetic algorithms for DNA-sequencing events, i.e., between human to human.
312. NIPRNET: Non-classified Internet Protocol Router Network is an IP network used to exchange unclassified information, including information subject to controls on distribution, among the private network’s users. The NIPRNet also provides its users access to the Internet. It is one of the United States Department of Defense’s three main networks.
313: Non-Invasive Nonsurgical Neurotechnology (N3- DARPA): The four-year N3 program focuses on two main aspects: noninvasive and “minutely” invasive neural interfaces to both read and write into the brain. Because noninvasive technologies sit on the scalp, their sensors and stimulators will likely measure entire networks of neurons, such as those controlling movement.
Energy is applied through: ultrasonic pressure waves, microwaves, circular polarized beams (EM cyclones), gamma rays, 2-D and 3-D phased arrays, beam steering, forming, nonlethal weapons, neuroweapons.
314. Non-invasive Neuro Technologies: Include ultrasound, light, radio frequencies, magnetic fields, RHIC, Electronic Dissolution of Memory (EDOM), RNM, S-Squad, etc.
315. NIST: National Institute of Standards and Technology:
316. Noninvasive methods for Neurostimulation:
317: Noninvasive N3: SW: nano-lobotomy
318. Noninvasive N3 Neuron Exchange:
319: Nonlethal weapons: Directed energy weapons, neuroweapons.
320: North Atlantic Treaty Organization (NATO): The US began building common surveillance systems with its partners in NATO. The more sources of intelligence they had, the more sources they could see.
321. North American Network Operators’ Group (NANOG): An educational and operational forum for the coordination and dissemination of technical information related to backbone/enterprise networking technologies and operational practices.” Participants/sponsors include Linkedin, Facebook, Instragram, Twitter, Cisco, ICANN, Internet Engineering Task Force, Internet Society
322. Obama Death Panel Data Base Carrier Waves: SW: These will go out with the CBDCs
323: OMNeT: OMNeT++ is an extensible, modular, component-based C++ simulation library and framework, primarily for building network simulators. “Network” is meant in a broader sense that includes wired and wireless communication networks, on-chip networks, queueing networks, and so on. SW: Software to model your body area network.
324. Open Network Airborne Computing Platform: National Science Foundations new optic networks. This is automous military since 2012. Genetically targeted hemodynamic functional imaging.
325. Open Shortest Path First (OSPF): SW: method of routing RF through the body.
326. Operations Security (OPSEC): Military term
327. Optical Coherence Tomography: SW: Process is used to change the cell structure in the human body.
328. Optic corridor: National Science Foundation
329. Optical Wireless Communications:
330.Optically Pumped Magnetometer:
331. Opto Array:
332. Optogenetics: Wiki: A biological technique to control the activity of neurons or other cell types with light. This is achieved by expression of light-sensitive ion channels, pumps or enzymes specifically in the target cells. On the level of individual cells, light-activated enzymes and transcription factors allow precise control of biochemical signaling pathways.
333: Optogenetics in Neural Systems: Interdisciplinary by nature, optogenetics requires (1) engineered control tools that can be readily targeted to specific cells, (2) technologies for light delivery, and (3) methods for integrating optical control with compatible readouts (such as fluorescent organic or genetically encoded activity indicators, electrical recording, fMRI signals, etc.
334. O.R.I.O.N.: SW: Google’s Software-Defined Networking Control Plane for your body.
335. Palantir:
336. Pathfinder Software: Pathfinder is a software that simulates evacuation and general pedestrian movement in various buildings. It offers advanced features, training, and support for AHJs and professionals. SW: Project MAVEN uses Pathfinder and AI to watch you walk around and think while you are in your house.
337. Personal Area Network (PAN): 6th generation wireless (6G)
338. Photonic:
339. Phys.org: A network of body monitoring devices using our own tissue as the basis for the internet of bodies.
340. Pilo-erection: Stimulation of one’s own biofield through concentration. Makes hair stand on end and generates stem cells.
341. Plasma Core Structure that Matches your DNA: your digital twin
342. Plasmotics: The generation, detection, and manipulation of signals at optical frequencies along metal-dialectic interfaces in the nanometer scale.
343. Positron Emission Tomography (PET): PET scanners emerged in the 1970s, allowing further investigations into the brain’s metabolic activity.
344. Precision Artificial Intelligence Wireless Health Care: SW: Reaching down to your bone marrow and controlling every cell in your body. With the SMART City agenda, we just log in and play you like a video game.
345. PRISM (NSA): Initially top-secret, now a reported fact, a program of the National Security Agency (NSA) through which it gets direct access to tech companies’ servers. The agency receives users’ information, including emails, SMS, videos, chat messages, browsing history, and other sensitive data. Most high-tech companies like Microsoft, Facebook, Google, and Apple are bound to give access via PRISM. Its official purpose was to facilitate the surveillance and protection of US citizens. However, it threatens the users’ privacy policy globally.
346. Project Lasso (Low-Altitude Stalking and Strike Ordinance) aka Lasso Program: is a: “manned-portable, tube-launch, lethal payload munition, unmanned, aerial system, including electrical, optical-infra-red sensor precision flight control and the ability to fly, track and engage non-line-of-sight targets and armored vehicles and precision-lethal fires. Lasso consists of three modulars; modular open system approach, used by Infrantry Brigade Combat Teams (IBCT), plasma warfare, autonomous drones.”
347. Project Looking Glass (CIA black project): SW: Involves routing radio frequencies through and looking through the body and setting up the MAC ID in the body (802.15.4/5/6) and lining it up with DNA.
348. Project MAVEN: SW: Is Mosaic Warfare/net-centric warfare for net-centric node access. WBANs (you) can be accessed by non-invasive N3 with optogenetics, EEG, your internet service provider, SMART Grid, UAVs (drones), radio-man net, Infra-red, infra-sonic, wireless sensor networks, brain-to-brain, peer-to-peer, front hall-back hall, biophotonics, nano-Cube-sat, MAC IDs, Personal Area Network (PAN); just anything can be brought up to access the target. The system is Tethered to the Ground with Agile POD Conduit on MQ-9 Reaper from the US Air Force for the Pathfinder Project with Object Detection with VMF underneath the contract tools from DOD Datamax Project Tradewinds Umbrella. We can order a drone update or a smart grid update. We can log in to your body with OM-Net software, 801.15.6. MQ-9 Reaper is tethered to ground, can do a scan, and can hunt you down wherever you are. Project MAVEN uses Pathfinder and AI to watch you walk around and think inside your house. It’s a machine to machine (M2M), vehicular, ad hoc on the fly network built for humans with the soft-kill systems which have to be there for electronic warfare because we don’t just target tanks and planes.
Google walked out on Project Maven. I.e., Maven was too evil even for Google.
349. Project OSIRIS: Slaughter bots program; US Marine Corps, Maryland-based, AT&T (Southern Bell, Bell Labs), helicopters (acopter)
350. Project Pandora: SW: “Uses wireless body area network to teleport DNA. Putting you in a special chair with specialized biophonic concrete or metamaterials under your feet that could translate back and forth and teleport materials and humans. Most importantly to build a CBRN (Chemical, Biological, Radiological and Nuclear (CBRN)) DNA biofrequency weapon secure skiff for themselves as they terra form the particulates in the atmosphere (prima materia) (because they have friends in the 4D.”
351. Project Pegasus: An Israeli Phoenix Program on American Soil; An international investigative journalism initiative that revealed governments’ espionage on journalists, opposition politicians, activists, business people and others using the private Pegasus spyware developed by the Israeli technology and cyber-arms company NSO Group. Pegasus is ostensibly marketed for surveillance of “serious crimes and terrorism”. In 2020, a target list of 50,000 phone numbers leaked to Forbidden Stories, and an analysis revealed the list contained the numbers of leading opposition politicians, human rights activists, journalists, lawyers and other political dissidents.
351. Project SALUS (Sentient AI): SW: Drones watching everyone think and everyone’s cells phase and phage states in real time with C2TWS (Cognitive Technology Threat Warning System). It is watching your biosensors- watching you from the inside out with the body area network. Has been around since 1969. SALUS platform is used by US Northern Command (Northcom) with upgrades out to vendors. It uses the neural prototype, Synchron. Aka Project Salvation. 7 billion people is the marker. Project Salus overrides God’s Holy Spirit Frequency.
352. Proteome: content of proteins in a cell
353. Proteonomics: re-writes your protein
354. Protocol Data Unit (PDU): In telecommunications, a protocol data unit (PDU) is a single unit of information transmitted among peer entites of a computer network (sabrina: that would be you, you’re a node on a computer network.). It is composed of protocol-specific control information and user data. (Sabrina: On the Cisco backplane of your cable company).
355: Position, Navigation, and Timing (PNT) from satellites: NTS-3 operates with this.
356. Psinergy: Psi plus energy= our own neurons (name of Sabrina Wallace’s website)
357. Psionics: Psychic abilities, including telepathy, empathy, precognition, telekenetics, teleportation. These are neurons.
strong>358. Psychological Operations (PSYOP): Operations used in psychological warfare.
359. Quantum computers/omputing: got really going in 1980s
360. Radio Access Network (RAN): RAN uses N2 (control plane) and N3 (user plane) to interface to the core and transparent N1 interface to the user devices. N1 is a transparent interface from 5G-UE to AMF of core(via NG-RAN). … N2 uses SCTP (NGAP) between 5GCN and access network.
361. Radio Frequency Identification (RFID): chips used in humans to locate them via radio frequencies; installed in humans beginning in 1950s with John Van Neumann software and architecture.
362. Radio Frequency (RF) Industrial, Medical, and Scientific Bands:
363. Radio Frequency Sinks: SW: These are located over the heart and stomach. The RF sinks pull the radio frequencies from other nodes in the body on 802.15.4 and 802.15.5 IP addresses.
364. Radionics:
365. Radiowave based communication: (SW: aka “Vril Maiden based communication”), includes, for example, Bluetooth.
366. Raraneous Chip Set: SW: Already installed in the brain that have their own operating system.
367. Rectenna: is a special type of receiving antenna that is used for converting electromagnetic energy into direct current electricity. They are used in wireless power transmission systems that transmit power by radio waves.
368. Remote Functional Brain Imaging:
369: Remote Neural Monitoring (RNM): currently being performed by the means of Measurement and Signal Intelligence (MASINT) on a large scale and it allows the extraction of sensory perceptions and associated mental processes and emotions using Artificial Intelligence.
i.e., detection of neural activity from a distance via:
a) detecting the magnetic fields produced by the brain electrical activity using Magnetometry
b) Multispectral Radio Acoustic Tomography: By illuminating brain tissues with pulsed radio waves, tissues absorb the radio waves pulses, and as a result undergoes thermo-elastic expansion. This expansion gives rise to ultrasound waves that can be detected by Microwave Vibrometry and formed into an image.
c) Microwave Spectroscopy
d) High-Sensitivity Electric Potential Sensors are used to perform contactless Electroencephalography.
e) Near Infrared Spectroscopy (NIRS) estimates the concentration of hemoglobin from changes in absorption of near infrared light.
f) Infrared Thermography: based on the fact that all objects with a non-zero temperature give off thermal infrared energy, considering the human body emits around 300W of infrared mainly at the wavelength of 12 μm, it is possible to perform functional imaging of the cerebral cortex based on its infrared radiation. This is called Thermoencephaloscopy.
g) Artificial Intelligence, the activity of the different brain areas can be analyzed:
– decoding of the visual cortex allows extracting visual perception, visual imagery during waking state and visual imagery during sleep.
– decoding of the auditory cortex allows extracting auditory perception and inner speech.
– decoding of the somatosensory cortex allows extracting the sensations of touch, temperature, pain, and proprioception.
– decoding of the motor cortex allows extracting body motion.
– decoding of the gustatory cortex allows extracting senses of smell and taste.
– all cognitive processes can be extracted from different brain areas.
370. Remote Neurostimulation: Can be accomplished through:
a) Brain Implants : see Neuralink and Synchron Stentrodes. Stentrodes can be delivered to the brain through the vascular system using a catheter and do not require neurosurgery.
b) Focused Ultrasounds interact with cell membranes and mechanosensitive Ion Channels and can trigger Action Potentials. Ultrasounds can be delivered to the brain by the mean of Radio Frequency Electromagnetic Waves turning into Ultrasound waves through the Optoacoustic Effect. Solitons waves which are waves that maintain their shape and speed over long distances can be used to achieve more efficient data transmission.
c) In Graphene, plasmons which are collective electron oscillations can be excited by electromagnetic waves in the terahertz frequency and by entering in resonance produce a strong enough current to activate surrounding population of neurons.
d) Magnetic activation of thermosensitive or mechanosensitive ion channels using magnetoelectric nanoparticles under the influence of an electromagnetic field to trigger action potentials.
e) Transcranial magnetic stimulation (TMS) to induce an electric current at a specific area of the brain through electromagnetic induction which can then either depolarize or hyperpolarize neurons at a site.
f) Magnetogenetics: by delivering to the brain specifically engineered genes that code for a magneto sensitive protein by the mean of a Virus, it becomes possible to activate specific populations of neurons by remotely applying a magnetic field to the brain.
g) Neuralnanorobots: remote controlled nanorobots able to traverse the blood brain barrier, enter the brain parenchyma, ingress into individual human brain cells, and autoposition themselves at the axon initial segments of neurons (endoneurobots), within glial cells (gliabots), and in intimate proximity to synapses (synaptobots) can perform very precise neurostimulation.
h) Radiogenetics could allow delivering to the brain specifically engineered genes that code for a radio wave sensitive protein by the mean of a Virus and then performing Neurostimulation by the mean of Radio Frequency.
(From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com)).
Remote Neurostimulation (applications): allows for a wide range of applications including:
a) Experiencing another person’s life in full immersive virtual reality by replicating the brain electrical activity of an individual undergoing remote neural monitoring, it allows inhabiting its mind and body and experiencing its 5 senses and associated mental processes and emotions.
b) Full immersion in a virtual reality engaging all five senses (sight, sound, touch, taste and smell). By allowing anyone to project its mind at will in the virtual reality of its choice and materialize an abundance of unlimited goods and services, it potentially allows each one of us to fulfill all of our wishes.
c) Erase and create memories : by mastering the process of encoding and retrieval of complex memories and memory attributes, including their hierarchical associations with one another through neurostimulation it allows complete reprogramming of an individual.
d) Delivering non-pharmacological treatments. The human brain undergoing neurostimulation has the capability to synthesize a very large number of chemicals that can act as drugs.
(From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com)).
371. Schumann cavity: Approximately the lower 50 miles of the earth’s atmosphere between the earth’s surface and the ionosphere.
372. Schumann Resonances: Set of resonance peaks in the extremely low frequency (ELF) part of the earth’s electromagnetic spectrum around 7.8 Htz. The fundamental mode is a standing wave in the Earth-ionosphere cavity with a wavelength equal to the circumference of the Earth.
373. Sensor Hunters: Police, military, special forces, citizen vigilante groups, gangstalkers, gangstalking perpetrators who track the biosensors in targeted individuals.
374. Sensors Open System Architecture (SOSA): program used on drones to locate targets and create electromagnetic field above target’s home. Used for Precision AI Health Care. To make CRISPR-CAS-9 genetic changes. To change cell structure. To irradiate human biofield.
375. Sentient World Simulation: (aka “the metaverses”): Continuously run mirror model of the real world alimented by people’s Functional Neuroimaging data and by Hyperspectral Imaging data to build a real time 3D model of the world.
376. Signals Intelligence (SIGINT):
377. Signature Reduction Force (SIGREDUX): Sabrina: “The Finders (CIA pedophiles) in the white vans (of the 1980s), we turned them into Local Logistics and the Signature Reduction Force and gave them a pay check with retirement benefits. They have a human-frequency DNA board to drive around and zap people back into submission.”
378. SIM (Subscriber Identification Module): real-life video game players can play real people like SIMS.
379. SIPRNet: Secret Internet Protocol Router Network (SIPRNet) is “a system of interconnected computer networks used by the U.S. Department of Defense and the U.S. Department of State to transmit classified information (up to and including information classified SECRET) by packet switching over the ‘completely secure’ environment”. SW: Includes Drone Kill Communications Network
380. Skyborg: Skyborg is an unmanned aircraft focused competency that will allow the Air Force to employ a team of artificially intelligent aircraft to quickly thwart adversaries in combat. Skyborg will not replace pilots but will provide crucial and prompt data to help the pilot make informed and accurate decisions. As of 2020, contracts have been awarded to Boeing, General Atomics, Kratos Unmanned Aerial Systems and Northrop Grumman.
381. SKYNET Surveillance Program: Wikipedia: A U.S. National Security Agency (NSA) program that performs machine learning analysis on communications data to extract information about possible terror suspects. The tool is used to identify targets, such as al-Qaeda couriers, who move between GSM cellular networks. Specifically, mobile usage patterns such as swapping SIM cards within phones that have the same ESN, MEID or IMEI number are deemed indicative of covert activities. Like many other security programs, the SKYNET program uses graphs that consist of a set of nodes and edges to visually represent social networks. The tool also uses classification techniques like random forest analysis.
NSA directorates participating: Signals Intelligence: S21, S22, SSG, Research: R6, Technology: T12, T14
It has partnerships with TMAC/FASTSCOPE, MIT Lincoln labs and Harvard. The SKYNET project was linked with drone systems, thus creating the potential for false-positives to lead to deaths. According to NSA, the SKYNET project is able to accurately reconstruct crucial information about the suspects including their social relationships, habits, and patterns of movements through graph-based visualization of GSM data. However, scholars criticize that current security literature conflate statistical discrepancies with behavioral abnormalities and that the anomaly detection methodology SKYNET perpetuates the self/other binary.
References:
1) Grothoff, Christian; Porup, J. M. (16 February 2016). “The NSA’s SKYNET program may be killing thousands of innocent people”. Ars Technica UK.
2) “SKYNET: Applying Advanced Cloud-based Behavior Analytics”. The Intercept. 8 May 2015.
3) NSA. “SKYNET: Courier Detection via Machine Learning”. Snowden Doc Search. Archived from the original on 2019-12-08. Retrieved December 7, 2019.
4) Crockford, Kade (8 May 2015). “MIT and Harvard Worked with NSA on SKYNET Project”. Privacy SOS.
5) Robbins, Martin (18 February 2016). “Has a rampaging AI algorithm really killed thousands in Pakistan?”. The Guardian.
6) Aradau, Claudia; Blanke, Tobias (February 2018). “Governing others: Anomaly and the algorithmic subject of security”. European Journal of International Security. 3 (1): 1–21. doi:10.1017/eis.2017.14. ISSN 2057-5637. S2CID 58923172.
7) http://cdn.arstechnica.net/wp-content/uploads/sites/3/2016/02/skynet-courier-detection-via-machine-learning-p17-normal.gif[bare URL image file]
382. S.M.A.R.T. (Specific, Measurable, Achievable, Relevant, and Time-Bound) City agenda operates off of the Body Area Network.
383. Social Security’s AI Precision Health Care. SW: Stipulates that we can wirelessly adjust your cells and tissue. This is going out right now (Oct. 2023). Uses photonic tools for remote medical diagnoses.
384. Software with human bodies: utilized since 1972
385. Special Access Project (SAP): Black projects, including the Targeted Individual Program
386. Special Information Operations (SIO):
387. Spells: SW: A logical feature value inside of GEOMANCER where we hunt you down by your body part digitally and log in.
388. Spellbook: Everyone has this. Your spells are tied to your Digital ID. This provides your feature values; age, weight, bank account, etc. (COV-BAN, Google Fingers). The name and process suggest the demonic/witchcraft elements of this system.
strong>389. Spellcaster: The name and process suggest the demonic/witchcraft elements of this system
390. Spike proteins: take measurements of your neurons and neurons are body-wide
391. Structured Query Language (SQL) Hive: SW: Transhumanist agenda is “to create a collective consciousness (hive mind) that will ensure that evil progresses without defiance.”
392. Stargate Project: Starting in 1978, the CIA’s Stargate Project aimed at developing Remote Viewing to allow seeing through anyone’s eyes by the mean of Remote Neural Monitoring or to be able to visualize any distant scene reconstructed in 3D by the way of Hyperspectral Imaging.
393. “Star-Seed Narrative:” CIA narrative, concerning certain groups like the Pleidians, Sirius, Orion, etc. that people with psionic abilities (telepathy, clairvoyance, etc.)
394. “Star Seeds:” (Sabrina Wallace’s definition): “A special breed of gullible people who are deeply hurt, traumatized and kept that way because they have real psionic abilities. These are the first people on the list to be targeted for transhumanism because they have neurons that have natural telepathy, empathy, and precognition that they subsume as a matter of their job, their patents, and their N-Sphere map. You are not going to another star system, I’m sorry, you are going to a liminal space, the Rydberg-atom toroidal field. We know how to modify everything within you at every cell density. And we have all chakras locked down with little lenses that report back and forth to those neutrino optical arrays in Antarctica and everywhere else with the doppler and everything else that we watch with radar. Sabrina: “These are Special Access Projects (SAPs). We make EBE’s (Engineered Biological Entities). We torture people into submission and we create hybrids.”
395. Stimoceiver: The first Brain Implant allowing stimulation of specific areas of the brain and Neuromonitoring to be performed by the mean of Radio Frequency. Invented by José Manuel Rodríguez Delgado in 1963. (From: Neurotechnology and Transhumanism: The big fraud towards Digital Slavery (From Remote-Neural-Monitoring.com)).
396. Steganographic covert communications: Steganography is a form of covert communication which hides the transmitted data from a third party even without encryption. In the context of wireless communications, spread spectrum techniques to hide information in channel noise have been explored which comes at the expense of extra communication energy. While the EQS-HBC transmitted signals suffer low loss, the leaked EQS-HBC signals are concealed within noise for an attacker, thereby showing promise to enable covert stenographic communication in the form of an inherent physical layer security.
397. Stingray: Stingrays, also known as “cell site simulators” or “IMSI catchers,” are invasive cell phone surveillance and tracking devices that mimic cell phone towers and send out signals to trick cell phones in the area into transmitting their locations and identifying information. Used by police and Sheriff’s departments to track TIs.
398. Structured Query Language (SQL): A programming language for storing and processing information in a relational data base.
399: Structured Query Language (SQL) Hive Data Bases: A relational data base stores information tabular form, with rows and columns representing different data attributes and the various relationships between the data values.
400. Structured Query Language (SQL) Hive: SW: is for C-40 cities.
401. Sudden Adult Death Syndrome (SADS): new name for death caused by electrocuting people’s biofield using this electronic warfare system
401. SynChron:
403. Synthetic Aperature Radar:
404. Synthetic biology:
405. Synthetic telepathy: aka Voice-to-Skull (V2K), Voice of God, Microwave Hearing
406. Targeted Individual: Those blacklisted civilians who are tracked, surveilled, and subjected to gangstalking abuse and harassment 24/7 as well as internal frequency monitoring and manipulations on RF Industrial, Medical, Scientific Band of 2.4 THz (WBAN 802.15.4, 802.15.5, 802.15.6) since the 1950s and 1960s.
407. Targeted Killing: Based on SIPRNeT, this network centric targeting became the means of a chilling new form of warfare, “targeted killing,” based on computer-driven, intelligence-led, extra-judicial assassinations of suspected terrorists. The UK connection was part of this because under the targeted killing programme, the network is the weapon. See: Drone kill communications net illustrated by Mark Ballard, 2014, ComputerWeekly.
408. Target signature:An algorithm tells the targeting system (NCCT) that in the event of an emergency, it should look out for a particular person, known to the Central Intelligence Agency (CIA) as “target ID 1454.”
409. Targeted Killing:Netcentric warfare.
410. Telemetry: (aka bio-telemetry). The science and technology of automatic measurement and transmission of data by wire, radio, or other means from remote sources, as from space vehicles, to receiving stations for recording and analysis. Communication and information transfer between computers and biological systems such as your body.
411. Telephony: SW: The biofield was connected to telephony in 1922.
412. Tensor sequences of Artificial Neural Networks:
413. Terrahertz (THz) bullet: Based on the Lora (LoRaWaN; Low Power, Wide Area networking (LPWA)), air molecules turn into a fist or a knife. Effects can be fatal and look like a stroke or a heart attack. Plausible deniability.
414. Teslaphoresis: Scientists at Rice University have discovered that the strong force field emitted by a Tesla coil causes carbon nanotubes to self-assemble into long wires, a phenomenon they call “Teslaphoresis.”
415. Thermal Dynamic (RF) Frequency Routing Through the Body: SW: We have this since 2013.
416. Thermoencephaloscopy: Based on the fact that all objects with a non-zero temperature give off thermal infrared energy, considering the human body emits around 300W of infrared mainly at the wavelength of 12 μm, it is possible to perform functional imaging of the cerebral cortex based on its infrared radiation. (Infrared Thermography)
417. Time-Sensitive Targeting/Time-Sensitive Targets (TST): “TST gives friendly forces (us) the option of striking targets minutes after they are identified.” “These could include “lucrative” targets that appeared in the surveillance net only fleetingly and therefore had to be attacked quickly,” according to NATO’s chief scientist in 2013. Examples of TSTs include “terrorist leadership” and “enemy of SOF” (special forces). TST is commonly known as the kill chain and has 6 steps: find, fix, track, target, engage, and assess. See: Drone kill communications net illustrated by Mark Ballard, 2014, ComputerWeekly.com.
418. TITAN (Tiered-integrated Tracking and Access Networks): Utilizes biologically-implantable chips to track key individuals and provide information about the way brains work to create narratives and behaviors. (Dr. JG).
419. Torus Manifold:
420. Tracking Systems: Blue Force and Red Force: The military uses these to trace the movements of these they have classified as goodies and baddies. The Red target list is the general hit list.
421. Toroidal field: “A toroidal field (toroidal is based on the word “toroid” that simply means doughnut shaped) that looks like this is what we medical intuitives would like to see when we observe your energy field.”
422. Trans- and intracranial pulse stimulators: use direct electromagnetic pulses to disrupt the network aggregation-network properties of the brain and create confusion. These are both individual and group disruptors. These neural network “confusion generators” can be hand held or delivered by UAV, drone, and insects. (Dr. J.G.)
423. Transcranial Electrical Stimulation: In 1980 P. A. Merton and H. B. Morton successfully used TES to stimulate the motor cortex.
424. Transcranial Magnetic Stimulation (TMS) (fTMS): Noninvasive method of monitoring and manipulating brain waves.
425. Transcriptomes: enables transcribing of CRISPR-CAS9 changes
426. Transformational Satellite (TSAT) Communications System:
427. Transhumanism: merger of humans with computers, including synthetic biology, life extension, prosthetics, brain-to-computer interface, merger of humans and machine. This WBAN cyber system is set up to electrically-rearrange people’s bio-electric code and bodies (transhumanism).
428. Ubiquitous Computing:
429. United States Air Force Sensor Operators: SW: Title of job of sensor hunters.
430. Ultra-wide body area network: RF bands for industrial, scientific and medical facilities
431. Video game controllers: Computer operators at work stations used in concert with drones to monitor and manipulate your WBAN and cells, etc.
432. Visible Light Communication (VLC): The use of visible light (with a frequency of 400-800 THz/wavelength of 780-375 um) as a transmission medium. VLC technology includes Li-Fi (Light Fidelity). VLC is a subset of optical wireless communications technologies.
433. Von Neumann cellular automoton:
434. Vril maidens: (by Lionsground) Maria Orschitsch, a member of the Vril-Gesellschaft obtained telepathically messages from extraterrestrials in a code language of the Knights Templar, a language that was unknown to her. The messages allegedly contain technical information about the construction of a UFO Hitler gave at the end of World War II mission to build flying saucers, claimed a report in the German science magazine PM.
Related: The Black Sun and the Luminous Lodge The Vril Society, the Luminous Lodge and the Realization of the Great Work
SW: The Vril Maidens were the original testing for routing the internet of things through the human body! Like Project Looking Glass, the Vril Maidens were radio frequency testing through the human body.
435. Whole Brain Functional Connectivity: Concurrent electroencephalography (EEG) and functional magnetic resonance imaging (fMRI) bridge brain connectivity across timescales. During concurrent EEG-fMRI resting-state recordings, whole-brain functional connectivity (FC) strength is spatially correlated across modalities.
436. Wireless Biomedical Tissue Engineering (aka regenerative medicine):
437. Wireless (or Wide) Body Area Network (WBAN): (aka Body Area Network (BAN), Body Sensor Network (BSN), Medical Body Area Network, MBAN) (IP address: 805.15.4/5/6). WBAN connects independent nodes that are placed in the clothes, on the body, or under the skin of a person (aka biosensors). The network expands over the whole human body and the nodes are connected through a wireless communication channel. The 802.15.6 Standard defines a communication standard optimized for miniaturized low-powered devices that are deployed on or implanted inside a human body for a variety of medical, non-medical and entertainment purposes. SW: People can log into your body WBAN with computer networking. “Your body is on someone’s network. That is a Dept. of Defense Directive.”
a) 802.15.4- Protocol is assigned to Bluetooth biosensors in the human body whcih are individually accessible via logins through CISA my tiny OS on cyber security; became commercially available in 2005.
b) 802.15.5- Protocol assigned to wireless sensor networks that create radio frequency relays and anything else they need to to pertebate cell structure on this band
c) 802.15.6 – Protocol is assigned to the human biofield (and body) since 1995 (2.4 THz). That is, your wireless body area network (WBAN) is the bio-frequency weapon, the network and the node.
The WBAN includes the medical (MBAN) and non-medical applications. Non-medical applications include human-computer interfaces (e.g., neural interface, virtual reality), location tracking, and personal fitness tracking. SW: (I.e., Vril Maidens).
SW: Wireless Body Area Network (WBAN) is you, your body, connected to the cloud.
438. WBAN Applications: Medical: Vital signs, respiration, Electroencephalogram (EEG), pH, glucose, muscle tension monitoring and hearing aid, disability assistance, speech disability, artificial hands; Non-medical: video streaming, data file transfer, sports, 3D video, Forgotten things, monitor; entertainment applications, gaming, social networking (Webmaster comment: remote torture)
439. “Weaponizable neuroscience technologies:” allow us to:
a) assess, predict and control particular cognitions, emotions, and behavior of adversaries,
b) mitigate aggression and foster cognitions, emotions and/or behaviors of affiliation or passivity in enemies,
c) induce morbidity, disability, or suffering and thus, “neutralize” enemies and/or potential opponents, or
d) induce mortality, that is, kill adversaries. (Dr. JG)
440. Wireless MANET networking: A MANET system is a group of mobile (or temporarily stationary) devices which need to provide the ability to stream voice, data, and video between arbitrary pairs of devices utilizing the others as relays to avoid the need for infrastructure. There are many techniques which are employed
441. Wireless Medical Telemetry Services (WMTS): Most often used for critical patient care.
442. Wireless Neighborhood Area Network (WNAN):
443. Wireless Local Area Network (WLCN):
444. WSN (Wireless Sensor Network):
445. Wireless Tissue Engineering: SW: It’s called Tissue Scaffolding with the DoD and HDIEC. For example, Morgellons. These filaments are controllable.
446. Wireless Wide Area Network (WWAN): Liscenced band for medical telemetry systems.
447. Xenobots: Programmable organisms designed by computers and assembled from living stem cells. They are an entirely new life form developed by researchers at the University of Vermont, Tufts University, and the Wyss Institute in order to learn more about how cells communicate – and eventually control it.
448. You: SW: The signal is coming from your tissue inside you. You are a node on a network since 1995. You are available to the internet and can be tracked and logged into like a computer with this system. You are accessible and commercially available to the enterprise level of Microsoft Open AI Azure Ingest and Subsume. We’re watching with headsets since 2007 on Cougar and SQL-Spark, the back end of WordPress. We can log into YOU with Qual-com, OMNeT, you are just seconds away.
Bonus Terms (Acronyms Coined by Webmaster to Describe “The Program”)
449. Remote Electronic Control, Torture, Euthanasia, Enslavement, Energy Harvesting, Transhumanism And SMART Under-The-Skin Surveillance System (RECTEEHTASUTSSS)
450: WRECT-SSTTEPs: Wireless Remote Electronic Civilian Targeting – Surveillance, Stalking, Torture, Termination & Experimentation Program(s)
451. JIWHHHHEEEP:* Jewish Institute for Wireless Hacking, Hunting, Hijacking, Harvesting & Electronic Enslaving & Euthanizing of People.
(First word in acronym can be Jewish, Zionist, British, American, AI, Nazi, and Illuminati, yielding pronunciations of Jiweep, Ziweep, Biweep, Iweep, Iweep, Niweep, and Iweep.)
452. WE MMUSSTTT ACCESS C-GOYS w/ LIES
Where acronyms stand for:
WE = Wireless (Body Area Network) Electronics
MMUSSTTT = Military-Medical Under-Skin Surveillance, Tracking, Torture, Transhumanism
ACCESS = AI Cryto Currency Enslavement Surveillance System
C-GOYS = Cyborgs w/ Graphene (-nanotech) Operating YourSelf
LIES = Logging Into Everybody’s Synthetic (biotech)
IV. Final Observations
A. Brief History of The Multi-Generational Transhuman Enslavement Project
I tend to credit most (but definitely not all) of Sabrina Wallace’s information as being correct, mainly because it comports well with and significantly extends the information I have independently compiled for this and my other websites. My research suggests that this present global technocratic enslavement-torture-murder system may be the direct descendant of the British-American eugenics movement and British and American Societies For Psychical Research (SPR) of the late 1800s. This same group (of British and American “New World Order slavemasters”) also created the Tavistock Institute in London (Chatham House), the Nazi mind-behavioral control experiments of World War II, the American-British Macy and Ratio Club Conferences of 1942-1953, and CIA-US military MKULTRA mind-behavioral control research and experiments from about 1950 to present.
Sabrina Wallace states that: “150 years ago they took away a body part” (the aura or human biofield). It may be no mere coincidence, then, that according to McClaughry’s Blog, the British and American Societies for Psychical Research placed primary importance on the study of psychic/paranormal (psionic) abilities some 140 years ago. The following timeline from McClaughry’s Blog reveals the truly strange interplay between science, politics, intelligence agencies, occult societies, the worship of Lucifer, and theurgy (the summoning of demons.) From Part IX of this series:
1882 – Society for Psychical Research (SPR) co-founded in London by Frederick Myer. It is being conducted under the thumb of the British spymaster family – the Cecil family. Balfour was a President of the SPR. The SPR was the first to examine paranormal phenomena in a scientific way. They investigated hypnotism, clairvoyance; telepathy; sensitives; mediums; ghosts and hauntings. They formed six research committees to investigate hypnotism and clairvoyance; telepathy; sensitives; mediums; ghosts and hauntings; and records and archives.
1884 – The American Society for Psychical Research (ASPR) is formed in Boston.
1887 – The British Society for Psychical Research sent Richard Hodgson to oversee the American Society for Psychical Research. The ASPR is also under the thumb of British intelligence.
1891 – Cecil Rhodes founds a secret society to bring the entire world under British rule. (It) is called the Round Table. Lord Balfour joins the Round Table. The British grand plan to rule the entire world has a name –the New World Order. The Brothers of Light international bankers, such as the Rothschilds, join the Round Table. Other international bankers, such as the Rockefellers, also join the Round Table. Scientology is under the New World Order people, it is their subject.
1897 – Sigmund Freud becomes a member of the Independent Order B’nai B’rith. It is a Brothers of Light lodge, practicing that Brothers of Light religion. Freud is one of the Brothers of Light. (According to Wikipedia: B’nai B’rith International (English pronunciation: from Hebrew: בני ברית b’né brit, “Children of the Covenant“), is the oldest Jewish service organization in the world. B’nai B’rith is committed to the security and continuity of the Jewish people and the State of Israel…) B’nai B’rith International was founded in 1843 in New York City by German Jewish immigrants. The widespread perception is that it is comprised of an exclusionary “German Jewish elite.”
(Webmaster’s Note: McClaughry refers to the “Brothers of Light” throughout his timeline. He identifies this group as an international Luciferian organization that traces back to the Nesilim, an ancient warring people from the Middle East, whose beliefs and m.o. form the core of various groups, including Judaism, Masonry, Rosicrucianism, OTO, Scientology, etc.)
1903 – This new British intelligence section (MI5) is formed in the same year that Frederick Myers published the findings of the Society for Psychical Research and their investigations into mental and spiritual phenomena – 1903. British intelligence is an arm of the New World Order people – the modern slavemasters. Through its covert agents, who carry out covert British propaganda operations, they seek to accomplish behavior modification under the euphemistic term “social engineering”.
1904 – James Hyslop formed the American Institute for Scientific Research. James Hyslop (a British MI5 agent) had formed the American Institute for Scientific Research to serve as part of William Melville’s foreign intelligence operations.
1905 – James Hyslop takes over as President of ASPR and moves it from Boston to New York. Hyslop puts the ASPR under the psychical research branch of his newly formed American Institute for Scientific Research (AISR), calling it Section B. The AISR was one of many front groups of British Intelligence, particularly the newly formed MI5 division under William Melville. Naming the ASPR SECTION B was a direct delineation of its status as an intelligence operation.
James Hyslop, through the Abnormal Psychology branch of his American Institute for Scientific Research, did an in-depth study of schizophrenics and he came to the conclusion that it was an infestation of spirits, or spirit possession.
This is the exact same theory that was pronouncedly reiterated in a British-backed book, The Oahspe. Thus we see that the Brothers of Light idea of the existence of numerous evil demons inhabiting any given human body – was deeply embedded in the accepted ideas of the British SPR and the American SPR. These people are the initial Scientologists. And they had determined that demons were the cause of schizophrenia.
1909 – James Hyslop resurrects the American Society for Psychical Research as a now independent organization.
The origin of the mental hygiene movement can be attributed to Clifford Beers in the United States. In 1908 he published A Mind That Found Itself; An Autobiography, a book based on his personal experience of admissions to three mental hospitals. The book… resulted in creation of the National Committee for Mental Hygiene in 1909. The committee’s chief concern was to humanize care of the insane: to eradicate the abuses, brutalities and neglect from which the mentally ill have traditionally suffered. The New World Order psychiatrists could not allow that to happen! To eradicate the abuse of mental patients would undermine their whole agenda to use torture to break a person so that he became obedient and docile. So, the New World Order men had to take over the mental hygiene movement.
Thomas W. Salmon, a British agent, takes over the National Committee for Mental Hygiene. So, right from the start, the National Committee for Mental Hygiene was commandeered and controlled into a specific direction. It immediately became an organization that was concerned with society, not with patients in mental institutions.
1910 – James Hyslop, through the Abnormal Psychology branch of his American Golden Dawn, member, Arthur Edward Waite, translated Dogma and Ritual of High Magic into English – he titled it Transcendental Magic, its Doctrine and Ritual.
The Seal of Solomon was on the front cover of the book. In Ritual Magick, the Seal of Solomon represents Divine Union, being composed of a female, watery triangle, and a male, fiery triangle.
The Key of Solomon, is a medieval book on magic originally attributed to King Solomon. A grimoire is a textbook of magic, giving instructions for invoking angels or demons, and gaining magical powers. Such books contain lists of angels and demons, directions on casting charms and spells and summoning unearthly entities. It is said that King Solomon evoked seventy-two demons and confined them in a bronze vessel sealed by magic symbols, and he obliged them to work for him. The Key of Solomon contains conjurations, invocations and curses to summon and constrain spirits of the dead and demons, forcing them to do the operator’s will. It also describes how to become invisible, gain favor and love, to cause harm to others, etc.
The Lesser Key of Solomon is an anonymous 17th century grimoire. It is one of the most popular books of demonology. It contains descriptions of the spirits and the conjurations needed to invoke and oblige them to do the will of the conjurer. The first section is Ars Goetia (Art of Goetia), contains descriptions of the seventy-two demons that Solomon is said to have evoked and confined in a bronze vessel, sealed by magic symbols, and that he obliged to work for him. It gives instructions on constructing a similar bronze vessel, and using the proper magic formulae to call up those demons. The Ars Goetia gives the demons “signs they have to pay allegiance to”.
The circle and triangle, used in the summoning of the 72 demon spirits of the Goetia. The magician stands within the circle and the spirit was believed to appear within the triangle.
The Goetia The Lesser Key of Solomon the King is a 1904 translation of the text by Samuel Mathers and Aleister Crowley. It is a manual that purports to give instructions for summoning 72 different demon spirits. 6 Thus we see what kind of magic Aleister Crowley was practicing – summoning demons. Later in time, L. Ron Hubbard (founder of Scientology) joins a Crowley cult where he also practices demon magic.
1911 – Sigmund Freud joined the Society for Psychical Research (SPR) in London.
1911 – L. Ron Hubbard was born. He is the son of United States naval commander Harry Ross Hubbard and Ledora May Hubbard. A friend of Ron’s father was US Navy Commander Joseph “Snake” Thompson. All the basic mental, spiritual, and religious ideas found in Dianetics and Scientology were developed by members of the SPR before L. Ron Hubbard was even born. That includes the therapy used.
By 1912, the Rockefeller Foundation had funded Thomas W. Salmon to be the first medical director of the National Committee for Mental Hygiene, the transformation and perversion of its original goals was now well underway.
1914 – 1919. World War I.
Aleister Crowley was a member of the Hermetic Order of the Golden Dawn, a Brothers of Light sect. Crowley worshipped Lucifer and practiced magic, by summoning demons. Crowley worked for British intelligence –MI 6 – during WW I and the 1920s and 1930s spying on Germans with occult interests.
Final Thoughts from Sabrina Wallace, Dr. Rauni Kilde and Dr. Eric Karlstrom:
Sabina Wallace: “Who’s doing all this? Your Medical, Sheriff, Police, Lawfare, Main Military, Para-military, Black Projects Military, Geo-Spatial and Silicon Valley with NetCentric Warfare and Mosaic Warfare, with Cognitive Technology Threat Warning System (CT2WS) using a headset and an EEG to watch you through your veins and arteries anytime, anywhere in the world with Sensors Open System Architecture (SOSA) on the Global Information Grid (GIG). So if someone tells you that the aura isn’t real, just laugh at them and say: “It is to ISR (Information, Surveillance, and Reconnaissance), the biggest companies in the world, Boeing, Ratheon and the rest of them. Check the market on directed energy weapons into 2030 and 2040.”
Dr. Rauni Kilde (author of “Bright Light on Black Shadows”): “This (weapons-control system) is the most important policy of the US government.”
Webmaster: The United States of America is a slave state tyranny run by the New World Order Slave masters.
B. Thoughts On Sabrina Wallace’s Credibility
Critical discernment is always required in order to try to validate testimony of others, especially regarding these topics. So we must ask: Is Sabrina Wallace “for real?” Is she acting? Is she piloted by others? Is she just “snowing” and misdirecting us with complex terms? Might she be radically over-exaggerating the capabilities and extent of the wireless body area network (WBAN) system? Critical discernment is required, especially in light of the tremendous number of military-intelligence agentur and their private sector cutouts (cyber stalkers and trolls) who pose as experts and produce podcasts in an attempt to grab center stage, control “the narrative,” and misdirect the public away from the truth. IIA, Interactive Internet Activities, for example, are extraordinarily well-funded DoD disinformation operations led by retired generals and ex-CIA officials. Alas, the Pentagon itself has a budget of about $4 billion/year to propagandize/fool the public with these kinds of operations.
My (still relatively minor) concerns along these lines include the following:
1) In her videos, Sabrina does not refer to any of the many, many authors and experts that I have studied and which I cite on this website. She appeared on the video podcast scene a year and a half ago and makes the claim that she and she alone has the truth. Hmmm. She never refers to my website which I have compiled since 2016 and which now has some 2300 posts. She never mentions the important research and output of brilliant, brave TI’s such as Dr. Rauni Kilde, Gloria Naylor, Rene Pittman, Cheryl Welsh, Mark M. Rich, Stephen O’Keefe, Dr. Allen Barker, Kay Griggs, Harlan Girard, Robert Naeslund, Suzie Dawson, and many others, which are centrally featured on this website.
Rather, she solely refers to her own research and a very small circle of other podcasters, including Toresays, Karen Kingston, Celeste Solum, Alex Jones, and Mike Adams and to a relatively small number of individuals who watch and comment on her podcasts. (While she praises and adores ToreSays and praises Celeste Solum, she refers to Jones and Adams as “butt-fuckers,” and accuses them and Karen Kingston as being “liars on the take” who are complicit in this system and thus, deliberately misleading everyone.)
2) She makes rather extraordinary claims about having met God, nephilim, Jesus Christ, and two 1800-year old Rockefellers when she was a 4-year old victim/nonconsensual experimentee in DoD black projects.
3) She alternately appears as well-dressed, lucid, and rational in some videos and without a shirt, ranting and raving, smoking a cigarette, and appearing to act in a most animated manner in others. While she is generally quite engaging and well spoken, she sometimes sounds, looks, and acts a bit crazy, especially when she does her biofield enhancing exercises.
4) She mispronounces relatively simple words like “hierarchy” and “spectroscopy” and perhaps tellingly, “Giordano,” the last name of DARPA/Georgetown University’s neuroscientist and weaponologist. This caught my attention based on the fact that she rattles off much more complex terms, rapid-fire, with ease.
5) Again, she often refers to her friend and fellow podcaster, ToreSays, as one who is spreading profound truths that could save us all. By contrast, my impression is that ToreSays is a fraud, an intelligence agent and cyber-stalker, playing the role of truth teller. (This is a commonplace phenomenon as noted in #1 above.) I certainly wonder at the self-referencing, alternative world (metaverse) that fake TI/podcasters have created for themselves and each other.
6) In one of her videos in which she discusses her family background, she mentions that both her parents were involved in black projects and that her family has “Cosmic Clearances.” She also claims to be a descendant of Eliphas Levi (1810-1875), the French “father of modern occultism,” kabbalist magician, and creator of the Baphomet image that has become a common icon of Satan. In one video in which she was demonstrating her “human biofield exercises,” I noticed she briefly flashed the horned devil sign with one of her hands. In another video, she briefly showed one of her notebooks which had a Pentagram on its cover. Coincidence? She mentions her descent from a relative with the last name B-a-u-r, which she spells out. Of course, Amshel Mayer Baur is the man who changed his last name to Rothschild, thereby founding perhaps the wealthiest and most satanic jewish dynasty ever as well as the Bavarian Illuminati!!!!!.
Is Sabrina an occultist? She claims to be a believer in Jesus Christ (incidentally, as do the celebrated podcasters she references, Alex Jones, Mike Adams, Celeste Solum, and Karen Kingston) but distains Christians for their ignorance and intransigence. By contrast, she supports and validates the work of “distance healers” and other energy workers.
7) Sabrina claims to be “augmented” which could mean a number of things. Is she mind controlled? Is she somehow hived in to other minds? I don’t know.
However, so many of her claims seem worthy of further investigation that I thought it worthwhile to compile this list of specialized terms/jargon applicable to these complex topics.
Dr. Eric Karlstrom, Emeritus Professor of Geography, CSUS, Oct. 20, 2023

Comments (0)